Deployments
Ivanti Policy Secure(IPS) supports two types of cluster deployments:
- Deployment of Active/Active Cluster
- Deployment of Active/Passive Cluster
Requirements and Limitations
The following are the requirements and limitations for clustering:
- Cluster members must run the same software version.
- Cluster members must use the same hardware platform.
- State synchronization must occur only through the internal Network Interface Card (NIC). Ensure the cluster communication and resource access must take place over an internal network.
- You can deploy active/active or active/passive clustering only within the same IP subnet.
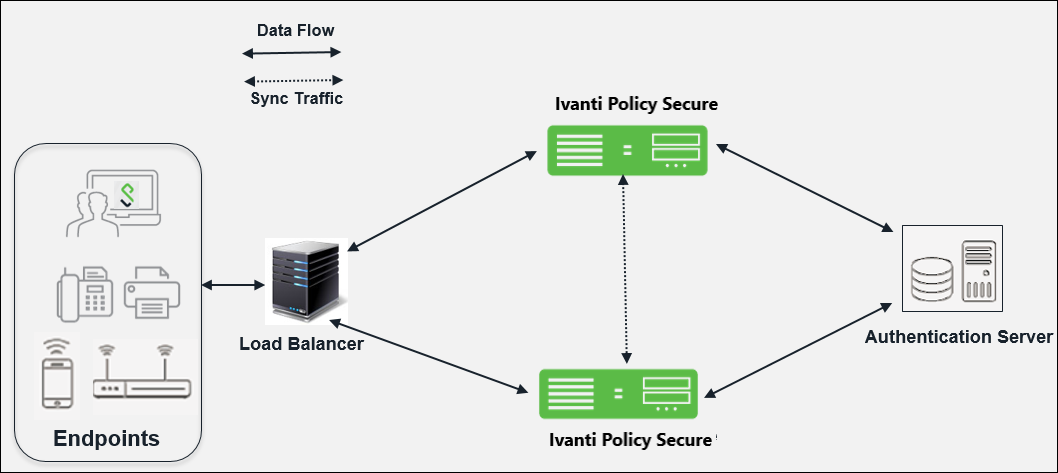
Deployment of Active/Active Cluster
An Active/Active deployment provides load balancing and high availability. IPS relies on an external load balancer for distributing the load among IPS nodes. Active/Active cluster configuration allows increased aggregate system throughput; however, it does not provide increased scalability beyond the total licensed users. It also provides seamless failover, which is achieved by state synchronization between the devices.
If a node goes offline, the load balancer adjusts the load on the active nodes. Users do not need to sign in again, however some session information entered a few seconds before the active machine went offline, such as cookies and passwords, may not have been synchronized on the current device, in which case users may need to sign in again.
Only 2 node A/A Cluster is qualified with IPS.
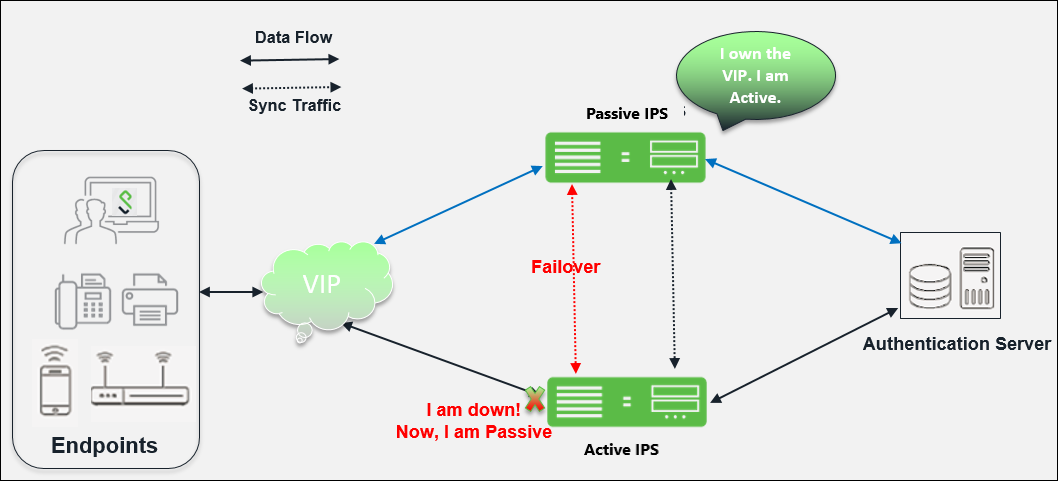
Deployment of Active/Passive Cluster
An active/passive cluster configuration provides high availability. Active/Passive deployment allows seamless failover without the need to set up any external equipment. The states are synchronized between the two devices for all the configurations so that the devices are virtually identical.
Active/Passive clustering is supported only if the members of the cluster pair are in the same subnet because the VIP address must be shared by both the members. IPS uses a virtual IP (VIP) address to address the cluster pair in addition to addressing each device. The IP address takeover (IPAT) approach is used for the VIP address. If the active node fails, the passive node takes over the VIP address and sends a gratuitous Address Resolution Protocol (ARP) message notifying other networking devices that it now owns the VIP address. You should check that other devices in your network, especially the next-hop gateways, will consider the gratuitous ARP messages.