Example Configuration: Guest Access with Juniper Mist WLC
This section describes the configuration that is required on IPS to communicate with Juniper Mist WLC for Guest wireless authentication.
To configure IPS for guest wireless authentication:
- Select Authentication > Auth.Servers. The Authentication Servers screen appears. Use the Default Guest Wired Authentication Server.
- Click Guest Wired Authentication available by default to view the settings.
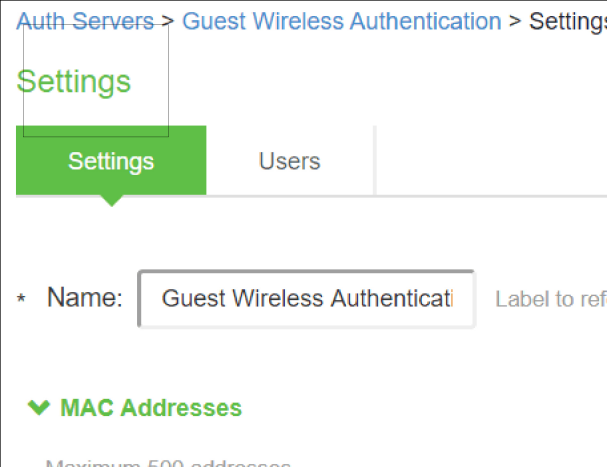
- You can make the necessary changes and click Save Changes.
- Select Users > User Roles. The User Roles page appears.
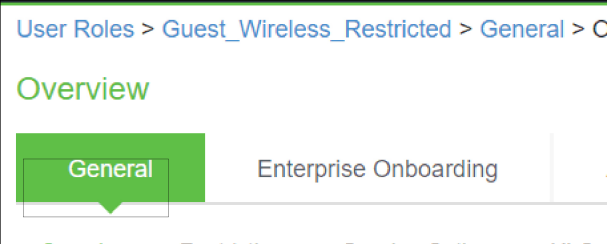
- Click Guest Wired Restricted user role available by default. The Agentless access is enabled for this role.
- Select Endpoint Policy > MAC Address Authentication Realms and click Guest Wired authentication realm available by default.

- Select Endpoint Policy > Network Access > Location Group. Select Guest Wired as MAC Auth Realm.
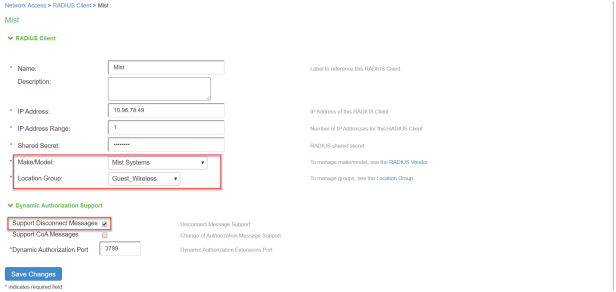
- Configure the Mist WLC as a RADIUS client. Ensure that the Guest Wired location group and Support Disconnect Messages options are enabled.
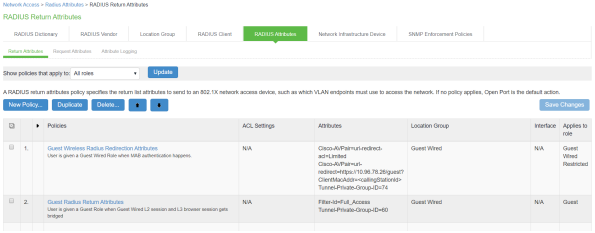
- Configure the RADIUS return attributes for Guest Wired policy. Select Endpoint Policy > Network Access > RADIUS Return Attribute Policies. Click New Policy. Under RADIUS Attributes tab, select the check box for Return Attribute.The RADIUS return attributes are required for MAB authentication initially when the guest connects to the SSID (where the redirection happens) and then the session is bridged after the guest authenticates.
Supported Attributes: Filter-Id, Airspace-ACL-Name, Aruba-User-Role.
Cisco-AVPair is supported to set the redirection URL.
Tunnel-Private-Group-ID and Airespace-Interface-Name are used to assign the VLANS.
Configuring Mist WLC
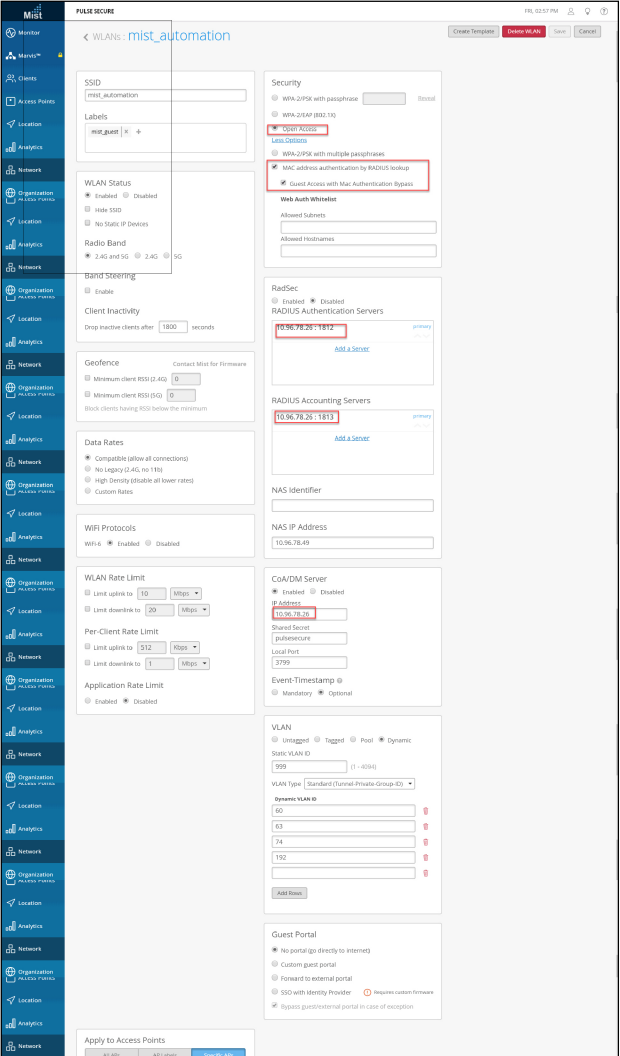
To configure WLAN on Mist:
- Add Mist as Access Point.
- Setup the Wireless Networks, Select Network > WLANs. Click Add WLAN.
- Configure Name, SSID.
- Under Security, select Open Access.
- Enable Guest Access with Mac Authentication Bypass.
- Under RADIUS Authentication Server and RADIUS Accounting Server, specify the IPS IP address.
- Create Security Policy to control resource access.
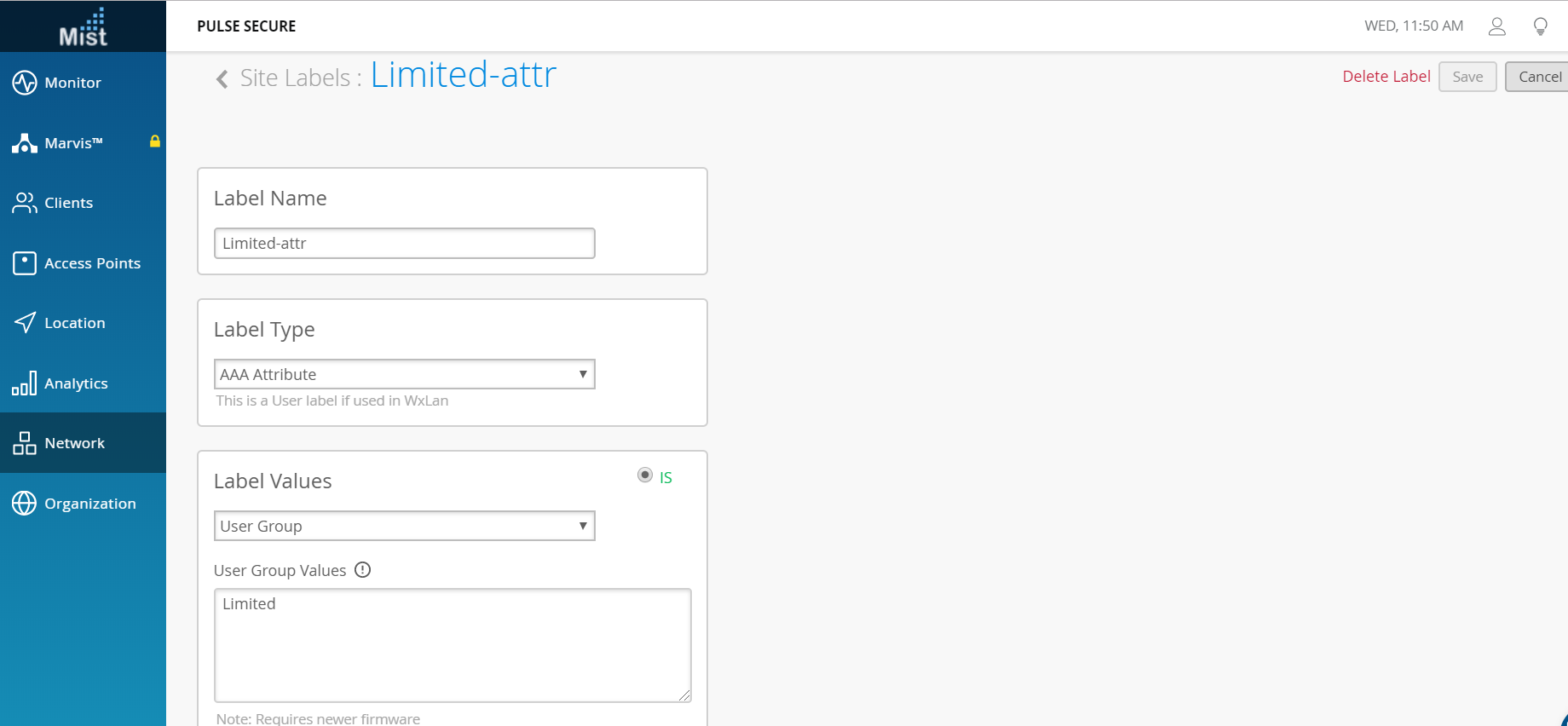
- You can also issue a label. The label is used to form tags or groups, which can be used to create security policies.