Network Device Administration using TACACS+
Overview
The network device administrators are required to configure and maintain the network devices such as switches, wireless access points, routers, and gateways. IPS supports configuring and coordinating the network devices through IPS Admin UI.
The administrator implements policies to determine who can login to a network device console, telnet session, secure shell (SSH) session to manage each device, what level of privilege do they have, what operations they can run (that is, the commands the admin user is permitted to run on the device) and also audit all the actions taken.
Managing these policies separately on each device is not just unmanageable but can lead to security incidents or errors that result in loss of service and network downtime due to undesired access. Most compliance requirements and security standards require using standardized tools to centralize authentication for administrative management.
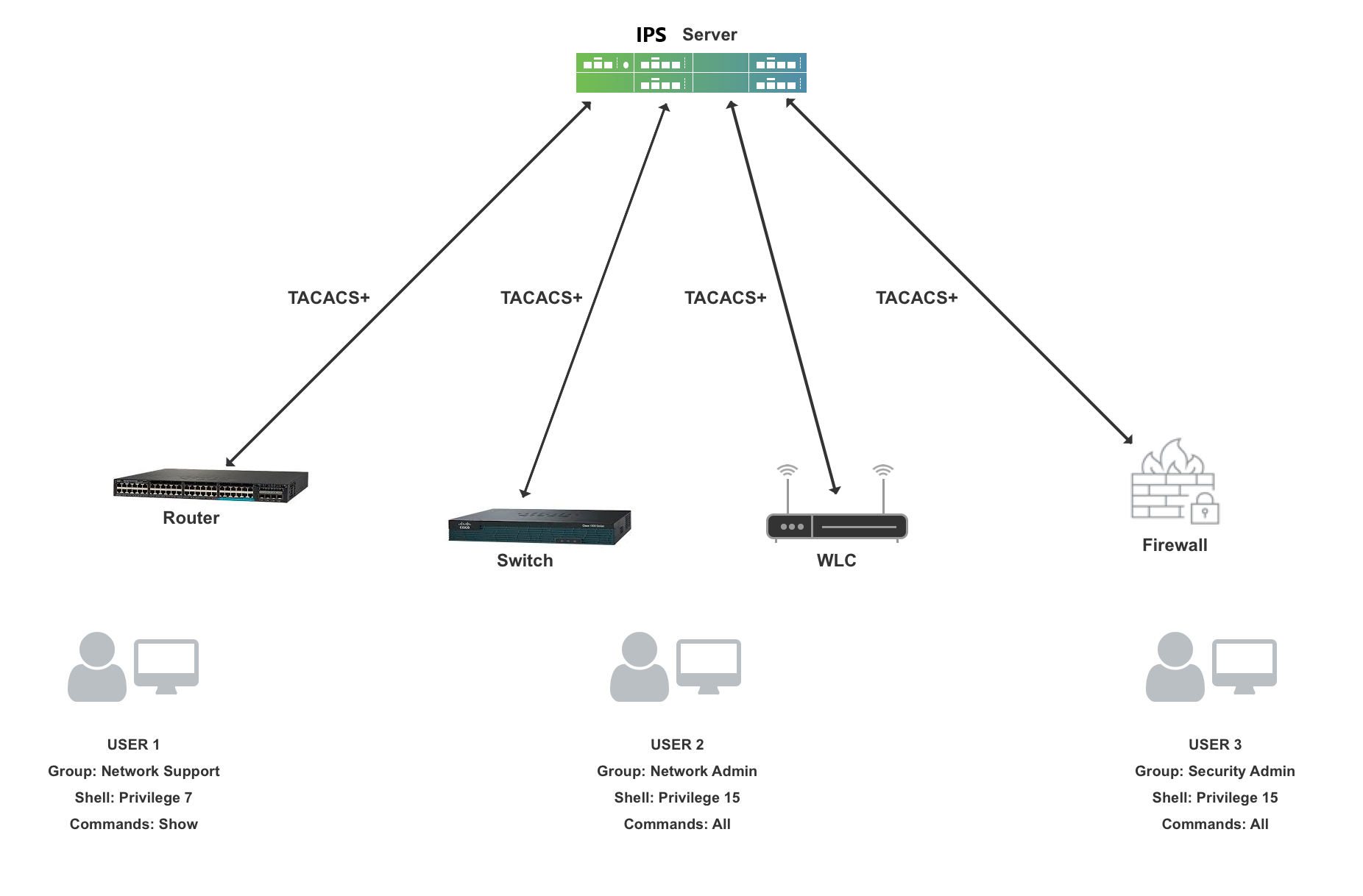
The above deployment consists of 3 types of administrators:
- User1 - This admin belongs to Network Support Group and can only access show commands on router, switches and access points. The admin has no access to Firewall.
- User2 - This admin belongs to Network Admin Group and can access all commands on routes, switches and access points. The admin has no access to Firewall.
- User3- This admin belongs to Security admin group and an firewall administrator and does not have access to routers, switches and access points.
A large company will have many devices from different vendors. It requires administrators to manage the network with many hierarchical levels.
Without a centralized server for administration, every time a new device is deployed, several admin accounts needs to be created on the new device to assign the required privilege for each of the admin. Similarly, if a new admin onboards an functional organization, the account needs to be created on thousands of devices.
With Ivanti Policy Secure(IPS) acting as a centralized server for device administration using TACACS+, a new admin can just be mapped to required group. A new Admin account can be configured either locally on IPS or any external servers such as AD, LDAP and so on. Similarly, when a new device is purchased, the only configuration is configuring IPS as a centralized server for device administration on device.
Licensing
TACACS+ user login does not consume any user license however either POLSEC license or Profiler license is required to be installed.
Authentication
Provides complete control of authentication through login and password.
Authorization
Provides fine-grained control over user capabilities for the duration of the user's session, which includes idle time-out, session duration. You can enforce restrictions on what commands a user may execute by configuring the privilege level for administrators. Within the privilege-level, further control can be forced by specifying command or regex match.
Ivanti Policy Secure(IPS) supports 2 types of authorization techniques for administrators:
- Exec authorization- This determines a user’s privilege level when they are authenticated. The admins can run the commands, which are allowed in the user’s privilege level.
- Command authorization- TACACS+ command authorization provides centralized control of the commands available to IPS admin user. In this, every command is sent to IPS for authorization and command is permitted after getting authorized by IPS.
- A Telnet, SSH, or console interface user who is previously authenticated by IPS using TACACS+ enters a command on the device.
- The network device looks at its configuration to see if the command is at a privilege level that requires TACACS+ command authorization.
- If the command requires authorization, the device consults the IPS to see if the user is authorized to use the command.
- If the user is authorized to use the command, the command is executed.
Accounting
Collects and sends information used for auditing to the TACACS+ server. Network device administrators can use the accounting facility to track user activity for a security audit or to provide information for user billing. Accounting records include user identities, start and stop, executed commands.