JITC Mode Option
To enable the Joint Interoperability Test Command (JITC) mode:
- Select System > Configuration > Security > Inbound SSL Options.
- Under DOD certification option, enable Turn on JITC mode.
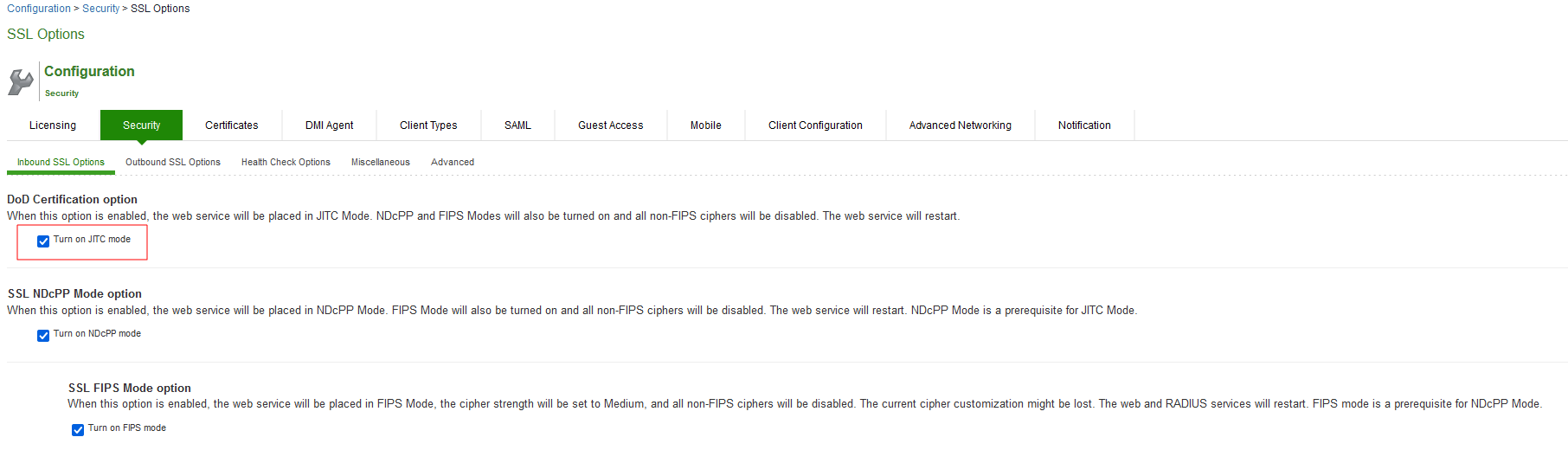
NDcPP and FIPS mode are automatically enabled after enabling the JITC mode.
- Click Save Changes.
- With JITC mode enabled, IPS detects any duplicate RADIUS Return and Request Attribute policies and an error message is displayed if the user tries to create a duplicate policy.
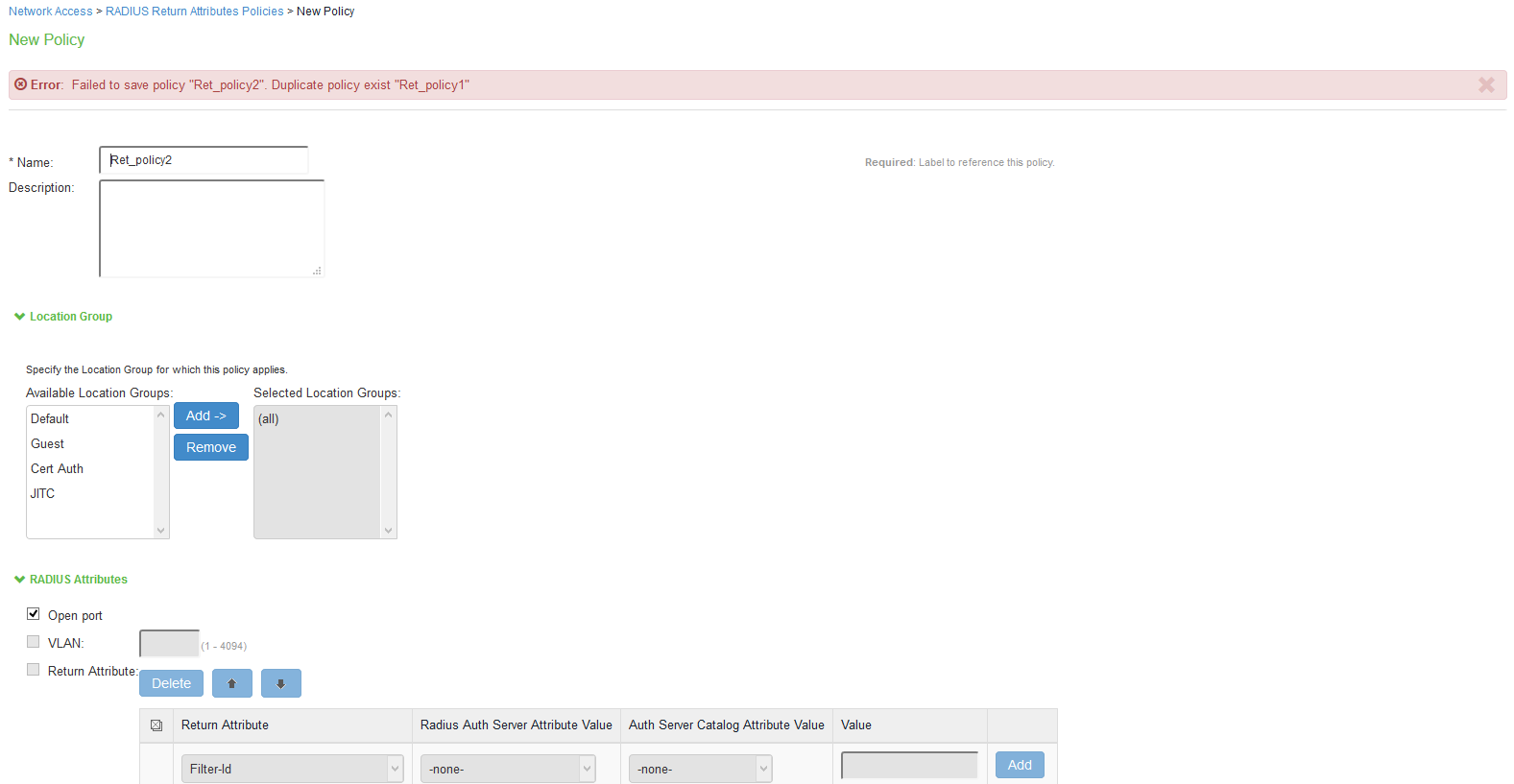
With JITC mode enabled, only the first match duplicate RADIUS policy found is reported in the error message.
Important Factors to Consider
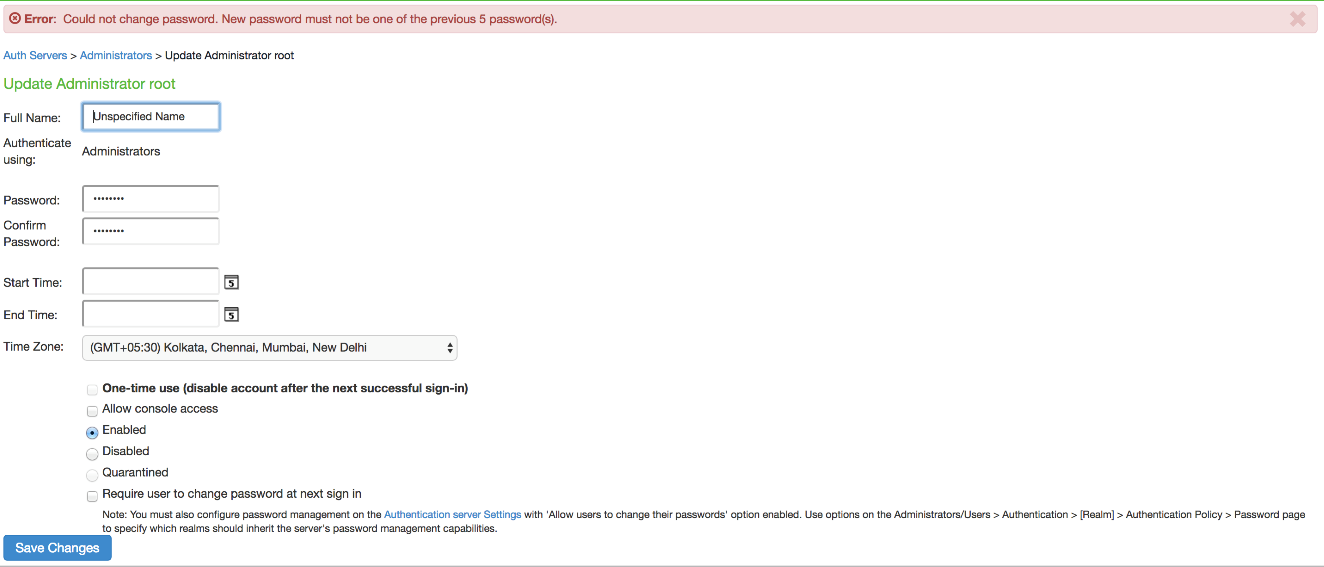
Password Strengthening: When JITC is enabled, IPS does not allow an administrator to configure a password exactly same as previously configured 5 passwords. An error message is displayed in this case.
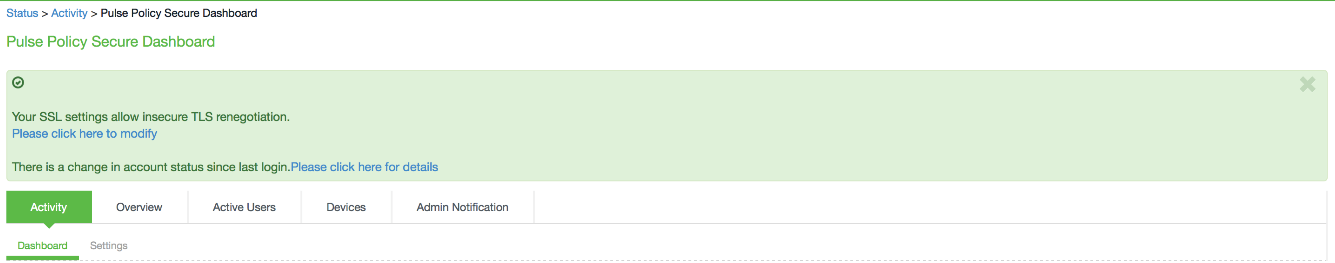
Notification for Unsuccessful Admin Login Attempts: With JITC Mode on, IPS shows a banner with the countof unsuccessful login attempts. This includes any change in the Admin status that would have happened since thelast successful login. Upon clicking on the banner, the Administrator is directed to the status page, which provides more details about status or configuration change since last login. These configuration changes are cleared before the next login so that admin can see different set of configuration changes, if anything happened from the last login.

Re-authentication of Admin Users: IPS will force the administrator to re-authenticate with IPS whenever the following conditions occur:
- Add Role
- Delete Role
- Modify the Role
- Delete the Realm
- Update the Realm
- During DPE (Dynamic Policy Evaluation)
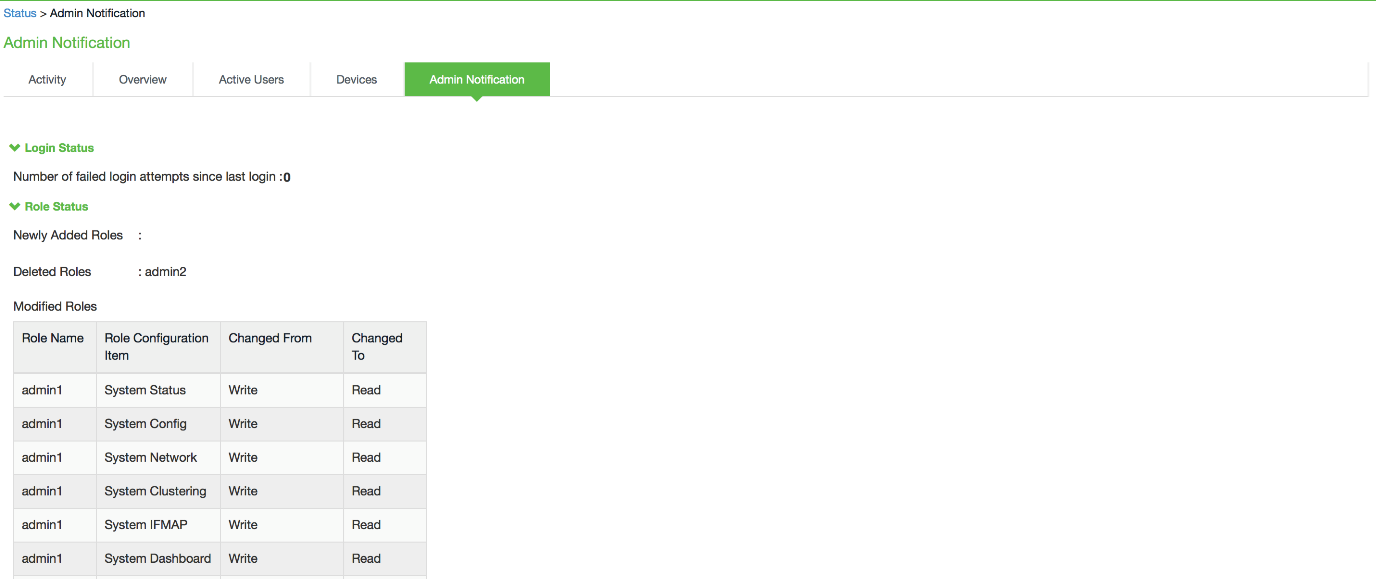
Configuration Change Notification: For details about configuration changes and status information since last login, go to System > Status >Admin Notification.
NDcPP Mode Option
NDcPP mode can be enabled in the Inbound tab with a checkbox. This status is also applied over to the Outbound tab. Turning on NDcPP automatically turns on FIPS mode and disables SSL/TLS Version TLS1.0 and below. Also, NDcPP Mode allows to choose only 16 Ciphers under Custom Encryption Strength. Turning on the NDcPP checkbox selects all the NDcPP ciphers by default on both, the Inbound and Outbound sides.
When the NDcPP Mode is enabled, backend server like Windows 2008 R2 which supports the SSL/TLS Version only till TLS1.0 cannot be connected.
syslog-ng server
Connection to syslog-ng server does NOT get established, since syslog-ng does not support TLSv1.1 and TLSv1.2.
rsyslog
Supports only till TLSv1.1. So, connection would not get established, if Outbound SSL Options is set to use TLSv1.2.
- To be NDcPP compliant, NTP Update Interval needs to be limited to 60 minutes. This is to avoid the potential drift becoming too excessive.
- For incoming client certificate during client certificate authentication and for incoming server certificate during backend syslog server connection 1024 bit Key Length is not allowed in both NDcPP and FIPS Mode where as SHA1 Signature Algorithm is not allowed only in FIPS Mode and is allowed in NDcPP Mode. This restriction is not applicable for Outgoing Certificates from IPS during SSL Negotiation.
Inbound Settings
When the NDcPP mode is enabled, the following settings appear by default in the Inbound SSL Options page:
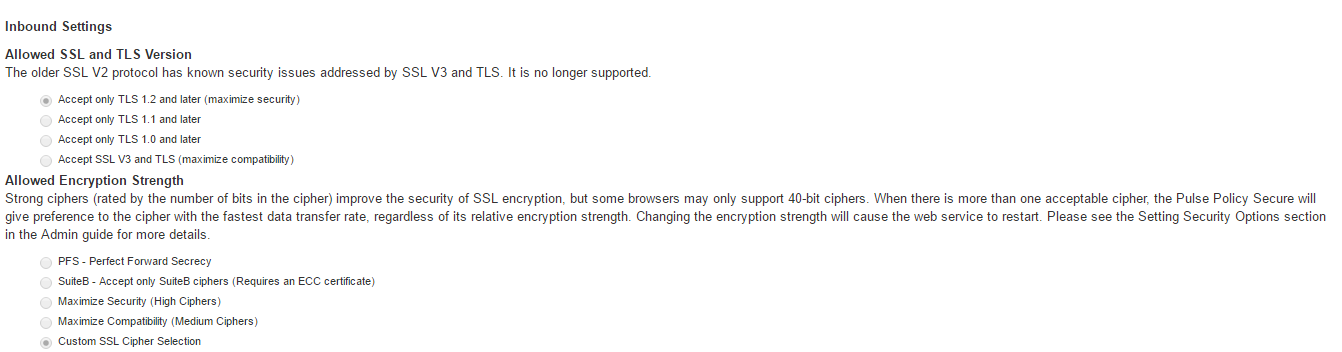
- The Accept only TLS 1.1 and later is enabled by default in the Allowed SSL and TLS Version settings. Only the Accept only TLS 1.1 and Accept only TLS 1.2 options can be chosen. The Accept only TLS 1.0 and later and the Accept SSL V3 and TLS (maximize compatibility) are disabled. See figure
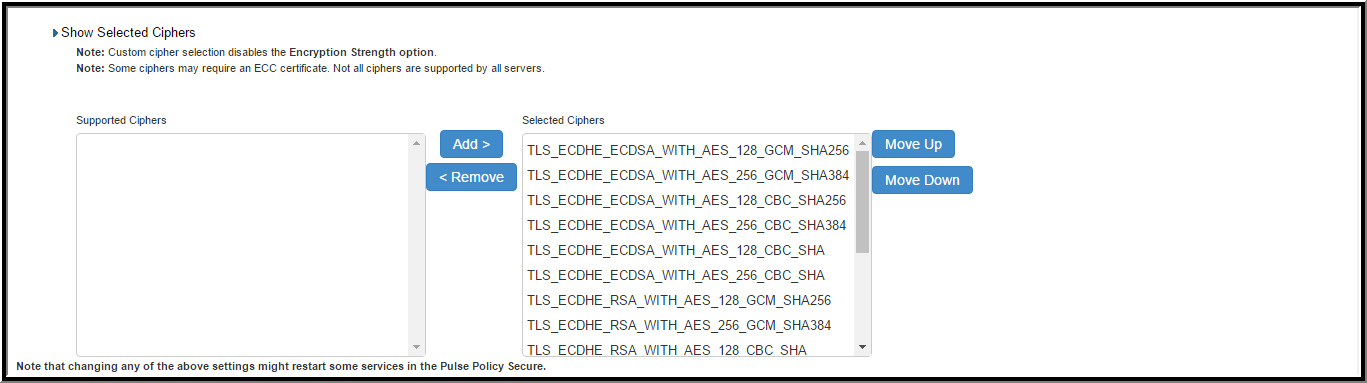
- With regards to the Allowed Encryption Strength settings the Custom SSL Cipher Selection is enabled by default with NDcPP Ciphers. All other options are disabled.
The following is a list of Selected Ciphers in the Inbound Settings with the NDcPP mode enabled:
- TLS_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_AES_256_CBC_SHA
- TLS_DHE_RSA_WITH_AES_128_CBC_SHA
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_256_CBC_ SHA256
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
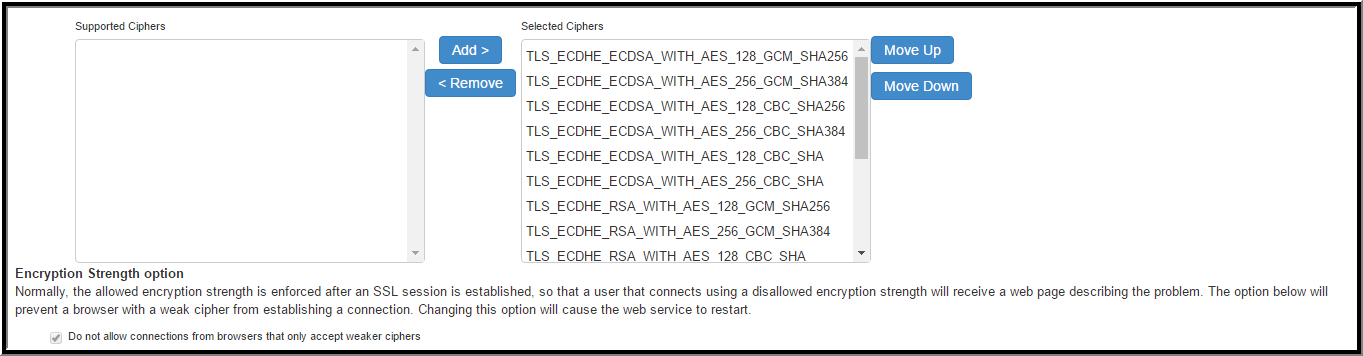
Outbound Settings
When the NDcPP mode is enabled, the following settings appear by default in the Outbound SSL Options page:
- The Accept only TLS 1.1 and later is enabled by default in the Allowed SSL and TLS Version settings. Only the Accept only TLS 1.1 and Accept only TLS 1.2 are editable. The Accept only TLS 1.0 and later and the Accept SSL V3 and TLS (maximize compatibility) are disabled.
- With regards to the Allowed Encryption Strength settings the Custom SSL Cipher Selection is enabled by default. All other options are disabled.
- Only the NDcPP ciphers configured in the Outbound SSL options settings are sent in the Outbound connections (IPS —> backend SSL).
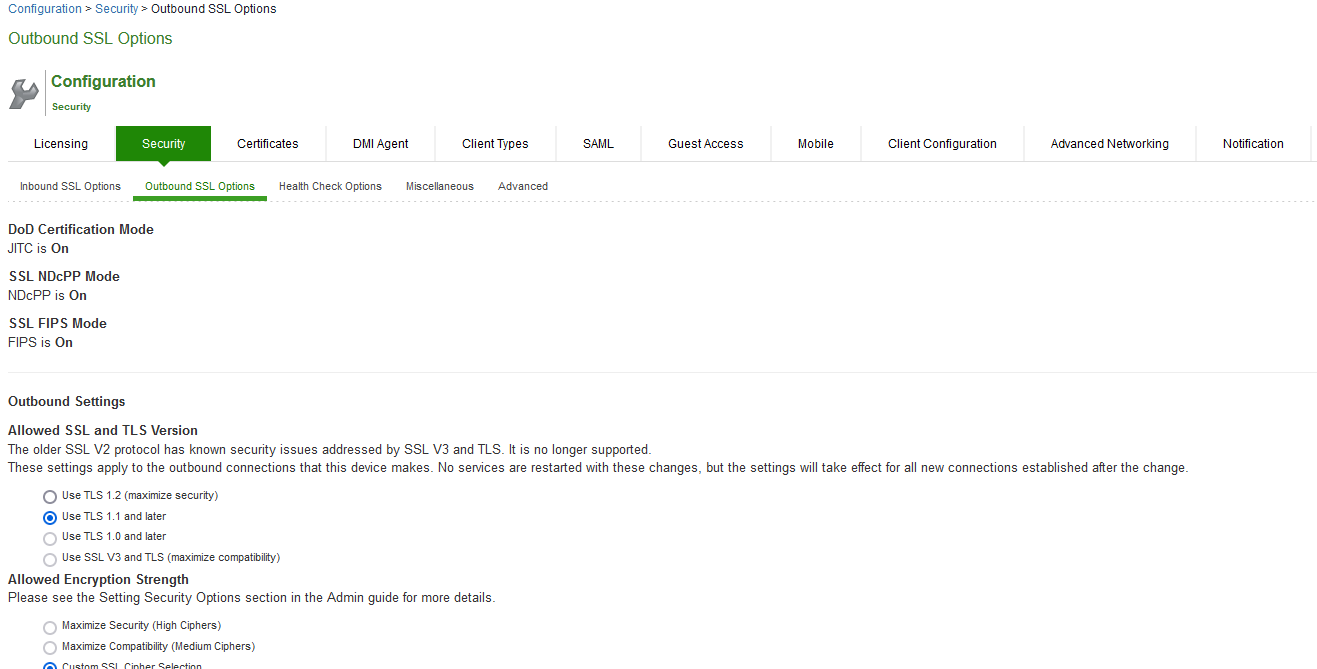
The following is a list of Selected Ciphers in the Outbound Settings with the NDcPP mode enabled:
- TLS_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_AES_256_CBC_SHA
- TLS_DHE_RSA_WITH_AES_128_CBC_SHA
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_256_CBC_ SHA256
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384