Using the Certificate Server
This topic describes integration with the certificate server.
Certificate Server Overview
This section describes support for using IPS with the certificate server.
Understanding the Certificate Server
The certificate server is a local server that allows user authentication based on the digital certificate presented by the user without any other user credentials.
When you use a certificate server, the user experience is similar to anonymous authentication. If the certificate is secured through a hardware or a software token or through a password, the certificate server authentication is very useful. The certificate contains the full distinguished name (DN) and the system extracts the values from the DN and uses it for role mapping rules, authentication policies, and role restrictions.
Feature Support
The Ivanti Policy Secure(IPS) access management framework supports the following certificate server features:
- Certificate directory services to retrieve user attributes in role mapping rules, authentication policies, and role restrictions.
- Load CA-created certificates on the system.
- Load multiple certificates from different CAs for use with different authentication realms.
Interoperability Requirements and Limitations
If you choose a certificate attribute with more than one value, the system uses the first matched value. For example, if you enter <certDN.OU> and the user has two values for the attribute (ou=management, ou=sales), the system uses the “management” value.
To use all values, add the SEP attribute to the variable. For example, if you enter <certDN.OUT SEP=”:”> the system uses “management:sales”.
Configuring Authentication with the Certificate Server
To configure authentication with the certificate server:
- Select Authentication > Auth. Servers.
- Select Certificate Server and click New Server to display the configuration page.
- Complete the configuration as described in table.
- Save the configuration.
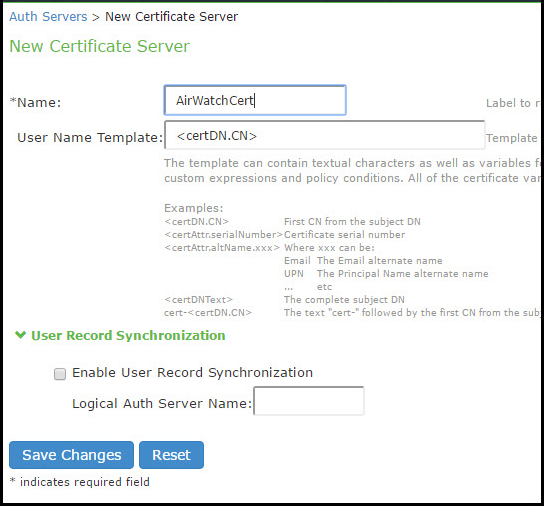
|
Settings |
Guidelines |
|---|---|
|
Name |
Specify a name to identify the server within the system. |
|
User Name Template |
Specify a username template. Specify how the system should construct a username. You may use any combination of certificate variables contained in angle brackets and plain text. This value populates the <USER> and <USERNAME> session variables for use throughout the rest of the system configuration. |
|
Logical Auth Server Name |
Specify a logical authentication server name. |
Displaying the User Accounts Table
To display user accounts:
- Select Authentication > Auth. Servers.
- Click the link for the authentication server you want to manage.
- Click the Users tab to display the user accounts table.
The user accounts table includes entries for the accounts that have been created. The Last Sign-in Statistic column shows the last successful sign-in date and time for each user, the user’s IP address, and the agent or browser type and version.
- Use the controls to search for users and manage user accounts:
- To search for a specific user, enter a username in the Show users named box and click Update.
You can use an asterisk (*) as a wildcard, where * represents any number of zero or more characters. For example, to search for all usernames that contain the letters jo, enter *jo*. The search is case-sensitive. To display the entire list of accounts again, type * or delete the field’s contents and click Update.
- To limit the number of users displayed on the page, enter a number in the Show N users box and click Update.
- To terminate the user session and delete the account, select the check box next to the user account record and click Delete.