Using the Compliance Report
This topic describes the compliance report.
Overview
The compliance report displays compliance status such as compliant, not compliant, remediated, not assessed information for each user based on the device activity in the selected time range.
To display the compliance report, select System > Reports > Compliance.
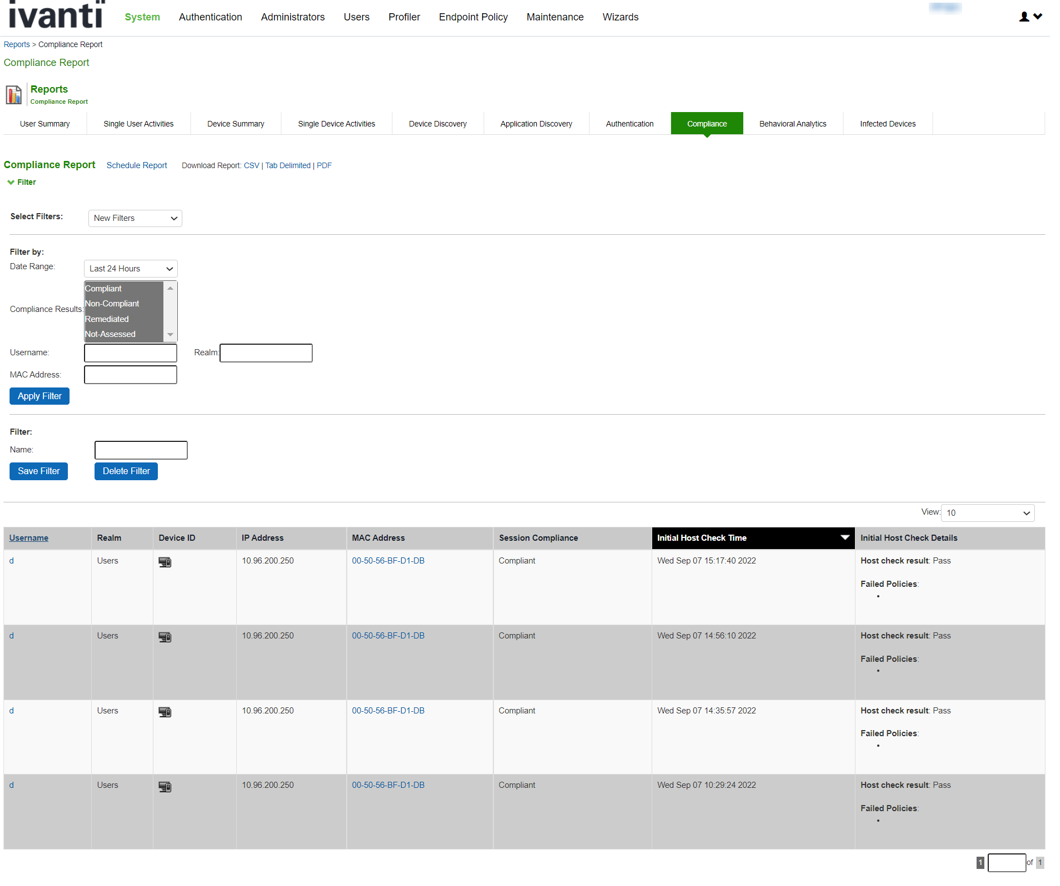
Table describes the different columns on the compliance report.
|
Column |
Description |
|---|---|
|
Username |
Specifies the name of the user. |
|
Realm |
Specifies the realm. |
|
Device ID |
Specifies a unique identifier used to identify an end point. Click the device ID icon to view a single device report. |
|
MAC Address |
Specifies the MAC address of the device. |
|
IP Address |
Specifies the IP address of the device |
|
Session Compliance |
Specifies the Host Checker posture assessment results: Compliant, Not Compliant, Not Assessed, or Remediated. |
|
Initial Host Check Time |
Specifies the initial host check time. |
|
Initial Host Check Details |
Specifies the host check result. |
The posture assessment chart is also a part of compliance report. It is displayed based on Initial Host Checker evaluation details (Login time).
Table lists the type and the failure reasons for Host Checker.
|
Type |
Failure Reason |
|---|---|
|
Antivirus |
Anti-virus not installed Anti-virus not running Anti-virus not up to date Anti-virus scan time check failed |
|
Firewall |
Firewall not installed Firewall not running |
|
Antimalware |
Anti-malware not installed |
|
Antispyware |
Anti-spyware not installed Anti-spyware not running |
|
OS Checks |
Unsupported OS |
|
Port |
Restricted ports open Required ports not open |
|
Process |
Detected restricted processes Required processes not detected |
|
File |
Detected restricted files Required files missing |
|
Registry |
Incorrect registry settings |
|
NetBIOS |
Detected restricted NetBIOS names Required NetBIOS names not found |
|
MAC Address |
Detected restricted MAC address Required MAC address not present |
|
Machine Certificate |
Certificate missing |
|
Patch Assessment |
Patches missing |
|
Remote IMV |
Remote IMV failure |
|
3rd party |
NA (Not considered for reporting) |
|
3rd party sub policy |
3rd party sub policy failed |
|
Rooting Detection |
Detected rooted devices |
|
Jail Breaking Detection |
Detected jail broken devices |
|
3rd party NHC Check |
Generic failure |
|
Type |
Failure Reason |
|---|---|
|
Statement of Health |
Generic failure |
|
Connection Control |
Generic failure |
|
HC |
HDEncryption software not installed Detected Unencrypted drives Drives are missing Unsupported client for HDEncryption check Patch Management software not installed Detected missing patches Unsupported client for PatchMgmt check Deprecated patch assessment rule |
Creating a new Filter
To create a new filter:
- Select System > Reports > User Summary.
- Under Filter, enter the name of the filter.
- Under Filter by: Select one of the following periods from the Date Range list box:
- Last 24 Hours– (Default) Refers to the last 24 hours from the current hour.
- Last 7 Days– Refers to current day and the previous last 6 days.
- Last 30 Days– Refers to current day and the previous last 29 days.
- Custom– Enter the custom from and till date range.
- Enter search criteria in one or more of the following attribute columns:
- Compliance Results
- Username
- Realm
- MAC Address
- Click Save Filter.
Once the filter is created, it gets listed in the filter drop-down. Administrator can also choose to edit the existing filter to customize the report based on the requirement. The filter can also be deleted using the Delete Filter option.
Applying Data Filters
To apply a data filter:
- Select System > Reports > Compliance.
- Select one of the following periods from the Filter by: Date Range list box:
- Last 24 Hours– (Default) Refers to the last 24 hours from the current hour.
- Last 7 Days– Refers to current day and the previous last 6 days.
- Last 30 Days– Refers to current day and the previous last 29 days.
- Custom– Enter the custom from and till date range.
- Enter search criteria in one or more of the following columns:
- Compliance Results
- Username
- Realm
- MAC Address
- Click Apply Filter.
Sorting Records
The data source determines the default sort order of the data rows in the report. Typically, data appears randomly, so sorting is an important task in creating a useful report. You can sort single data column.
To sort the compliance report:
- Select System > Reports > Compliance.
- Select Initial Host Check Time or Username column and click either the ascending or descending order icon.
Exporting Compliance Report
To export a compliance report:
- Select System > Reports > Compliance.
- Select a Download Report option.
- CSV– Exports the report in CSV format.
- Tab Delimited– Exports the report in tab-delimited format.
- PDF– Exports the report in PDF format.