Configuring Check Point Next-Generation Firewall
Check Point firewall detects traffic from an endpoint that matches a configured security policy using the access roles. It determines the role(s) associated with that user, and allows or denies the traffic based on the actions configured in the security policy.
The network interfaces are configured on the Check Point Next-Generation firewall and the remaining configurations are done on the Check Point Smart Console.
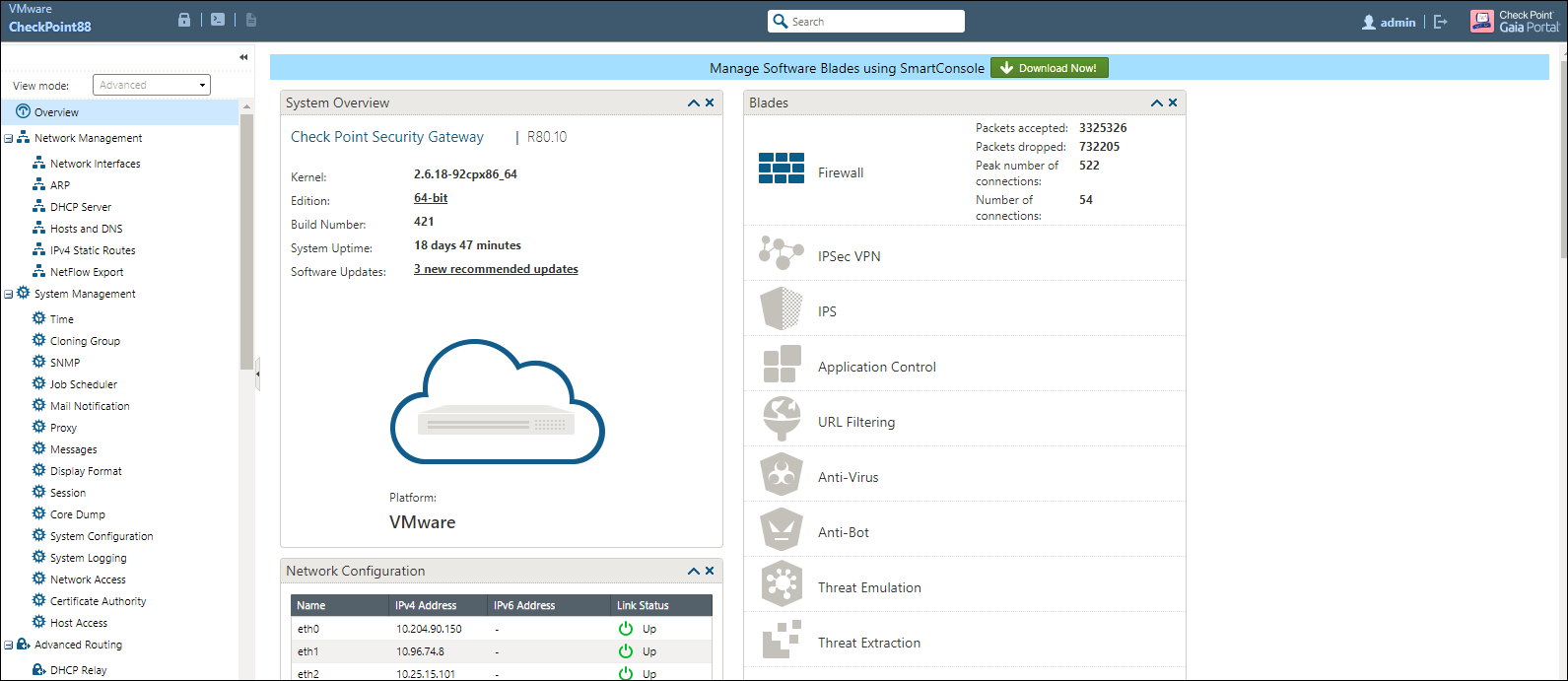
Configuring Identity Awareness in SmartConsole
The Identity Awareness lets you easily configure network access and auditing based on network location, identity of user, and identity of the device. When Identity Awareness identifies a source or destination, it shows the IP address of the user or computer with a name. For example, this lets you create firewall rules with any of these properties. You can define a firewall rule for specific users when they send traffic from specific computers or a firewall rule for a specific user regardless of which computer they send traffic from.
To enable Identity awareness:
- Login to the Check Point SmartConsole.
- From the Security & Gateways view, double-click the Security Gateway on which to enable identity awareness.
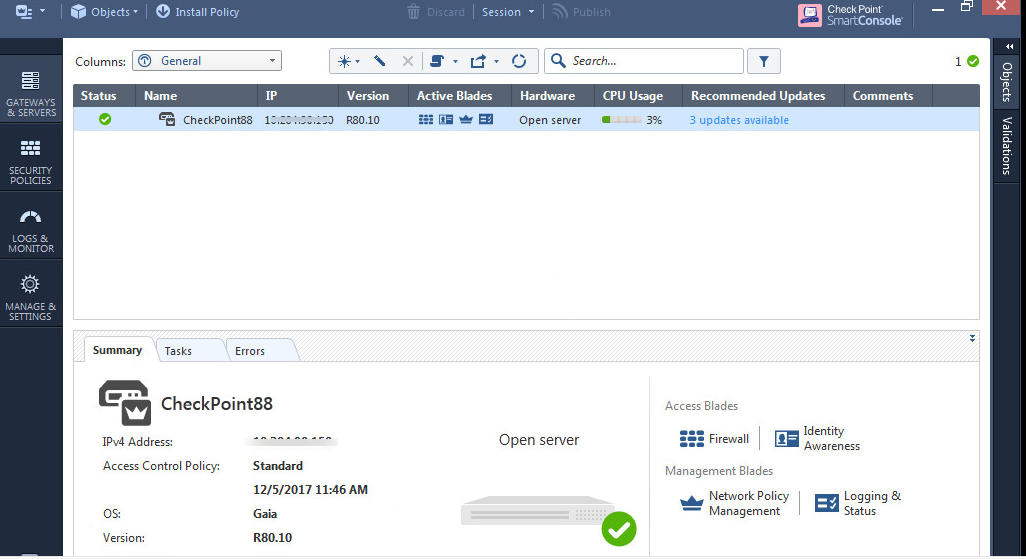
- Create an object for IPS. Select Objects > New Host and enter the IPS IP address. Under Servers, enable Web Server and click OK.
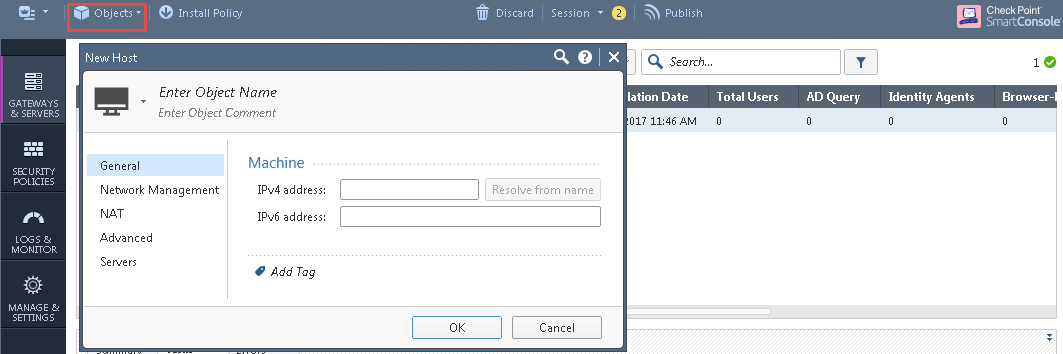
- Select Gateways & Servers > Identity Awareness and enable the following options:
- Terminal Servers- Note down the pre-shared secret key.
- Identity Web API- Click Settings and add the IPS device as Authorised Clients.
- Click Install Policy.
- From the Object Explorer create an object for Identity matching by creating user roles. Select Objects > Object Explorer and Click New > Users > Access Role.
The role names must match with the Role names created on IPS.
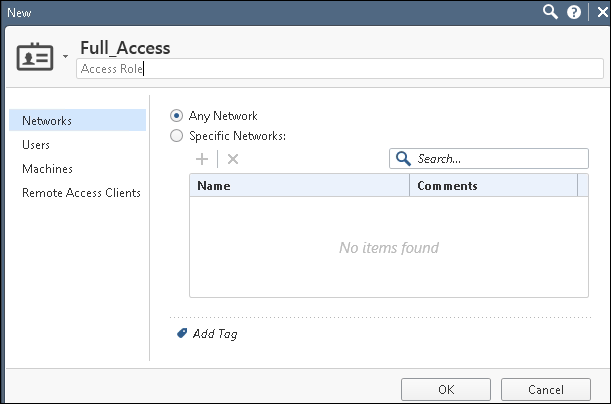
- From the SmartConsole, create a security policy by keeping the Access Role in Source column. Select Security Policies > Access Control > Policy and then configure the required policies. For example, Full_Access policy allows traffic from Client with Full_Access role, Limited_Access role policy denies traffic from Client with Limited_Acces role, and default_allow policy which allows all traffic. The Full_Access role is on the top of the list since it should be considered first.
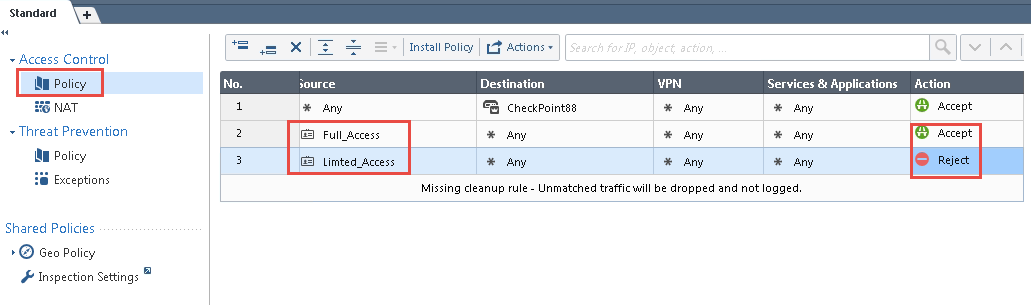
- Click Install Policy.