Deployment of IPS using Check Point Next-Generation Firewall
This section describes the integration of IPS with Check Point Next-Generation Firewall. The Check Point Next-Generation Firewall controls the access to resources (for example, internet, CRM systems, Wikis and so on.) based on policy settings that defines the access. The Check Point Next-Generation Firewall allows integration with directory sources (For example, AD or LDAP) to get user and group information. The policies are then defined based on user role information.
IPS serves as the provider of identity information (For example, user-ID, IP address, and roles) for Check Point Next-Generation Firewall. The Check Point Next-Generation Firewall uses the identity information provided by the IPS for deciding the resource access.
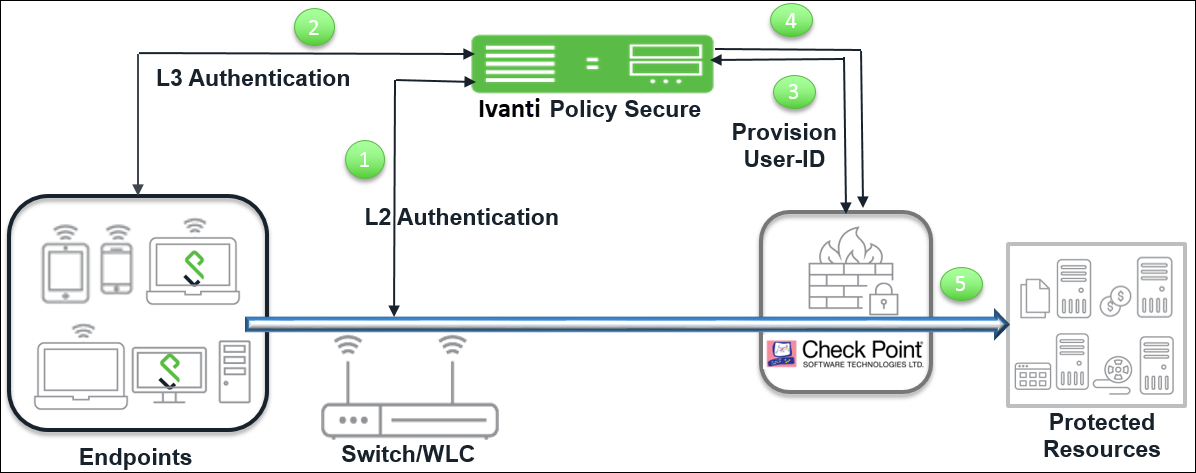
The authentication process is described below:
- The endpoints connect to Switch/WLAN and performs the layer 2 authentication with IPS.
- IPS performs the layer 3 authentication and performs compliance check on the endpoint and detects for any unauthorized behavior. IPS can also learn endpoint IP address using accounting and provision mapping.
- IPS provisions the auth table entries (user-ID, IP address, and roles) on the Check Point Next-Generation Firewall.
- The user role changes, which includes any unauthorized behavior are dynamically updated on the firewall. IPS provisions the auth table with changes in role information if any on Check Point Next-Generation Firewall. The access is based on roles.
- The Check Point Next-Generation Firewall applies policies to allow or block user access to protected resources.