Behavioral Analytics
Overview
Enterprises deal with constant and ever-increasing magnitude of threat vectors, which includes Data Loss Prevention (DLP), malware and Domain Generation Algorithms (DGA) attacks. With changing business requirements and new types of threats, Administrators must understand how users and devices are accessing company’s data and services to ensure that the access control policies are up to date. Even after successful authentication the user’s activity should be monitored fully to ensure device compliance. Policy rules for protecting resources need to be configured and should be resistant to new attacks. Policy rules are configured manually, and the process is not scalable with new attacks. Hence, it is very important for Administrators to have insights into any anomalous behavior and act accordingly.
Behavioral Analytics feature analyzes user’s action along with other context data to derive conclusions about any anomalous activities. It provides information/visibility based on real time user or device context thus helping in advanced attack detection and helps in proactive policy-based enforcement.
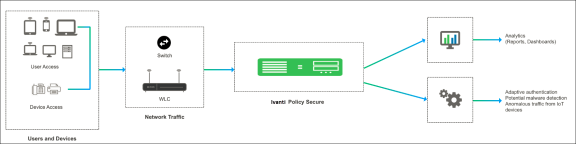
The Behavioral Analytics feature analyzes user or device behavior using the following methods:
- Adaptive Authentication- User/device is prompted for second level of authentication based on the threat profile determined for the corresponding user/device.
Below are some of the scenarios where second level of authentication is required:- User authenticating from new device: This is detected by using the device MAC address.
- User authenticating from new location: Location details are obtained by using the subnet and location configurations.
- Anomalous Traffic from IoT devices: The unmanaged and IoT devices are profiled during the learning period configured in Ivanti Policy Secure. Any Anomolous traffic from these devices is detected as an anomoly based on the known profile of the device. Ivanti Policy Secure uses both Netflow and SPAN configuration on switches for detecting anomalous traffic from IoT devices.
- Potential Malware Detection: Malware on client devices have become more intelligent and in generating domain names by using dynamic generation algoritms. Hence, using rule-based policies might not detect these anomalies. Ivanti Policy Secure uses SPAN data collection method for monitoring DNS traffic and detects these potential malware on the endpoint.
Adaptive authentication user flow
- Users connect to Ivanti Policy Secure.
- Ivanti Policy Secure performs the primary authentication.
- Ivanti Policy Secure checks for any anomalies.
- Ivanti Policy Secure prompts for secondary authentication for the first login or if the user location changes.
- User enters the credentials required for secondary authentication.
- Ivanti Policy Secure performs the secondary authentication and allows/rejects access to the user/device.
Anomalous traffic from IoT devices user flow:
- User/Device establishes a connection with Ivanti Policy Secure.
- Switch and DNS Server forwards the network traffic of the device to Ivanti Policy Secure.
- Ivanti Policy Secure analyzes the network traffic and takes the action based on the detected anomaly.
Potential malware detection user flow:
- User/Device establishes a connection with Ivanti Policy Secure.
- DNS server forwards all the domain resolutions to Ivanti Policy Secure.
- Ivanti Policy Secure analyzes the DNS traffic and detects potential malware on the endpoint.