Configuring FortiAuthenticator
You must add Ivanti Policy Secure as a syslog source in FortiAuthenticator to parse the information.
Prerequisite:
- Ensure that the FortiAuthenticator instance is communicating on the network and is reachable from the Ivanti Policy Secure appliance's management interface.
- Select System > Network > Interfaces, select the port and enable the FortiGate FSSO, FortiClient FSSO and Syslog services on FortiAuthenticator interface, which communicates with Ivanti Policy Secure and FortiGate firewall.
To configure FortiAuthenticator:
-
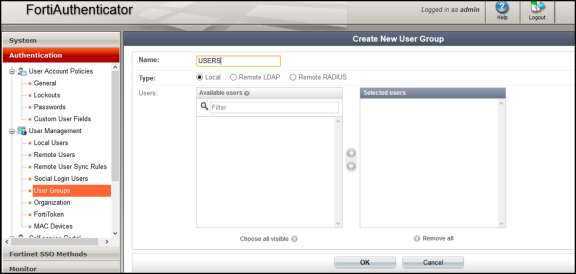
Create a Local user group with the names which matches the name Ivanti Policy Secure will send as the 'Group=' value in your Syslog messages. Select Authentication > User Management > User Groups and click Create New. Create the groups with the following data:
- Name- Enter the same names, which is received from Ivanti Policy Secure, For example, Users.
- Type- Select Local as type.
- Click OK.
-
Create a syslog matching rule. Select Fortinet SSO methods > SSO > Syslog Sources. In the upper right corner, from the 'View' drop down choose matching rules and click Create New and give the following data:
- Name: Enter the name for the syslog Rule.
- Trigger: Enter the filter name created in Ivanti Policy Secure. For example, id=FSSO
- Auth Type Indicators: Enter strings to differentiate between the types of user activities. For example, Logon: AUT24803
- Update: AUT23524
- Logoff: AUT22673
- Username field: Define the semantics of the username field, where {{user}} indicates where the username is extracted from. For example: user= {{: username}}
- Client IP field: Define the semantics of the client IP address. For example, src={{:client_ip}}
- Group field: Define the semantics of the group. For example: roles=" {{: group}}"
There is a trailing space after the User, IP, and Group fields. The parser treats the trailing space as an ending character after the variable portion of the field. The parsing fails if the trailing space is omitted.
- Group List Separator: SSO syslog feed can parse multiple groups if the names are separated by a plus (+) symbol or a comma (,). Use the Group list separator to specify the separator.
- Test Rule: Enter a sample log message into the text box, then select Test to test that the desired fields are correctly extracted.
- Click OK to add the new matching rule.
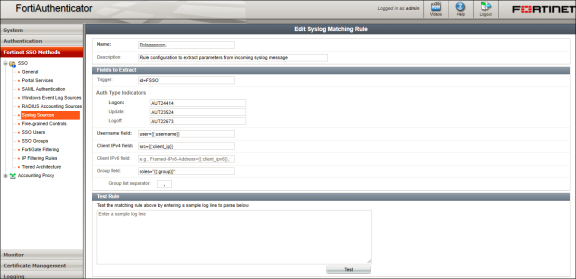
For the Logon and Logoff indicators, the data specified will vary depending on the installation and depending on your syslog message contents. In this example, when a user logs in the message ID created is AUT24414 and is considered as a Logon event on FortiAuthenticator. When the role change happens as part of periodic host check updates, the message ID created by Ivanti Policy Secure is AUT23524. A sign-out event is considered a 'Logoff' event on FortiAuthenticator, and the identity is removed from the user group, thus, failing to match policy.
-
Create a Syslog source, Select Fortinet SSO methods > SSO > Syslog Sources. In the upper right corner, from the 'View' drop down choose Syslog Source and click Create New and provide the following data:
- Name- Enter a name for the source
- IP address- Enter the IP address of Ivanti Policy Secure server
- Matching rule- Select the requisite matching rule created above.
- SSO user type- Select External as the user type.
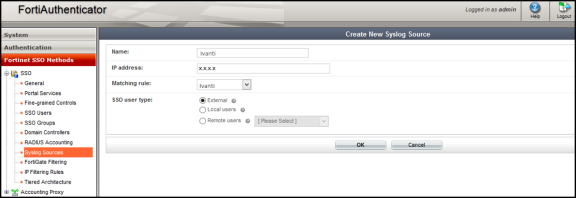
You must add all the cluster node IP's (not cluster VIP's) in the FortiAuthenticator when using a Ivanti Policy Secure cluster setup.