Configuring MAC Authentication on Ivanti Policy Secure
To allow access for unmanageable devices, configure the necessary VLANs on your internal network to accommodate the different devices that you want to allow. On Ivanti Policy Secure, you assign devices to VLANs through the location groups that are added to RADIUS attributes policies.
Configuring the MAC Address Authentication Server
To support MAC authentication, add a MAC authentication server to Ivanti Policy Secure. You can either configure the MAC addresses directly on Ivanti Policy Secure or you can associate the MAC authentication server with an LDAP server.
To configure the MAC address authentication server:
- Select Authentication > Auth.Servers.
- Select MAC Address Authentication and click New Server to display the configuration page MAC address authentication server configuration page.

- Complete the configuration as described in the below table.
- Click Save Changes to save the configuration.
|
Settings |
Guidelines |
|---|---|
|
Name |
Specify a name to identify the configuration. Follow a convention that is helpful to you and others who might perform administration tasks. |
|
MAC Addresses |
|
|
MAC Address |
Enter a MAC address. The system supports various formats, including no-delimiter (003048436665), single dash (003048-436665), multidash (00-30-48-43-66-65), and multicolon (00:30:48:43:66:65). The system supports wildcards (00:30:*:*:*:*). In the user log, entries appear in the multicolon format. |
|
Action |
Select an action to take when the MAC address matches: Allow-Signal successful authentication. Deny-Signal unsuccessful authentication. Allow and Attributes-Typically, a match terminates the search. If you select Allow and Attributes, the search is not terminated; instead, the system searches the LDAP servers for a match to retrieve the LDAP authorization attributes. |
|
Attributes |
Specify a name-value pair to associate the MAC address with a particular group or organization. For example, dept=eng is a name-value pair that associates the MAC address with a department (engineering). When you create the MAC address realm, you can create a custom expression to assign the MAC address to a specific role. Radius Return Attributes from the dictionaries is pre-populated to the Server Catalog of MAC Auth server so that they are available under the custom attributes for a specific user. |
|
Optional LDAP Servers |
|
|
Available / Selected LDAP Servers |
Use the Add and Remove selector buttons to add LDAP servers to the list of selected servers. Use the up and down buttons to order the list. The order in which the LDAP servers are listed is important. The system searches for MAC address matches in the following order: If the MAC address of the endpoint matches a manual entry, the system does not query servers in the LDAP server list. If no manual entries match, the system tries the first LDAP server. If the request times out or gets rejected, the system tries the second, then the third, and so on. Each LDAP server that must be queried affects performance. |
|
Server Catalog |
|
|
Attributes |
If you have selected LDAP servers in the configuration, save the configuration. After you have saved the configuration, the Attributes button is displayed. Click the Attributes button to display the LDAP server catalog, which you can use to select or add attributes to be retrieved from the LDAP servers. |
Configuring the MAC Address Authentication Realm and Role Mapping Rules
The MAC address authentication framework uses a special realm called the MAC Address Authentication Realm. You need not configure a sign-in policy while using MAC address authentication realm. The MAC Address authentication realm uses any username credential that matches one of the common variants of a MAC address format (colon-separated, dash-separated, and the like) and sends it to the MAC authentication realm based on its format.
To configure the MAC Address authentication realm and role mapping rules:
- Select Endpoint Policy > MAC Address Realm.
- Click New to create a new configuration.
- Complete the configuration. The following table summarizes the key settings.
Setting
Guideline
Name
Enter the name of the realm.
Description
Enter the description for identifying the realm.
Server
Authentication server
Select the MAC Address authentication server configured.
User Directory/Attribute
Select the LDAP authentication server configured.
Accounting
Select the MAC Address authentication server configured.
Device attribute
Specify the server for device authorization. For profiler, select the name of the local profiler.
Dynamic Policy Evaluation
Dynamic Policy Evaluation
Select this option to automatically or manually refresh the assigned roles of users by evaluating a realm's authentication policy, role-mappings, role restrictions, and resource policies.
- Save the configuration. Upon saving the new realm, the system displays the role mapping rules page. Under Role Mapping tab, click New Rule. Role Mapping Rule page appears.
- Select Device Attribute under Rule based on tab and click Update. Enter the name for the rule.
- Select the relevant Attribute under Attributes tab for Role Mapping and enter an appropriate value.
- Select an appropriate role from Available Roles and Click Add to Selected Roles.
- Click Save Changes to save the configuration settings.

Configuring User Roles for the MAC Address Authentication Realm
Ivanti Policy Secure access management framework evaluates authentication requests to match endpoints to roles. You must configure user roles for the various types of endpoints authenticated by the MAC address authentication framework.
To create a user role:
- Select Users > User Roles.
- Click New Role.
- Complete the name and description configuration and then save the configuration.
- Click Agent and deselect agent options and then save the configuration.
- Click Agentless and enable agentless access and then save the configuration.
Do not configure role restrictions for roles used with a MAC address authentication realm.
Configuring a Location Group
Location groups let you organize or logically group network access devices by associating the devices with specific sign-in policies. Sign-in policies provide a way to define and direct independent access control policies with the network. For example, you can create location group policies to logically group the network access devices in each building at a corporate campus. You can also use location group policies to specify a special realm for MAC address authentication.
To configure a location group:
- Create a sign-in policy to associate with the location group.
- Select Endpoint Policy > Network Access > Location Group.
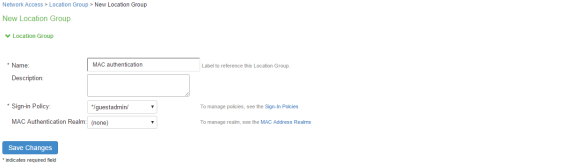
- On the New Location Group page, enter a name to label this location group and optionally a Description.
- For Sign-in Policy, select the sign-in policy associate with the location group.
- For controlling an unmanageable device using MAC address authentication, select a MAC Authentication Realm that you created from the list.
- Click Save Changes.
Configuring RADIUS Client
A RADIUS client policy specifies the information required for unmanaged devices to connect as a RADIUS client of the Ivanti Policy Secure.
To configure a RADIUS client:
- Select Endpoint Policy > Network Access > RADIUS Client.
- Click New RADIUS Client.
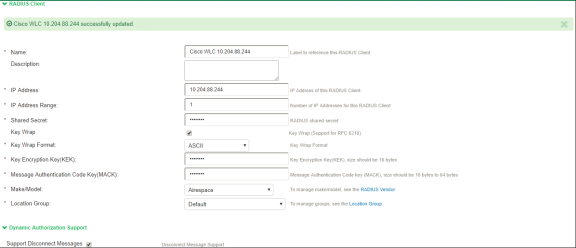
- On the RADIUS Client page, enter a name to label the RADIUS client. You can assign any name to a RADIUS client entry, use the device's SSID or IPv4 address to avoid confusion.
- Enter a purpose or description of the configuration so that other users are aware of it.
- Enter the IP address of the NAD.
- (Optional) For IP Address Range, enter the number of IP addresses in the IP address range for the switch/WLC, starting with the address you specified for IP Address. You can specify a range up to a maximum of 32,768 addresses.
- For Shared Secret, enter the RADIUS shared secret. A RADIUS shared secret is a case-sensitive password used to validate communications between Ivanti Policy Secure and NAD. Ivanti Policy Secure supports shared secrets of up to 127 alphanumeric characters, including spaces and the following special characters: ~!@#$%^&*()_+|\=-'{}[]:"';<>?/.,
- For Make/Model, select the make and model of the NAD. The make/model selection tells Ivanti Policy Secure which dictionary of RADIUS attributes to use when communicating with this client.
- For Location Group, select the location group to use with this NAD.
- Under Dynamic Authorization support, Select the Support Disconnect Messages check box to send disconnect messages to supplicants if access is no longer authorized. If this check box is selected, a disconnect request is sent to the NAD any time a session is deleted. Ivanti Policy Secure can also send disconnect messages upon a role event that includes a VLAN change or a change in RADIUS attributes.
- Select Support CoA Messages to enable CoA messages and disconnect messages support for the client.
- (Optional) Enter a new Dynamic Authorization Port (Default port is 3799). The default port might vary depending on the manufacturer. NAD listens to UDP port to receive RADIUS CoA messages from Ivanti Policy Secure.
- Click Save Changes.
MAC address authentication must be enabled on the switch port. See Configuring 802.1x and MAC Authentication on the Switch Port for switch configuration.
Configuring RADIUS Attributes
This configuration describes the configuration information for RADIUS return attributes policy that is applied on switch, request attribute policy, which can be used along with sign-in policies for realm selection, policy realm restrictions, and authentication/accounting reporting for RADIUS authentication events.
This configuration describes how to send VLAN assignment and other attributes to the switch/WLC by returning RADIUS attributes.
- Select IPS > Network Access > RADIUS Attributes, and then select VLAN.
- Specify a VLAN ID.
- Select Return Attribute.
- Select the attribute you want to return from the Attribute list.
- For Value, specify an attribute value.
IP Address Pools
In current implementation, the Ivanti Policy Secure supports only static IP address assignment. From 9.1R13, Ivanti Policy Secure also allows the admins to assign IP addresses dynamically for the users or nodes from IP address pools.
When the RADIUS authentication succeeds, if the pool name is configured in the Framed-IP-Address return attribute, then the available IP address is assigned to the user from the corresponding IP address pool. When the user session ends (on receiving acct-stop or admin deletes the user session), the assigned IP address is released back to the pool.
In order to release the IP address when a user is deleted from the active user page, it is necessary to have received an “accounting start” request after authentication request by the user/node.
IP address pools are not supported for Ivanti dot1x and native dot1x use cases.
Configuring IP Address Pool
To configure the IP address pools, use the following procedure:
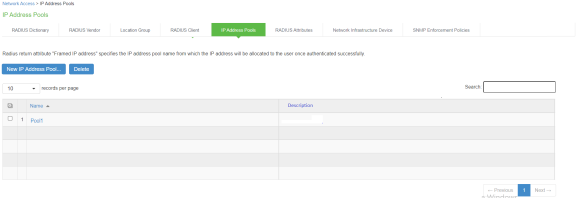
- Navigate to Endpoint Policy > Network Access > IP Address Pools. The page lists the existing IP address pools. Click New IP Address Pool... to add a new address pool.
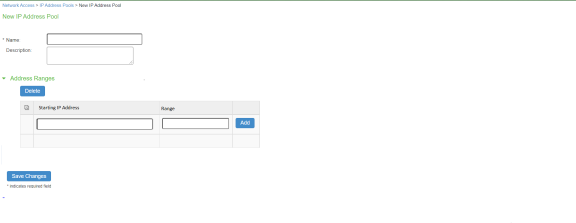
- Add the name and IP address range for the IP address pool and save the changes.
-
1.To configure IP address pools for System Local Users, use the following procedure:
- For System Local Users, under Custom Attributes, select Framed-IP-Address. Then select IP Address Pool as the type and select the name of the IP address pool to add to the attribute list.
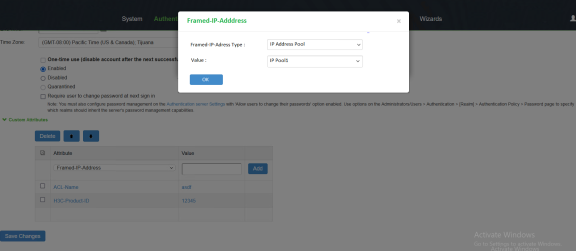
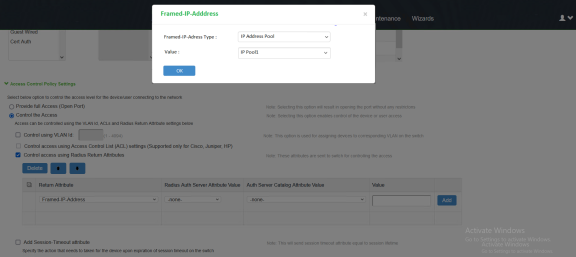
- (Mandatory) If Radius Return Attributes policy is configured, then under Access Control Policy Settings do one of the following:
- Map the Framed-IP-Address attribute to the auth server catalog attribute.
- Select Framed-IP-Address. Then select IP Address Pool as the type and select the name of the IP address pool to add to the attribute list.
- For System Local Users, under Custom Attributes, select Framed-IP-Address. Then select IP Address Pool as the type and select the name of the IP address pool to add to the attribute list.
- To configure IP address pools associated with Radius Client, use the following procedure:
- For Radius Clients, select the IP address pool from the list.
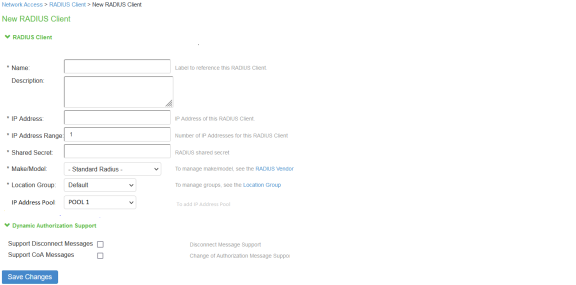
- Once Radius client is associated with the IP pool configuration, associate it with Framed-IP-Address attribute in Radius Return Attribute Policy or User catalog attributes.
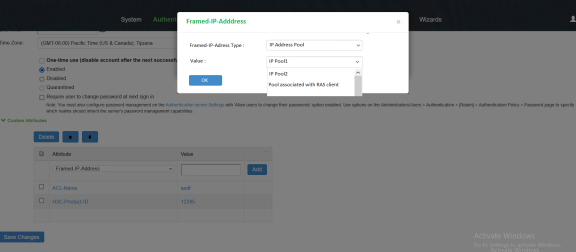
- For Radius Clients, select the IP address pool from the list.
The user catalog attribute value takes precedence over the value associated with Radius Return Attribute policy.
Delegated Admin Control
This feature allows super admin to configure different access levels to RADIUS, SNMP policies and RADIUS Clients, SNMP Clients configurations listed under Endpoint Policy → Network Access.
A super admin can configure a delegated admin role and assign permission levels (Read/Write/Deny) for Network Access Clients and Network Access policies in the Delegated Admin role configuration.
On successful login to IPS, the delegated admin is assigned the permissions as set by super admin.