Policy Enforcement Using Simple Network Management Protocol/SSH
Policy Enforcement using SNMP for Unmanaged Devices
To deploy policy enforcement using SNMP for unmanaged devices, add the switch as an SNMP Agent and the Ivanti Policy Secure device as an SNMP server in the switch and then configure the SNMP Enforcement Policies in Ivanti Policy Secure.
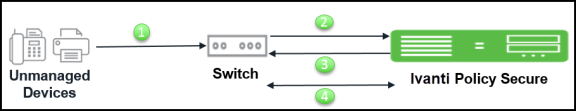
The workflow for the SNMP policy enforcement using linkup/MAC address Notification traps is described below:
- Unmanaged corporate devices such as phones, printers, and cameras connect to SNMP switch. The SNMP switch is configured for linkup/MAC address Notification trap. The SNMP switch generates the SNMP trap. See the Appendix section for switch configuration.
- Ivanti Policy Secure learns or receives the MAC address.
- Ivanti Policy Secure performs the MAC authentication and sets the VLAN/ACL based on the role assigned using SNMP.
- When the user disconnects the device from the switch by plugging out the cable, Ivanti Policy Secure receives an SNMP trap and it deletes the session from the Ivanti Policy Secure server and sets the switch port to the default VLAN/ACL.
The workflow for the SNMP policy enforcement using port-security trap is described below:
- Unmanaged corporate devices such as phones, printers, and cameras connect to SNMP switch. The SNMP switch is configured for port-security trap. A dummy static MAC address is configured on the port. Since machine's MAC address does not match with the configured dummy mac address, it generates a security violation and a port security trap is sent to Ivanti Policy Secure. See the Appendix section for switch configuration.
- Ivanti Policy Secure learns or receives the MAC address.
- Ivanti Policy Secure performs the MAC authentication and the dummy MAC address configured on the interface is replaced with the endpoint MAC address thus authorizing the endpoint on the switch and sets the VLAN based on the role assigned.
- When the user disconnects the device from the switch by plugging out the cable, the session is not deleted from the Ivanti Policy Secure. However, the session is deleted only after the session timeout.
Policy Enforcement using SNMP for Managed Devices
To deploy policy enforcement using SNMP for managed devices, add the switch as an SNMP Agent and the Ivanti Policy Secure device as an SNMP server in the switch and then configure the SNMP Enforcement Policies in Ivanti Policy Secure.
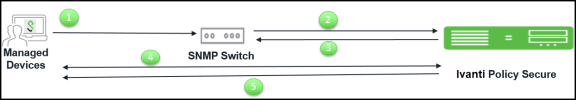
The workflow for the SNMP policy enforcement using link-up/MAC address Notification traps is described below:
- Managed corporate client (Ivanti Secure Access Client is installed) such as Windows/MAC OSX machine connects to SNMP switch port. The SNMP switch is configured for link-up/MAC address Notification trap. The SNMP switch generates the SNMP trap. See Appendix section for switch configuration.
- Ivanti Policy Secure learns or receives the MAC address.
- Ivanti Policy Secure performs the MAC authentication and sets the VLAN/ACL based on the role assigned using SNMP.
- The user connects to Ivanti Policy Secure using Ivanti Secure Access Client. Host checker evaluates the compliance status of machine. If machine is compliant with Host Checker policy.
- Ivanti Policy Secure sets the VLAN/ACL configured for compliant role using SNMP and if machine is non-compliant with Host Checker policy then Ivanti Policy Secure sets the VLAN/ACL configured for non-compliant role using SNMP.
- When the user disconnects the Ivanti Secure Access Client. Ivanti Policy Secure reevaluates the role and sets the VLAN/ACL based on the role assigned.
- When the user disconnects the endpoint from the switch by plugging out the cable, session from the Ivanti Policy Secure server is deleted and the switch port is set to the default VLAN/ACL.
The workflow for the SNMP policy enforcement using port-security trap is described below:
- Managed corporate client (Ivanti Secure Access Client is installed) such as Windows/MAC OSX machine connects to SNMP switch port.
The SNMP switch need to be configured for port-security trap. A dummy static MAC address is configured on the port. Since the machine's MAC address does not match with the configured dummy mac address, it generates a security violation and a port security trap is sent to Ivanti Policy Secure. - Ivanti Policy Secure learns or receives the MAC address.
- Ivanti Policy Secure performs the MAC authentication and the dummy MAC address configured on the interface is replaced with the endpoint MAC address thus authorizing the endpoint on the switch and sets the VLAN based on the role assigned.
- When the user disconnects the device from the switch by plugging out cable, the session is not deleted from the Ivanti Policy Secure. However, the session is deleted only after the session timeout.
- Ivanti Policy Secure sets the VLAN configured for compliant role using SNMP and if machine is non-compliant with Host Checker policy then Ivanti Policy Secure sets the VLAN configured for non-compliant role using SNMP.
- When the user disconnects the Ivanti Secure Access Client. Ivanti Policy Secure reevaluates the role and sets the VLAN based on the role assigned.
- When the user disconnects the device from the switch by plugging out the cable, the session is not deleted from the Ivanti Policy Secure. However, the session is deleted only after the session timeout.
- If the SNMP switch supports MAC Notification traps (MAC added notification trap), you must enable the traps in addition to the Link Up / Link Down traps.
- If Port Security traps are enabled, LinkUp/LinkDown or MAC Added Notification traps should not be enabled.
- Ivanti Policy Secure does not support MAC removed notifications trap. It tracks the session / MAC address associated with a particular interface and removes it once a link down trap is received.
- MAC notification traps are supported only for Cisco and HP switches.
- SNMP Enforcement using ACL is not supported using Port-Security traps.