Using Client Auth Certificates
This topic describes how to use client auth certificates.
Understanding Client Auth Certificates
In certain corporate environments, servers on the LAN are protected with two-way SSL authentication. These servers require the client to authenticate by presenting a valid certificate.
In the remote access scenario, Ivanti Connect Secure is a client of these servers. You can configure Ivanti Policy Secure to present client authentication certificates to servers whenever it communicates over SSL.
This feature authenticates end users or end-user machines to servers on the corporate LAN.
The SSL protocol provides for mutual authentication of server and client at the time of session initiation. The client part of the authentication is optional. For enhanced security, some deployments may require that the client also authenticate itself with a certificate. Normally, when setting up an SSL connection with a server on behalf of the end user, Ivanti Connect Secure does not present any certificate to the server. It needs to be explicitly configured to present such certificate. This section explains how such configuration may be performed.
The basic idea is to upload a certificate, private key pair to the Ivanti access management framework, and configure a mapping between this pair and a server resource. Subsequently, when an end user attempts to establish a connection with that server, Ivanti Policy Secure presents the associated certificate to the server. If no certificate is associated with the server in Ivanti Connect Secure certificate store, then it is assumed that the server does not demand client certificate.
If, during the SSL handshake, the back-end server requests a client certificate but Ivanti Policy Secure doesn’t send a certificate, the end user sees an “access denied” error message. Similarly, if the back-end server rejects the Ivanti Policy Secure certificate, the end user sees an “access denied” error message. If a certificate is configured, is successfully retrieved and no error is encountered during handshake, the user is granted access to the server.
The Ivanti Policy Secure access management framework allows client authentication certificates to be uploaded to the device in two ways: generate a CSR and upload the signed certificate returned by the CA, or directly import the certificate if one is available.
Importing a Client Auth Certificate
The Ivanti access management framework allows certificates that include the private key and for instances where the private key is in a separate file from the certificate. In addition, if your certificates have been exported into a system configuration file, you can import the system configuration file to upload the certificates.
To import the client auth certificates files:
- Select System > Configuration > Certificates > Client Auth Certificates.
- Click Import Certificate & Key to display the configuration page.
- Complete the configuration described in table.
- Click Import.
|
Guidelines |
|
|---|---|
|
If certificate file includes private key |
|
|
Certificate File |
Browse to the network path or local directory location of your private key file. |
|
Password Key |
Enter the password key. |
|
If certificate and private file are separate keys |
|
|
Certificate File |
Browse to the network path or local directory location of your certificate key file. |
|
Private Key File |
Browse to the network path or local directory location of your private key file. |
|
Password Key |
Enter the password key. |
|
Import via System Configuration file |
|
|
System Configuration File |
Browse to the network path or local directory location of the system configuration file. |
|
Password |
Enter the password. |
Renewing a Client Auth Certificate
To renew a certificate:
- Select System > Configuration > Certificates > Client Auth Certificates.
- Click the link that corresponds to the certificate you want to renew.
- Click Renew Certificate to display the configuration page.
- In the Renew the Certificate form, browse to the renewed certificate file, enter the password for the certificate key, and click Import.
Configuring Two-Way SSL Authentication
To configure two-way SSL authentication:
- Import the certificates used for two-way SSL handshake in the System > Configuration > Certificates > Client Auth Certificates window.
- Define the back-end resource and assign a certificate to be presented when accessing it using the Users > Resource Policies > Web > Client Authentication window.
Enabling Certificate Revocation Check for Client Auth Certificate
Client Auth Certificate Revocation Check is only applicable for TLS Syslog Backend Server. It is not applicable for any other backend server configured to ask Client Certificate.
To enable the CRL for Client Auth Certificate:
- Go to System > Configuration > Certificates > Client Auth Certificates.
- Click on the certificate from the list to go to the certificate details.
- In the Certificate Details page, go to Certificate Status Checking and enable the Use CRLs (Certificate Revocation Lists) checkbox.
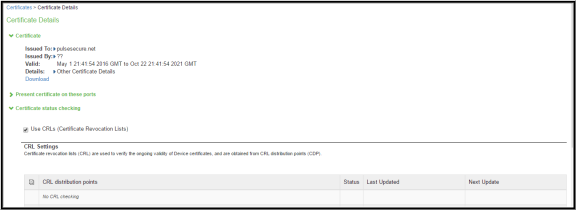
- Click on Save Changes.
- Import the CA or CA Chain that issued the Client Auth Certificate to System > Configuration > Trusted Client CAs.
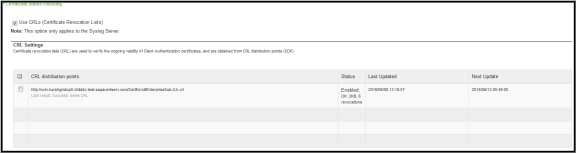
- Once the CRL is successfully downloaded for Client Auth Certificate, it is listed in the CRL distribution points.
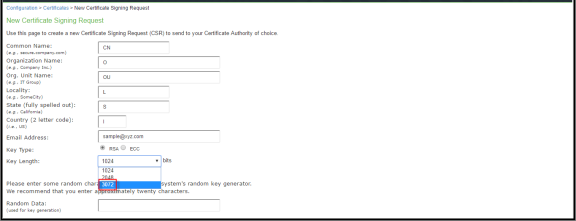
This version of the Ivanti Policy Secure supports the 3072 bit key length for Client Auth Certificates.
CRL Download for Device Certificate and Client Auth Certificate using LDAP based URL won't work due to dependency of LDAP Username and Password. In some cases, CDP LDAP URL hostname field is also required which is also not supported.