Configuring Ivanti Policy Secure for Guest Wired Authentication using Cisco Switch
This section describes the configuration that is required on Ivanti Policy Secure to communicate with a Cisco switch for Guest wired authentication.
To configure Ivanti Policy Secure for guest wired authentication:
- Select Authentication > Auth. Servers. The Authentication Servers screen appears.
- Click Guest Wired Authentication available by default to view the settings.
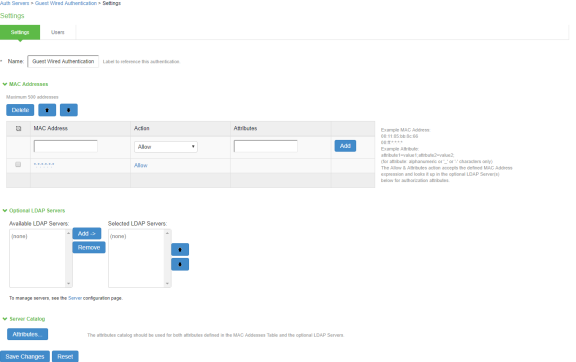
- You can make the necessary changes and click Save Changes.
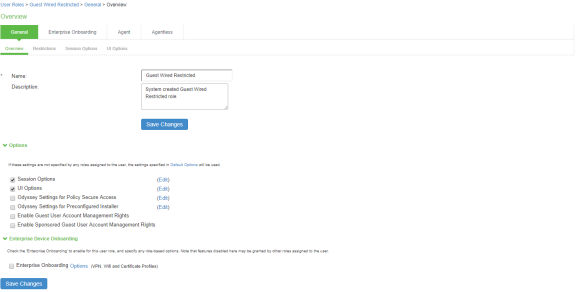
- Select Users > User Roles. The User Roles page appears.
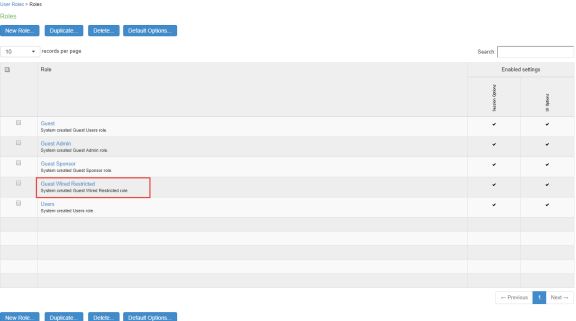
- Click Guest Wired Restricted user role available by default. The Agentless access is enabled for this role. You can also configure Host Checker for assessing the compliance statuts of the endpoint.
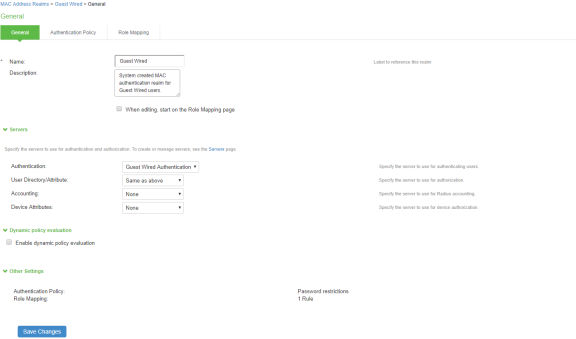
- Select Endpoint Policy > MAC Address Authentication Realms and click Guest Wired authentication realm available by default.
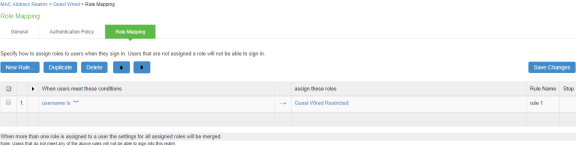
- Select the default role mapping rule, which specifies the conditions to assign the Guest Wired Restricted role.
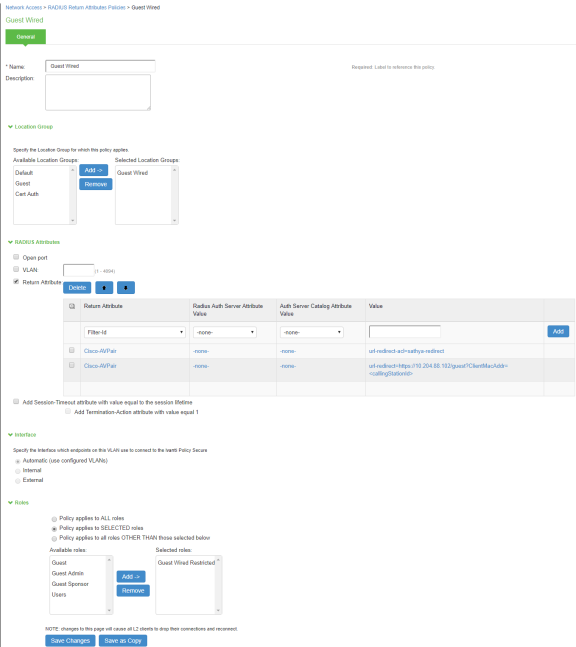
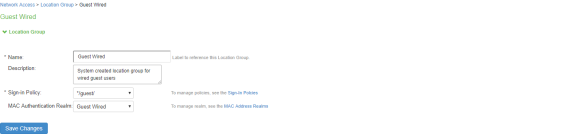
- Select Endpoint Policy > Network Access > Location Group. Select Guest Wired as MAC Auth Realm.
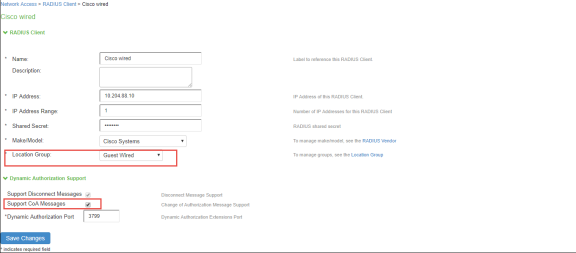
- Configure the Cisco switch as a RADIUS client. Ensure that the Guest Wired location group and Support CoA Messages options are enabled.
- Configure the RADIUS return attributes for Guest Wired policy. The RADIUS return attributes are required for moving the endpoint to the appropriate VLAN.
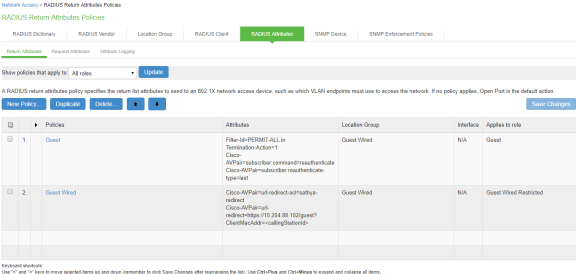
- The user configures the RADIUS URL-redirection attributes on the Cisco Switch. Using RADIUS URL-Redirection return attributes the Cisco switch redirects any initial HTTP/s traffic to Ivanti Policy Secure.
You must configure the following return attributes (supported only on Cisco switches):
Cisco-AVPAIR=url-redirect-acl=REDIRECT_To_Ivanti Policy Secure
Cisco-AVPAIR=url-redirect=https://<Ivanti Policy Secure-SIGN-IN-URL>/guest?ClientMacAddr=<callingStationId>
Here in redirect guest portal URL (*/guest), the "ClientMacAddr" is to identify the end client being redirected to Ivanti Policy Secure. As part of MAB authentication, Ivanti Policy Secure updates the value of radius return attribute "url-redirect" and replaces <callingStationId> with the client MAC address.
The RADIUS CoA configuration for various Cisco switch platforms is described below.
|
Cisco Platform |
IOS Version |
RADIUS CoA Configuration |
|---|---|---|
|
3850 |
16.3 |
Filter-Id=PERMIT-ALL.in |
|
2960X |
15.2 |
Filter-Id=PERMIT-ALL.in |
|
2960 |
12.2 |
Filter-Id=PERMIT-ALL.in |