Profiler
Overview
Profiler dynamically identifies and classifies endpoints across managed and unmanaged endpoint devices, so that access to network and resources can be controlled based on the type of the device. It also helps you to get visibility and enforce your security policies for corporate access, BYOD, and guest access.
The Profiler has the capability to:
- Detect and classify devices using DHCP fingerprinting.
- Provide access control for devices based on the device profile - mainly characterized by Manufacturer, Operating System, and Device Category.
- Provide visibility into IP-enabled devices connecting to the network.
- Enable MAC Authentication.
- Enable granular policies based on device attributes.
A high-level overview of the configuration steps needed to set up and run Profiler is shown in the following figure.
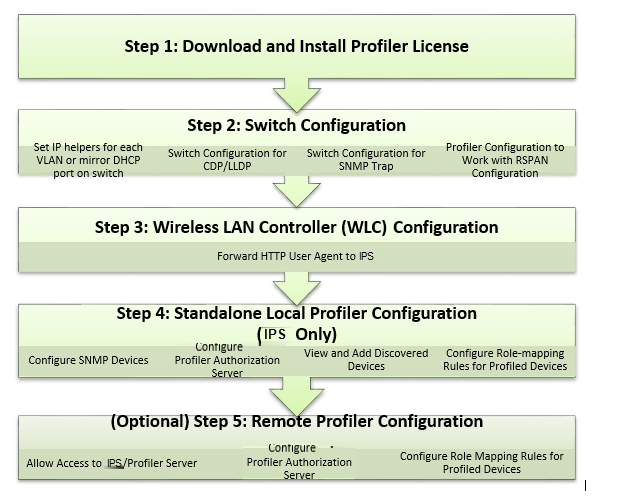
For more information on deployment and configuration, see Profiler Deployment Guide.