Configuring Miscellaneous Security Options
You can use the System > Configuration > Security > Miscellaneous page to configure the following security options:
- Persistent cookie options—Choose whether to preserve or delete persistent cookies when a session is terminated.
- Lockout options—You can configure lockout options to protect the system from denial of service (DoS), distributed denial of service (DDoS), and password-guessing attacks.
To configure cookie and lockout options:
- Select System > Configuration > Security > Miscellaneous to display the configuration page.
- Complete the configuration as described in table.
- Save the configuration.
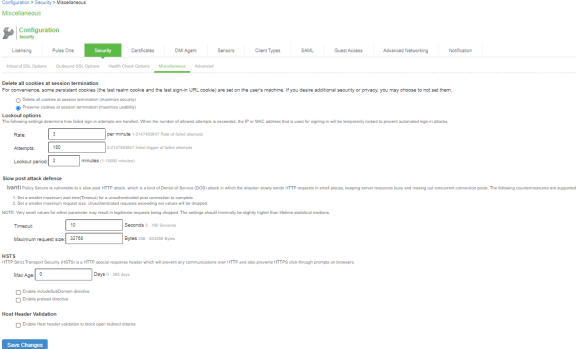
|
Settings |
Guidelines |
|---|---|
|
Delete all cookies at session termination |
For convenience, the system sets persistent cookies on the user’s machine to support functions such as multiple sign-in, last associated realm, and the last sign-in URL. For additional security or privacy, you can choose not to set them. |
|
Lockout options |
|
|
Rate |
Specify the number of failed sign-in attempts to allow per minute. |
|
Attempts |
Specify the maximum number of failed sign-in attempts to allow before triggering the initial lockout. The system determines the maximum initial time (in minutes) to allow the failed sign-in attempts to occur by dividing the specified number of attempts by the rate. For example, 180 attempts divided by a rate of 3 results in an initial period of 60 minutes. If 180 or more failed sign-in attempts occur within 60 minutes or less, the system locks out the IP address being used for the failed sign-in attempt. |
|
Lockout period |
Specify the length of time (in minutes) the system must lock out the IP address. |
|
Slow Post Attack Defence |
|
|
Timeout |
By default, the POST body is received within 10 seconds. If the browser is unable to send the POST body within 10 seconds the connection is eventually dropped. (Configurable from 3 - 60Sec) |
|
Maximum Request Size |
By default, now a connection is directly rejected if it tries to POST more than 4KB in POST body (Configurable from 256 Bytes to 24 KB) |
|
HSTS |
|
|
Max Age |
Specify the maximum age for HSTS. It can be disabled by configuring max age as 0. |
|
Enable include Subdomain directive |
Select the check box to enable/disable the include Subdomain directive. By default, it is turned off. |
|
Enable preload directive |
Select the check box to enable/disable the preload directive. By default, it is turned off.
|
|
Host Header Validation
|
|
|
Enable Host Header Validation to block open redirect attacks |
Select the check box to enforce Host Header validation. By default, it is turned off. When Host header validation is enabled, every http request will be validated against hostnames and IP v4/v6 addresses known to the Ivanti Policy Secure server. If match is not found, the request will be dropped. |
Scenario Illustrating Lockout Settings Workflow
The following scenario illustrates how lockout settings work. For example, assume the following settings:
- Rate = 3 failed sign-in attempts per minute
- Attempts = 180 maximum allowed in initial period of 60 minutes (180/3)
- Lockout period = 2 minutes
The following sequence illustrates the effect of these settings:
- During a period of 3 minutes, 180 failed sign-in attempts occur from the same IP address. Because the specified value for Attempts occurs in less than the allowed initial period of 60 minutes (180/3), the system locks out the IP address for 2 minutes (fourth and fifth minutes).
- In the sixth minute, the system removes the lock on the IP address and begins maintaining the rate of 3 failed sign-in attempts/minute. In the sixth and seventh minutes, the number of failed sign-in attempts is 2 per minute, so the system does not lock the IP address. However, when the number of failed sign-in attempts increases to 5 in the eighth minute, which is a total of 9 failed sign-in attempts within 3 minutes, the system locks out the IP address for 2 minutes again (ninth and tenth minutes).
- In the eleventh minute, the system removes the lock on the IP address and begins maintaining the rate of 3 failed sign-in attempts per minute again. When the rate remains below an average of 3 per minute for 60 minutes, the system returns to its initial monitoring state.