Deployments using 802.1X Authentication
The 802.1X provides authenticated access to LAN, which applies to both wireless and wired networks. In a wireless network, the 802.1X authentication occurs after the client has associated to an access point using an 802.11 association method. The wired networks use the 802.1X standard without any 802.11 association by connecting to a port on an 802.1X enabled switch.
Using 802.1X, the user is authenticated to the network by means of user credentials, such as a password, certificate, or a token card. The keys used for data encryption are generated dynamically. The authentication is not performed by the switch, but rather by Ivanti Policy Secure as the RADIUS server. The 802.1X method uses EAP messages to perform authentication. The newer EAP protocols can dynamically generate the Wired Equivalent Privacy (WEP), Temporary Key Integrity Protocol (TKIP), or Advanced Encryption Standard (AES) keys that encrypt data between the client and the wireless access point. Dynamically created keys are more difficult to break than preconfigured keys because their lifetime is much shorter. The known cryptographic attacks against WEP can be prevented by reducing the length of time that an encryption key remains in use. The encryption keys generated using EAP protocols are generated on a per-user and per-session basis. The keys are not shared among users, as they must be with preconfigured keys or preshared passphrases.
Deployment of Ivanti Policy Secure with External Authentication Server
It is difficult or impossible to maintain a centralized database of users in environments with many distributed users. You can easily pair Ivanti Policy Secure with an organization's other identity databases, such as LDAP and Active Directory to leverage existing credentials. Ivanti Policy Secure RADIUS server can forward authentication requests from a network access device (NAD) to an external Authentication server.
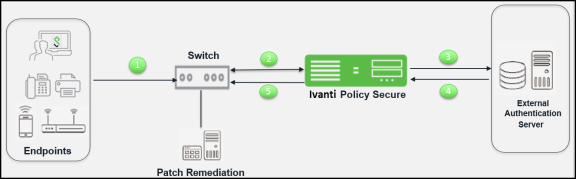
The authentication process is described below:
- The endpoint connects to an 802.1X enabled switch/WLC. The endpoint exchange EAP messages using 802.1X, which contain information about user credentials and the health of the endpoint.
- The switch receives the request and starts the RADIUS authentication with Ivanti Policy Secure.
- Ivanti Policy Secure receives the request and then converts the request to the required format for the external authentication server.
- If Ivanti Policy Secure successfully authenticates the user, it sends a message to the switch/WLC to allow the endpoint access to the network. The type of access granted depends on the user's identity and the health of the endpoint. For example, if the endpoint meets the requirements of all Host Checker policies, the user can have full network access. If the endpoint does not meet some security requirements, the user can be granted access to a remediation server. If the endpoint is using Ivanti Secure Access Client as its 802.1X supplicant, Ivanti Policy Secure and the endpoint exchange messages as necessary throughout a session (for example, to monitor the endpoint's security compliance). If the endpoint is using a native supplicant, Host Checker is not supported.
- If the endpoint is using Ivanti Secure Access Client, and the endpoint meets the requirements of all Host Checker policies then Ivanti Policy Secure allows user to access the protected resources.
The user's identity and the endpoint health assessment are used to determine which VLAN to use for the switch port that the endpoint is connected to. Typically, if the endpoint does not meet minimum criteria for health assessment as defined by the administrator, the endpoint will be placed on a restricted VLAN which allows access to servers which can aid in remediating the endpoint.
You define VLAN policies for endpoints that access switches using 802.1X. After an authenticated endpoint, has been mapped to a set of roles, the VLAN policies are evaluated and the VLAN information is communicated to the switch through RADIUS attributes. RADIUS attributes vary by make and model of switch. You specify the make and model when configuring a RADIUS client on Ivanti Policy Secure.
In addition to authenticating endpoints with 802.1X Ivanti Policy Secure RADIUS server can be used to authenticate 802.1X IP phones, switches.
Deployment of Ivanti Policy Secure as a RADIUS Server
Ivanti Policy Secure provides the RADIUS server functionality for layer 2 enforcement. Using the Ivanti Policy Secure internal RADIUS server, you can provision 802.1X authentication for endpoints. Layer 2 authentication and enforcement is used to control network access policies at the edge of the network using an 802.1X enabled switch or access point.
A RADIUS license allows you to use the Ivanti Policy Secure series device as a RADIUS appliance. To apply your initial license or to upgrade your license, select System > Configuration > Licensing in the left navigation pane.
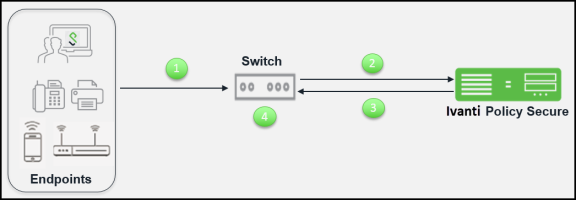
The authentication process is described below:
- The endpoints connect to switch over 802.1X using EAP protocol.
- The switch receives the request and starts the RADIUS authentication with Ivanti Policy Secure.
- Ivanti Policy Secure integrated RADIUS server receives the request and performs the authentication and then returns the attributes for controlling user access.
- The switch uses the returned attributes to control the user access privileges on the port or service set identifier (SSID).
The following RADIUS configuration options are available only with RADIUS license.
- Host Checker Custom: Statement of Health policy- When you apply both a RADIUS license and an MS-NAP license, you can configure an Endpoint Security policy by way of the Host Checker policy. If you have only a RADIUS license, the Endpoint Security menu is not available.
- RADIUS User Count- This feature allows you to create RADIUS users. To view the number of RADIUS users, select System > Status. The number of RADIUS users does not count against the concurrent user license if you have both a RADIUS license and a user license installed.
The following features are not available with RADIUS only license:
- IF-MAP Federation
- Infranet Enforcer
- Host Enforcer
- Endpoint Security
- Push Configuration
- MDM Authentication servers
- Sign-in Notifications
- Agent and Agentless tabs do not appear on the Overview page.
- Enterprise onboarding
Deployment of Ivanti Policy Secure as a RADIUS Proxy
In environments with many distributed users, it can be difficult or impossible to maintain a centralized database of users. Using RADIUS proxy, Ivanti Policy Secure RADIUS server can forward authentication requests from a network access device (NAD) to an external RADIUS server.
You can configure Ivanti Policy Secure to proxy RADIUS inner or outer authentication to an external RADIUS server. Proxying inner or outer authentication gives you the flexibility to direct requests for authentication through whatever realm is most appropriate for each user.
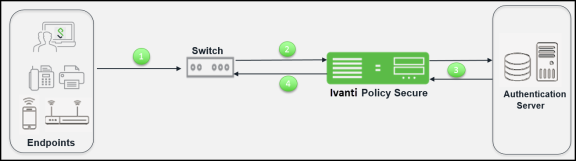
The authentication process when using an external authentication server is described below:
- The endpoints connect to switch.
- The switch receives the request and starts the RADIUS authentication with Ivanti Policy Secure.
- Ivanti Policy Secure receives the request and then forms another RADIUS request and forwards it to the external RADIUS server.
- If authentication succeeds the Ivanti Policy Secure assigns the user the appropriate roles, and then passes the associated RADIUS attributes back to the access device.
With RADIUS proxy enabled, Ivanti Policy Secure acts as a simple relay agent and does not participate in the accounting and authorization process. You must configure all attributes for authenticator configuration on the external RADIUS server.
You can specify the outer or inner proxy as follows:
- Outer proxy requires that the external RADIUS server presents a certificate to the supplicant. The result is a secure tunnel between the supplicant and the external server.
- Inner proxy uses the Ivanti Policy Secure certificate to establish the secured tunnel, but relays the supplicant authentication data to the external RADIUS server. The secured tunnel is established between the supplicant and Ivanti Policy Secure. The data passes between the Ivanti Policy Secure and the external RADIUS server in clear text.