Configuration
The goal is to provide secure and role-based access control for Guest Access using ACLs on Huawei WLC/Switch through Ivanti Policy Secure.
Using Guest Authentication Server
Use the Default Guest Authentication Server under Authentication > Auth.Servers.
The Guest configuration page is shown below.

Using Default Realm
Select User Realms > User Authentication Realms.
Using Default Sign-in Policy
Select Authentication > Signing In > Sign-in Policies.
Creating a Host Checker Policy
-
Select Authentication > Endpoint Security > Host Checker.
-
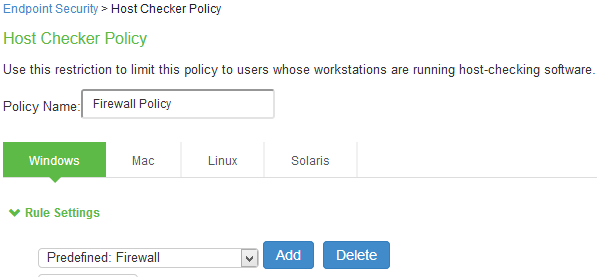
Under Policies, Click New and enter a policy name and click Continue.
-
Under Rule Settings, select the rule type as Predefined Firewall and click Add.
-
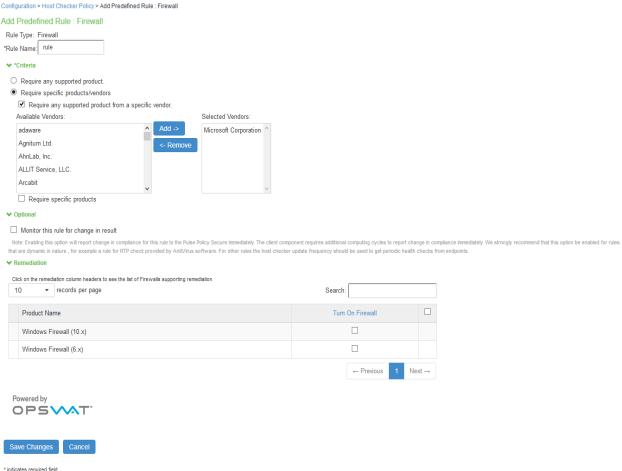
Enter the rule name and specify the criteria for compliance and click Save Changes.
Creating User Roles
-
Select Users > User Roles > Guest Role (Default).
User defined roles can also be created. For example, Remediation Role.
-
Click Save Changes.
-
Select User Roles > <Full Access Role> > General > Restrictions > Host Checker. Add the Firewall Policy restriction created earlier inCreating a Host Checker Policy for Full Access Role. Click Save Changes.
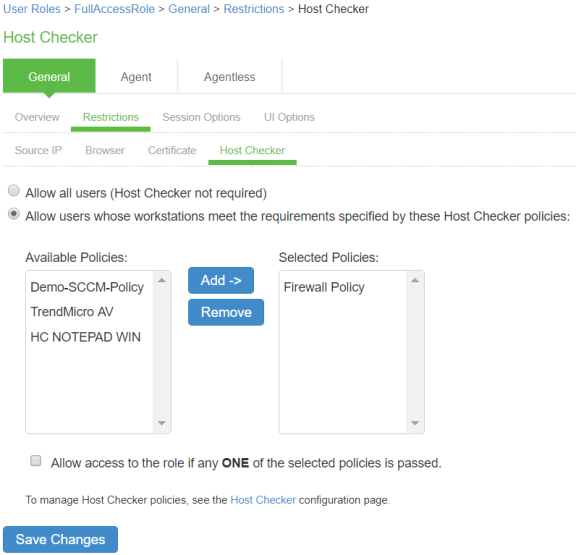
For Remediation Role, ensure that the Host Checker not required option is not selected.
-
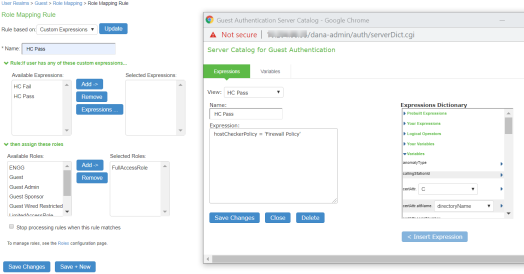
Set Role Mapping rules. Select User Realms > Guest > Role Mapping > New Rule
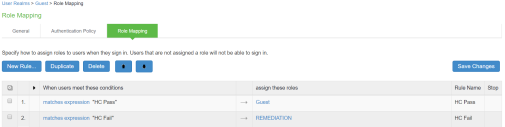
Once the role mapping roles are configured the following screen is displayed.
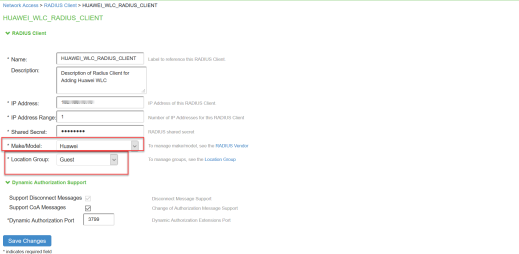
Creating a new RADIUS Client
Add the Switch as RADIUS client
-
Select Endpoint Policy > Network Access > RADIUS Client.
-
Enter the name.
-
Enter the IP address of the Switch.
-
Select the make/model as Huawei.
-
Select the default location group as Guest.
-
Click Save Changes .
Shared Secret will be used in the Huawei/RADIUS configuration.
Configuring RADIUS Return Attribute Policies
Define Radius Return Attribute policy based on ACL for different roles.
-
Set RADIUS return attributes. Select Endpoint Policy > Network Access > RADIUS Return Attribute Policies. Click New Policy.
-
Under RADIUS Attributes tab, select the check box for Return Attribute. Select appropriate Vendor Specific Attribute as Return Attribute. In the Value filed, define the ACL/Firewall Filter. For example, Return Attribute is Filter-Id and Value as full_access.in.
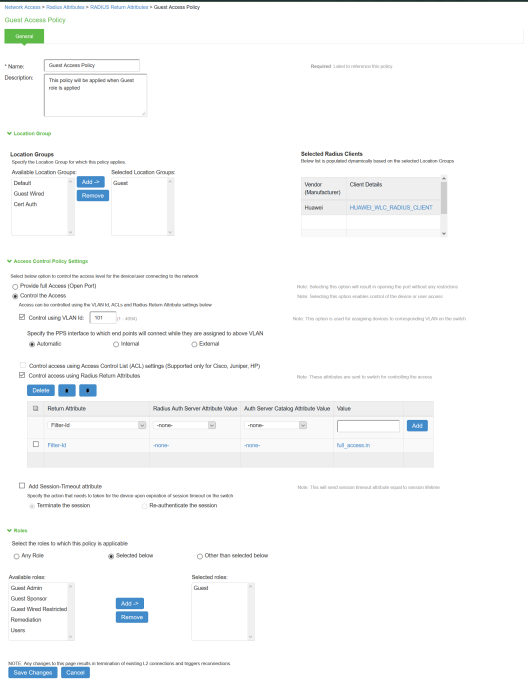
Similarly define a remediation policy with Return Attribute as Filter-Id and Value as limited_access.in.

The following example shows the Filter-Id radius attribute policy for Huawei Switches.
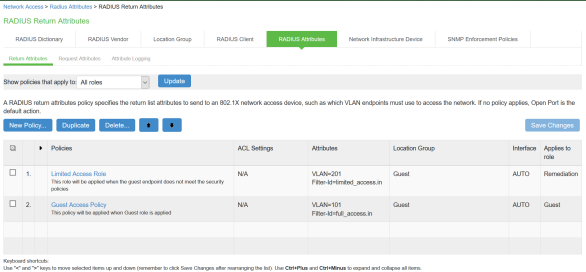
The following example shows RADIUS return attribute used to send the VLAN ID. In the below example, VLAN 101 is sent for Guest Access Role and VLAN 201 for Limited Access Role.
The following example shows the Filter-Id radius attribute policy for Huawei Switches.
- When using VSAs there is no need to configure ACL/Firewall filters in the switches. These are managed by Ivanti Policy Secure and access control entries (ACEs) will be applied on the switches after User Authentication.
- VLAN change using CoA is supported with Huawei Switches.
Configuring Huawei WLC/Switch
Administrator must configure hw_redirect_url as redirect url parameter key and hw_login_url as key for the login url parameter on Huawei switch.
Configure external Port Authentication on Access Controller
# Configure RADIUS authentication parameters.
# Configure a RADIUS server template.
[Huawei]radius-server template radius_wlc_pps
[Huawei-radius-radius_wlc_pps]display this
radius-server template radius_wlc_pps
radius-server shared-key cipher %^%#XX!84-3lJ~dR8X#p:-{0(TF+'=IOe<MG'BR2QrL&%^%#
radius-server authentication 192.168.10.11 1812 weight 80
radius-server accounting 192.168.10.11 1813 weight 80
calling-station-id mac-format hyphen-split mode2 uppercase
# Create an AAA scheme and set the authentication method to RADIUS.
[Huawei]aaa
[Huawei-aaa]authentication-scheme radius_wlc_pps
[Huawei-aaa-authen-radius_wlc_pps]display this
authentication-scheme radius_wlc_pps
authentication-mode radius
# Configure a Portal server profile
[Huawei]portal https-redirect enable
[Huawei] portal web-authen-server https ssl-policy ssl_policy port 8443
[Huawei]interface LoopBack 0
[Huawei-LoopBack0]display this
interface LoopBack0
ip address 10.0.0.1 255.255.255.255
[Huawei]free-rule-template name default_free_rule
[Huawei-free-rule-default_free_rule]display this
free-rule 0 destination ip 10.0.0.1 mask 255.255.255.255
[Huawei]url-template name test
[Huawei-url-template-test]display this
url-template name test
#URL of the guest login page
url https://<IPS-IP>/guest
# Configure hw_redirect_url as redirect url parameter key and hw_login_url as key for the login url parameter on Huawei.
# hw_redirect_url: URL that the user is redirected to after successful authentication.
# hw_login_url: Switch URL needed to post parameters. Admin must configure login url value.
url-parameter redirect-url hw_redirect_url login-url hw_login_url https://10.0.0.1:8443/login
# https://10.0.0.1:8443/login is the login page of the Huawei
[Huawei]web-auth-server wlan-net
[Huawei-web-auth-server-wlan-net] display this
web-auth-server wlan-net
server-ip 192.168.10.11
port 50100
url-template test
server-detect action log
protocol http
http get-method enable
http-method post login-fail response err-msg authenserve-reply-message (or) http-method post login-fail response err-msg msg AuthenticationFailed (Recommended to configure one of this)
#Configure the Portal access profile portal_access_profile
[Huawei-portal-acces-profile-portal_access_profile]display this
portal-access-profile name portal_access_profile
web-auth-server wlan-net direct
#Create the authentication profile wlan-authentication
[Huawei-authen-profile-wlan-authentication]display this
authentication-profile name wlan-authentication
portal-access-profile portal_access_profile
free-rule-template default_free_rule
access-domain wlc_pps dot1x
access-domain wlc_pps dot1x force
access-domain wlc_pps portal
Configure WLAN service parameters.
# Create the security profile wlan-net and retain the default security policy (open system authentication).
[Huawei]wlan
[Huawei-wlan-view]security-profile name wlan-security
# Create the SSID profile.
[Huawei-wlan-view]ssid-profile name wlan-ssid
[Huawei-wlan-ssid-prof-wlan-ssid]display this
ssid wlan-pps
# Create the VAP profile wlan-vap, configure the data forwarding mode and service VLANs, and bind the security profile, authentication profile, and SSID profile to the VAP profile.
[Huawei-wlan-view]vap-profile name wlan-vap
[Huawei-wlan-vap-prof-wlan-vap]display this
forward-mode tunnel
service-vlan vlan-pool vlan_pool_101_201
ssid-profile wlan-ssid
security-profile wlan-security
authentication-profile wlan-authentication
# Bind the VAP profile wlan-vap to the AP group and apply the profile to radio 0 and radio 1 of the AP.
[Huawei-wlan-view]ap-group name ap-group1
[Huawei-wlan-ap-group-ap-group1]display this
regulatory-domain-profile domain1
radio 0
vap-profile wlan-vap wlan 1
radio 1
vap-profile wlan-vap wlan 1
#Create the ACL for full access and limited access. Admin must use the same ACL names in IPS.
acl name full_access 3998
description full_access.in
rule 1 permit ip
acl name limited_access 3999
description limited_access.in
rule 1 deny ip destination <Resource-IP>