Summary of Configuration
To prepare your network to perform endpoint protection using Ivanti Policy Secure, McAfee ePolicy Orchestrator (ePO) server and Firewall, perform the following tasks:
The following sections describe each of these steps in detail.
Configuring Ivanti Policy Secure with McAfee ePO Server
The Ivanti Policy Secure configuration requires defining the McAfee ePO server as HTTP attribute server in Ivanti Policy Secure.
A high-level overview of the configuration steps needed to set up and run the integration is described below:
-
The Administrator configures the basic Ivanti Policy Secure configurations such as creating an authentication server, authentication realm, user roles, and role mapping rules.
-
Configure McAfee ePolicy Orchestrator (ePO) as HTTP attribute server in Ivanti Policy Secure.
-
Configure the Switches/WLC as RADIUS Client in Ivanti Policy Secure (Endpoint Policy > Network Access > Radius Clients > New Radius Client). Switch should be configured with Ivanti Policy Secure as a RADIUS server.
-
Configured HTTP attribute server has to be mapped as a "Device Attributes" under the realm configuration and role mapping rules can be used to assign the roles based on the attributes values received from the attribute server.
-
Admin can optionally configure the remediation action to report the unmanaged endpoint IP address to McAfee ePO server.
Configuring HTTP Attribute Server
The default McAfee template provides the list of possible attributes that can be received from the network security device along with attribute value. The template also provides possible remediation actions that can be taken for an attribute. Ivanti Policy Secure is loaded with default template for McAfee ePolicy Orchestrator (ePO).
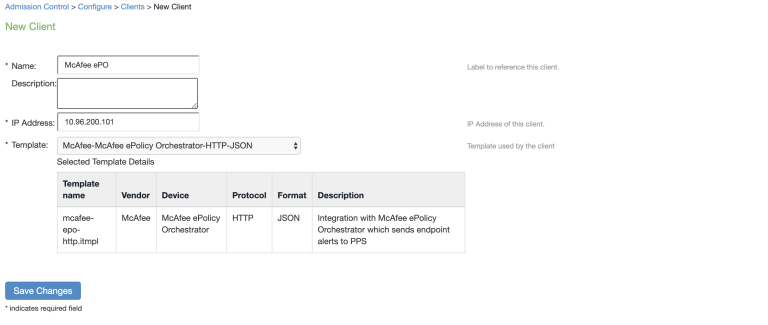
To add the HTTP Attribute server in Ivanti Policy Secure:
-
Select Authentication > Auth.Servers, select HTTP Attribute Server under New and Click New Server.
-
Enter the name.
-
Select McAfee-McAfee ePolicy Orchestrator - Endpoint Protection Platform as template.
-
Enter the IP address or hostname of McAfe ePO server.
-
Enter the port number. Default is 8443.
-
Enter the username and password (Admin credentials of McAfee ePO server).
-
Click Test Connection to test connectivity between Ivanti Policy Secure and McAfee ePO server.
-
(Optional) Under Remediation Action, enable report endpoint to report endpoint details to McAfee ePO server and enter the Group ID to which the endpoint has to be added on McAfee ePO server. See Identifying the Group ID to identify the Group ID.
-
Profiler has to be configured to take remediation action for endpoints authenticating through native supplicant.
-
Remediation action of reporting endpoint IP address is not supported for unmanaged devices (For example, Printers, Scanners), VoIP phones and Mobile devices.
-
Remediation action of reporting endpoint is supported only with Windows, Linux, and Mac OS.
-
-
Click Save Changes.
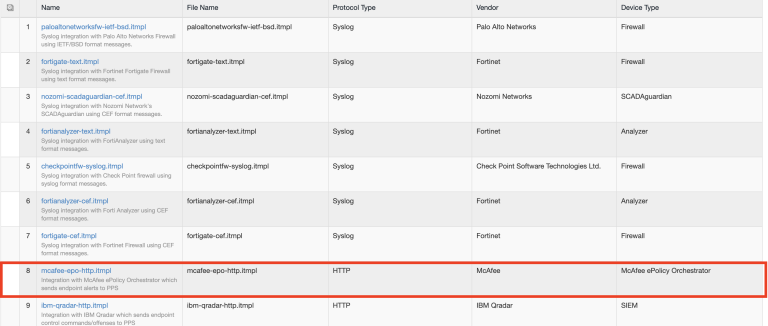
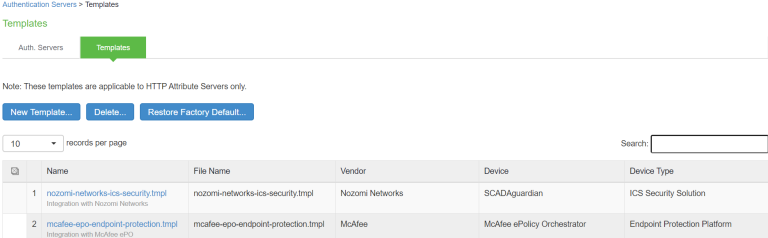
A subset of attributes supported by McAfee ePO server is added in the default template. A new template can be created by Admin and has to be uploaded on Ivanti Policy Secure for supporting any additional attributes apart from the one's in the default template. See the template creation guide for template creation.
-
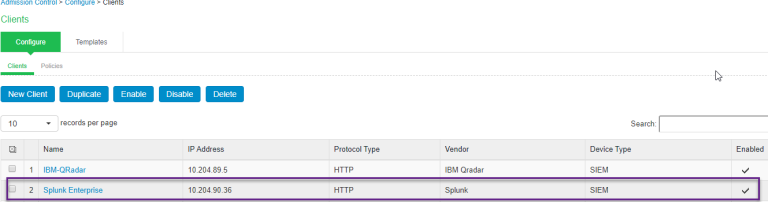
Under User Realms > Users > General, select the McAfee HTTP attribute server created in Device Attributes or Endpoint Policy > MAC Address Realms click New to create the authentication realm. Under Device Attributes, select the McAfee ePO HTTP attribute server created earlier.
-
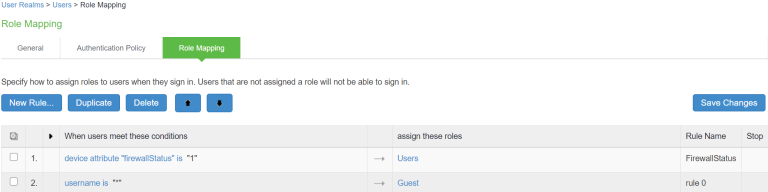
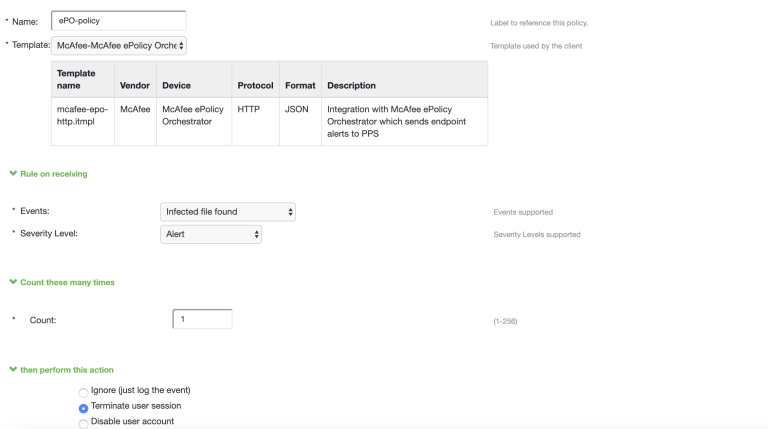
Configure rules based on Device Attributes from User Realms > Users > Role Mapping > Role Mapping Rule or Endpoint Policy > MAC Address Realms and click Role Mapping > Role Mapping Rule.
-
Click Save Changes.
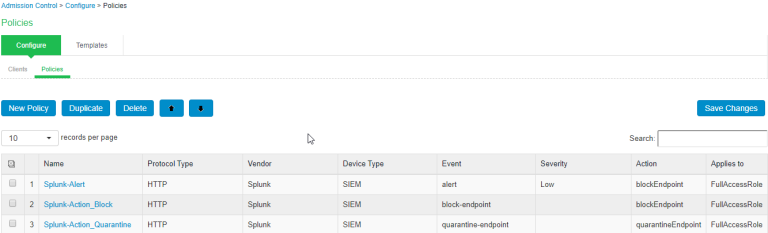
Once the role mapping rule is created. You can see the summary page as shown below. The following page shows the different rules created with the corresponding roles assigned.
MAC Address is used as a device identifier to query attributes from McAfee ePO server. Without Host Checker, Ivanti Policy Secure doesn't learn the MAC address. For agent less sessions, Host Checker should be enabled to learn MAC address. For Agentless sessions/logins, pre-auth Host Checker must be enabled.