Scenario 4: Corporate Laptop Connecting via Ivanti Secure Access Client through the Internal Firewall
Role Based Access Control at Firewall
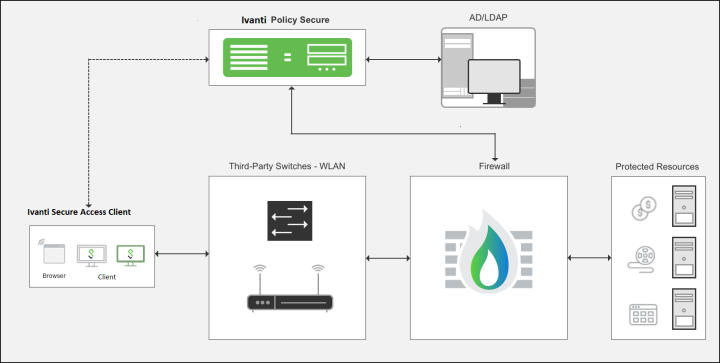
In this scenario, Pat, a marketing employee, is connecting from his office to access the Business Objects applications that he is authorized to access.
In this scenario, Pat is trying to access a mission critical application protected by a firewall. The administrator can create an access policy, tying user roles to policy—for example, only users in a marketing role can access the Business Objects networked application. Note that this policy is created during initial setup configuration.
The first step is to perform a full host check to ensure that the device meets corporate policy. Next, the Ivanti Policy Secure talks to the AD server to perform authentication and authorization. When AD confirms that Pat is part of the marketing organization, and the role is pushed to the firewall along with the device IP. The firewall maps Pat to a specific resource access policy based on this role information and enables to access the applications.
The integration between Ivanti Policy Secure and third-party next-generation firewalls (Currently supported are Juniper SRX Series, Palo Alto Networks Firewall, Check Point Firewall, and Fortinet) built security ecosystem for heterogeneous networks. When combined with Ivanti Policy Secure, the firewall becomes identity-aware to enforce application security policies per user and role basis, and meets compliance regulations. This delivers fine grained access control that is easily managed from a central location. It also enables IT admin to extend NAC BYOD at the perimeter level to offer end-to-end secure access.