Configuring Ivanti Policy Secure for Dot1x Authentication
Configuring User Role for Dot1x Authentication
Ivanti Policy Secure access management framework evaluates authentication requests to match endpoints to roles. You must configure user roles for the various types of endpoints authenticated by the MAC address authentication framework.
To create a user role:
-
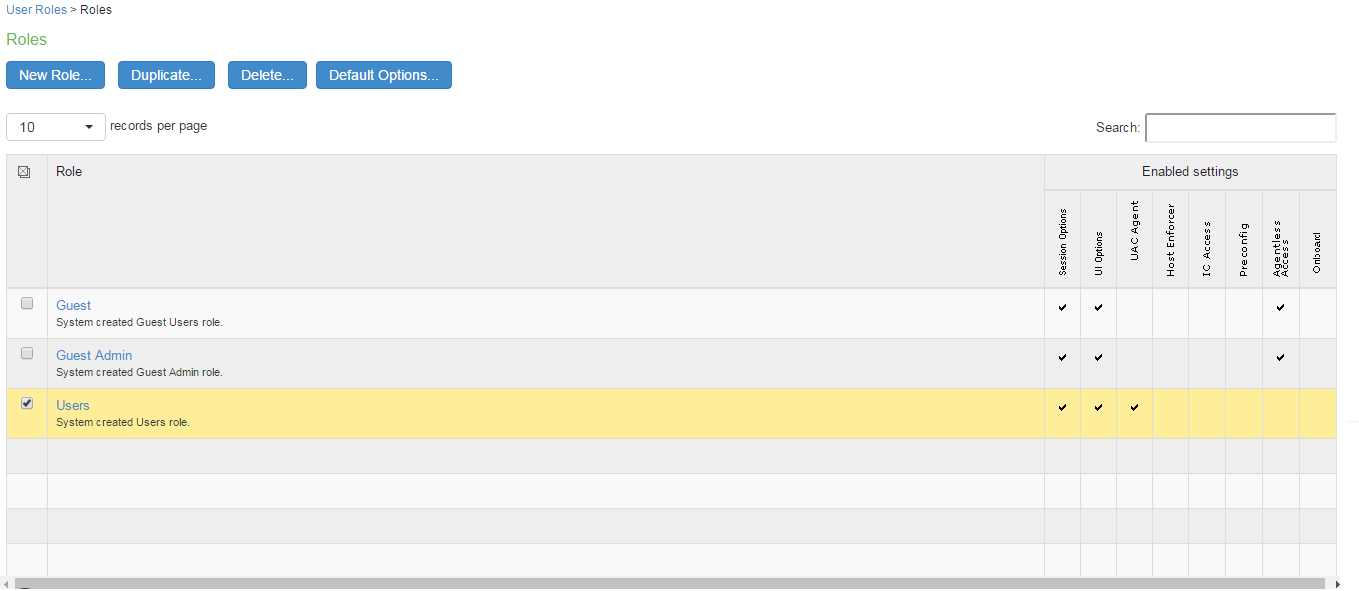
Select Users > User Role to navigate to the role configuration page.
-
Click New Role to display the configuration page shown in figure.
-
Complete the configuration for general options.
-
Save the configuration.
Configuring User Realm for Dot1x
The user realm configuration associates the MDM server data with user roles.
To configure the realm and role mapping rules:
-
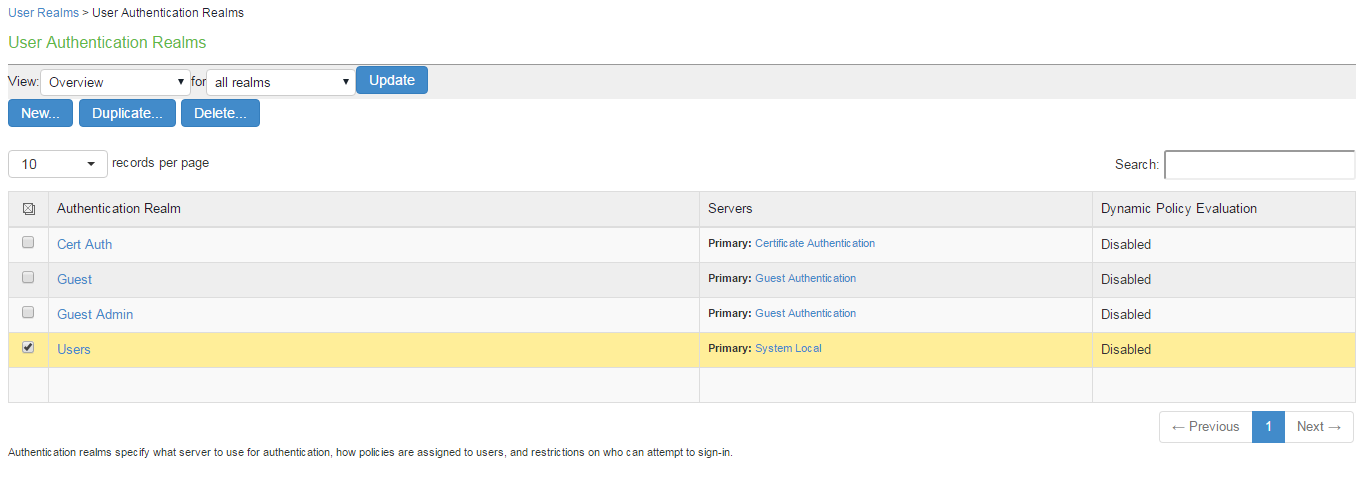
Select Users > User Realms > New User Realm to display the configuration page shown in figure.
-
Make necessary changes and save the configuration.
Configuring a Sign-In Policy for Dot1x
A sign-in policy associates devices with a realm.
To configure a sign-in policy:
-
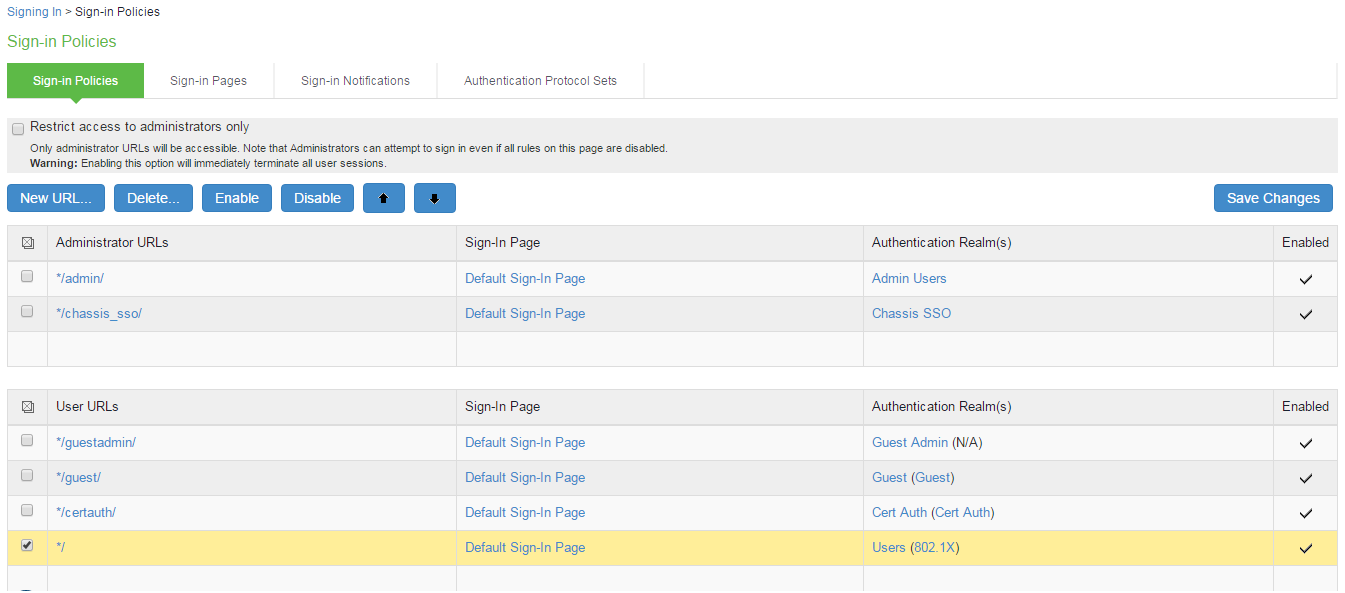
Select Authentication > Signing In > Sign-In Policies to navigate to the sign-in policies configuration page.
-
Click New URL to display the configuration page shown in the following figure.
-
Make necessary changes and save the configuration.
Configuring Location Group for Dot1x
To configure Policy Secure 802.1x framework for non-supplicant endpoints, you must configure Location Group.
-
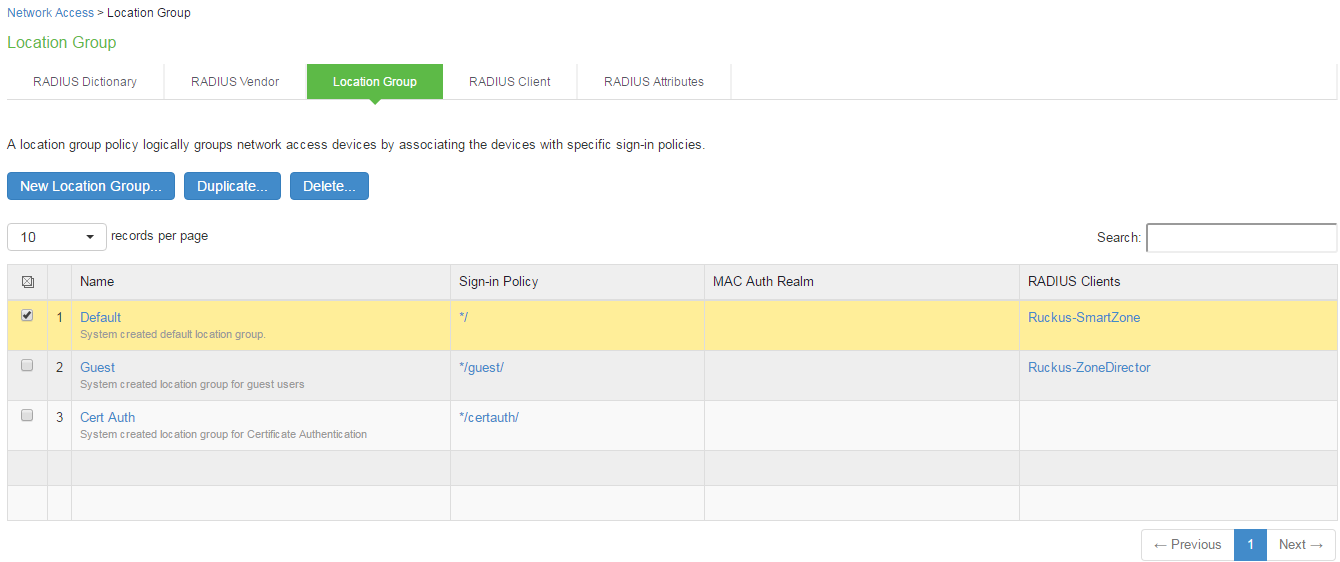
Select Endpoint Policy > Network Access > Location Group.
-
Complete the configuration as shown in figure.
-
Save the configuration.
Configuring Authentication Protocol Set for Dot1x
Switches from various vendors may use the Standard Password Authentication Protocol (PAP), CHAP, or EAP-MD5 protocols for MAC authentication. These protocols are not included in the default authentication protocol set for 802.1x deployments.
To add PAP, CHAP, and EAP-MD5 to the 802.1x protocol set:
-
Log into Ivanti Web administrator interface.
-
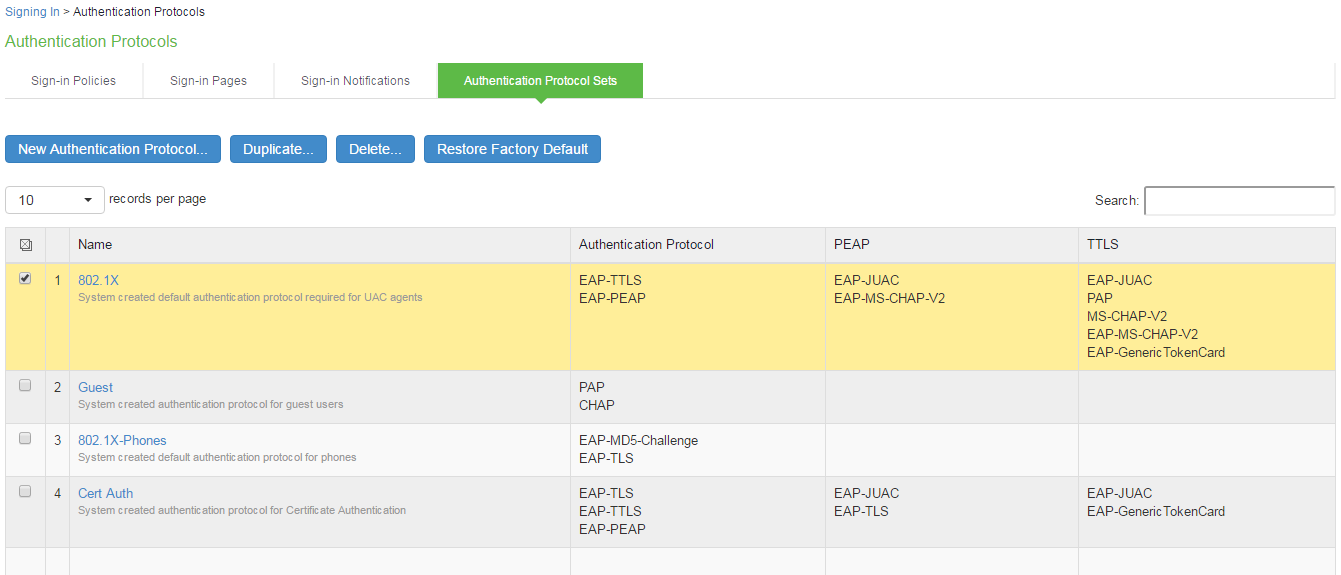
Select Authentication > Signing In > Authentication Protocols Sets to display the Authentication Protocol Sets page.
-
Click the 802.1x link to edit the 802.1x authentication protocol set configuration.
-
Use the selector buttons to add PAP, CHAP, and EAP-MD5-Challenge to the 802.1x authentication protocol set.
Configuring RADIUS Client
To configure a Radius Client:
-
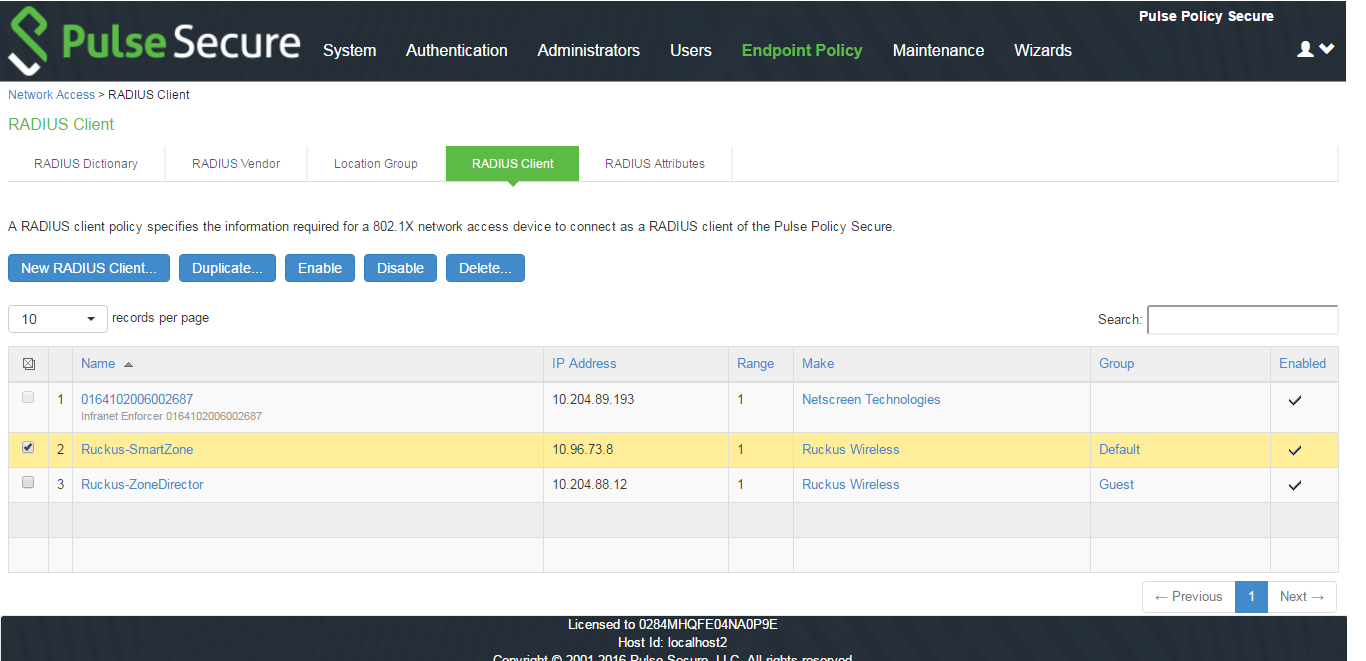
Select Endpoint Policy > Network Access > RADIUS Client.
-
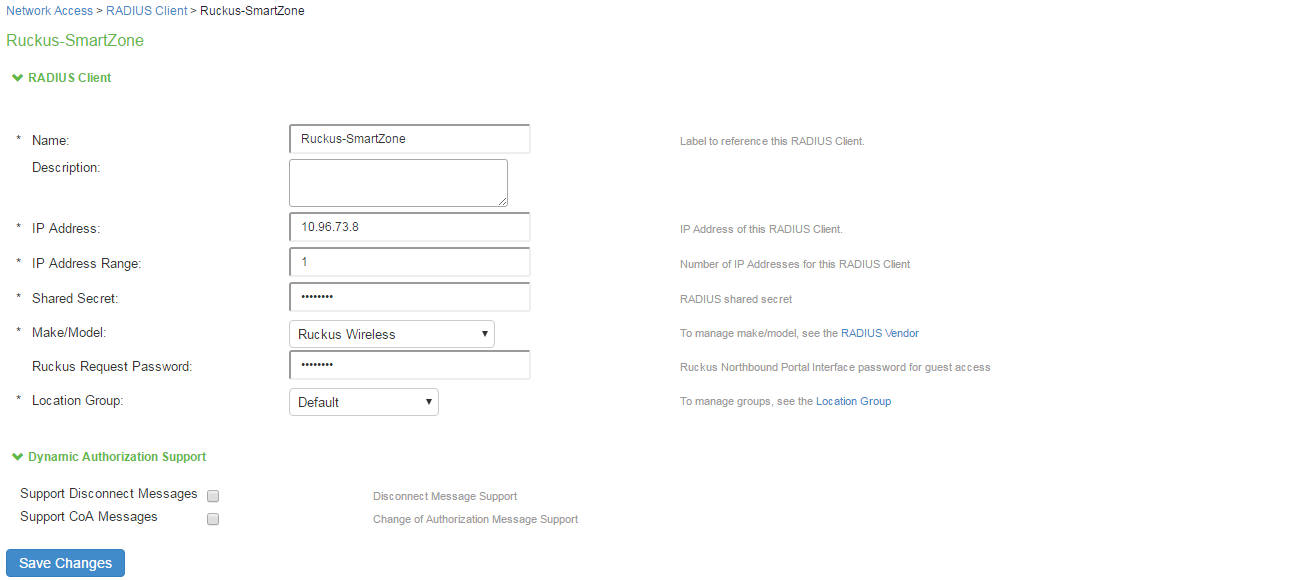
Enter the Name, IP Address, Shared Secret and Make model as Ruckus Wireless.
-
Here Ruckus Request password should be the same which is configured in “NorthBound Polar Interface” of SmartZone WLC and select default location group.