Configuring Splunk Enterprise
Install Ivanti Policy Secure Alert Add-On for Splunk
Download the ps-pps-9.1R3-splunk-alertaddon.tar.gz file from Ivanti software downloads location and install them onto your Splunk server.
To configure the Ivanti Policy Secure App:
-
Log into Splunk as an Admin user.
-
In the Splunk Enterprise Dashboard, select the Admin tab > Manage Apps.
-
Select Apps > Upload App
-
Click Browse and upload the Pulse-Policy-Secure.zip file to install the Ivanti App for Splunk.
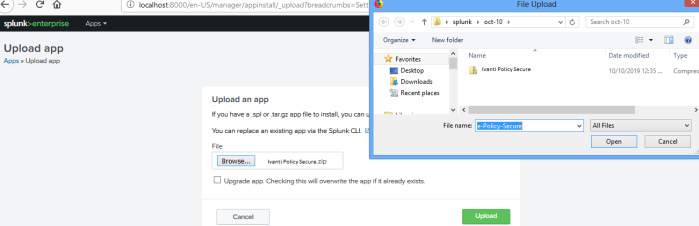
For upgrading the existing Ivanti Policy Secure app, select the upgrade app. Checking this will overwrite the app if already exists option.
-
After installation, Pulse Policy Secure Alert Add-On for Splunk appears in the App section
-
Select the Pulse Policy Secure Alert Add-On for Splunk Icon.
-
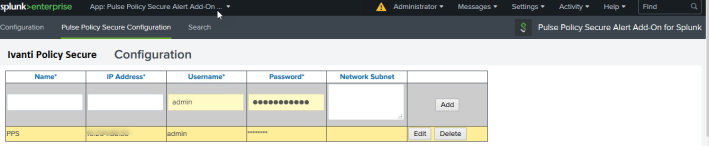
Enter the name, Ivanti Policy Secure IP address, user name, network subnet to send alerts/action. Click Add.
-
Click Save.
Alert Action Based on Source IP/MAC Address
SIEM provides live streaming of the processed events and flows. SIEM admin live monitors these log and network activity. Expert SIEM admin can identify the malicious host by monitoring these data. Ivanti application provides an option for the SIEM admin to take action for such host based on IP Address even if these are not listed under alerts.
-
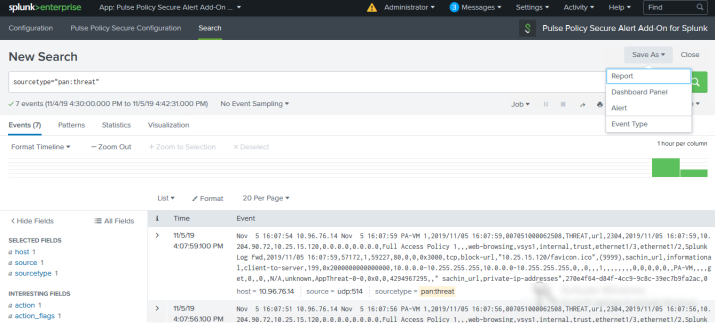
In the Ivanti Alert Add-on App for Splunk, run a search.
-
Under the Pulse Policy Secure Alert Add-On for Splunk logo select Save As and then Alert.
-
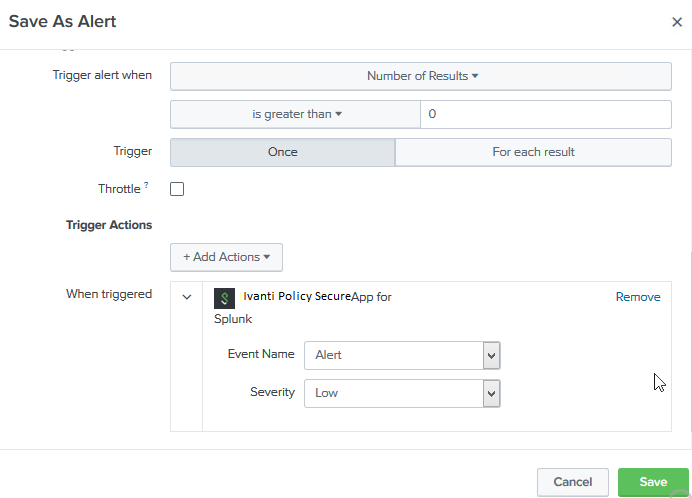
The Save As alert dialog opens.
-
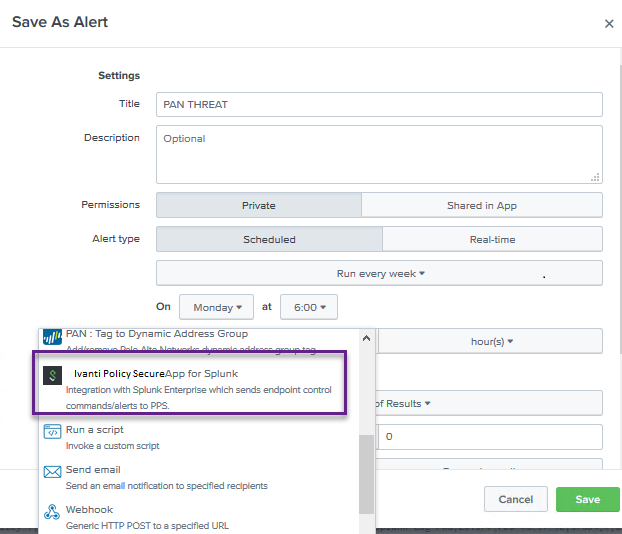
Define the schedule and trigger conditions.
-
In the Trigger Actions section, select Add Actions and then select Pulse Policy Secure App for Splunk.
-
Specify the Event Type and the severity and click Save.
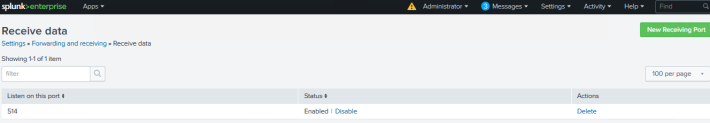
Enable port 514 from Settings > Forward and receiving> Receive Data.
For more information on Splunk configuration, see Splunk documentation.