Configuring EX switch with Ivanti Policy Secure
The EX Series switch serves as a policy enforcement point. Ivanti Policy Secure sends auth table entries and resource access policies when an endpoint successfully completes 802.1X authentication or MAC authentication (unmanaged devices). Access for any endpoint is governed by the resource access policies that you configure on Ivanti Policy Secure. Because resource access policies are employed, firewall filters are not required for the EX Series switch configuration.
Configuring EX switch as an Infranet Enforcer
The EX-series switches will permit or deny network access based on policies developed and distributed by Ivanti Policy Secure, including those policies based on user authentication status, endpoint posture compliance, user/device role and other policies. The EX-series switches provide standards-based 802.1X port-level access control.
To configure a Juniper EX switch as an Infranet Enforcer in Ivanti Policy Secure:
-
Select Endpoint Policy > Infranet Enforcer.
-
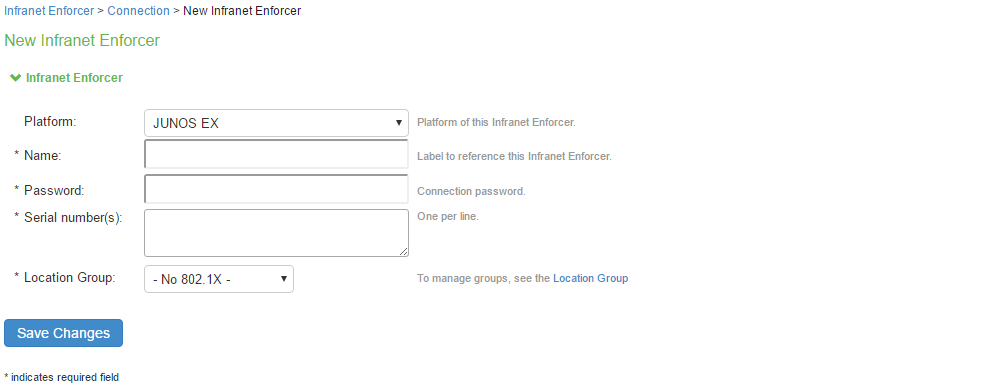
Click New Infranet Enforcer and select Junos EX in the Platform drop down.
-
Enter the name of the EX Series switch in the Name box.
-
Enter the password for the EX Series switch. This password is a shared secret that administrators of both the switch and Ivanti Policy Secure can use for connectivity between the two devices.
-
Enter the serial number of the EX Series switch.
-
Select the location group.
-
Click Save Changes.
On the EX Series switch, you use the CLI to configure the connection with Ivanti Policy Secure.
Configuring an Authentication Table
The EX Series switch receives and maintains auth tables for valid user sessions with Ivanti Policy Secure. An auth tables consist of a unique identification number, the MAC address of the endpoint that initiated the session, and a list of roles that the user has been assigned.
Auth tables are sent from Ivanti Policy Secure to the EX Series switch when a user is authenticated on the network.
Always Provision and Never Provision Auth table mapping policies are supported for the EX Series switch.
For complete configuration information, see Configuring Auth Table Mapping Policies.
Configuring Resource Access Policy
Using resource access policies with an EX Series switch you can configure authorization for protected resources. If you have configured the EX Series switch as an Infranet Enforcer, select the switch in the resource access policy.
A resource is a single entry in the resource field of the resource access policy. This could be a MAC address, or it could be a combination of IP address ranges, ports, and protocol. A filter term is the access/deny detail for a single resource. The number of terms you can configure per firewall filter will vary, depending on which EX Series switch you are configuring. The below table shows the number of terms allowed per firewall filter for different EX Series switches.
If you create resource access policies with the number of resources greater than the maximum number of filter terms allowed, the filter is not installed, and 802.1X authentication fails.
|
EX Switch |
Number of Terms Allowed |
|---|---|
|
EX2200 switch |
512 |
|
EX3200 and 4200 switches |
7,042 |
|
EX4500 switch |
1,536 |
|
EX8200 switch |
32,768 |
|
EX3300 switch |
1,436 |
|
EX6200 switch |
1,400 |