Troubleshooting
To verify the event logs on Ivanti Policy Secure:
Select System > Log/Monitoring > Events.
You can verify that the event logs are generated every time when an event is received from Juniper Policy Enforcer.
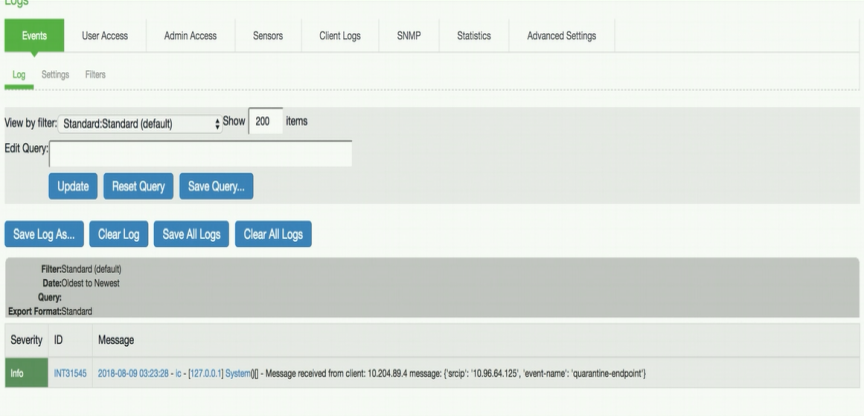
To verify the user access logs:
Select System >Logs & Monitoring > User Access to verify the user login related logs like realm, roles, username and IP address.
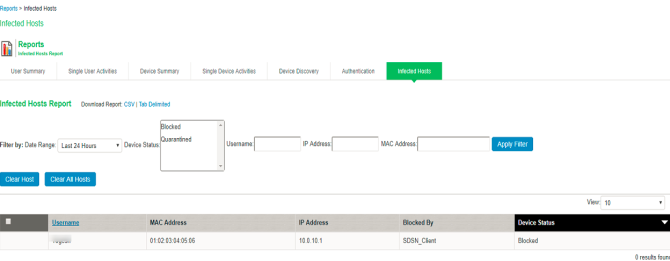
You can also verify whether the quarantined/blocked host is listed in the Infected Devices report, which lists the mac address, IP address, and the device status. To verify the reports, select System > Reports > Infected Hosts.
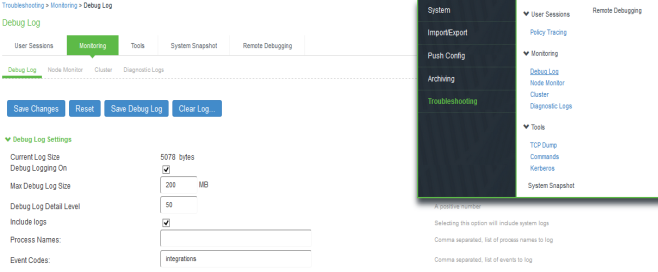
You can also enable debug logs to troubleshoot any issues.
Select Maintenance > Troubleshooting > Monitoring > Debug Log to enable debug logs.
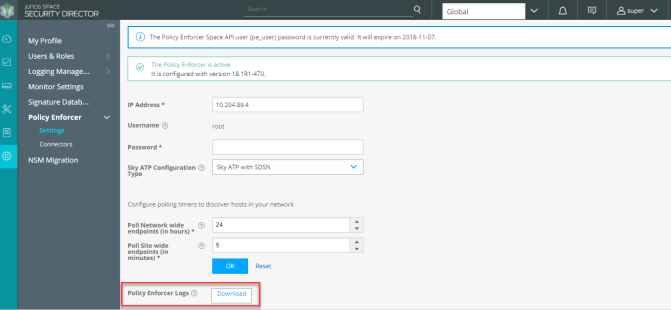
For any issues on the Policy Enforcer, you can download and verify the Policy Enforcer logs from Junos Space Security Director, Policy Enforcer > Settings page.
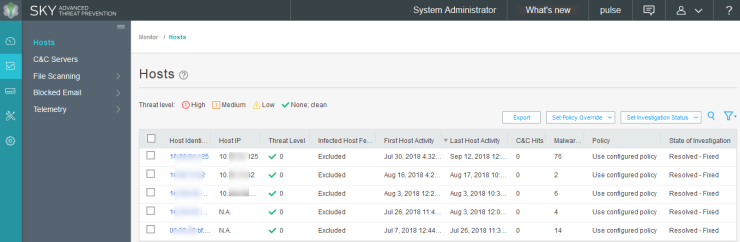
The Administrators can also verify the Hosts table from Sky ATP to check the status of the host. You can clear the host entry if the state of investigation is resolved-fixed.