Ivanti Connect Secure Admission Control Using Ivanti Policy Secure
Admission control feature is extended to Ivanti Connect Secure sessions using IF-MAP server. When Firewall/SIEM detects compromised remote devices the Firewall/SIEM sends threat alert to Ivanti Policy Secure. Ivanti Policy Secure then instructs Ivanti Connect Secure to act (For example, terminate session, change roles, disable user account) based on the configured admission control policies.
This section explains how Ivanti Policy Secure can receive alerts from remote users and provide an action to Ivanti Connect Secure (remote) based on the configured admission control policies. This feature is supported for the admission control clients, which alerts Ivanti Policy Secure with VPN Tunneling IP address of endpoints. VPN Tunneling IP Address of the user is mandatory in the received alert/message to identify the user session.
This feature is supported for the admission control clients, which alerts Ivanti Policy Secure with VPN Tunneling IP address of endpoints. VPN Tunneling IP Address of the user is mandatory in the received alert/message to identify the user session.
The below set of actions can be performed on Ivanti Connect Secure sessions based on the configured policies:
-
Ignore (only log): Received event details are logged and no specific actions are taken.
-
Terminate the session: Terminate the user session on the Ivanti Connect Secure for the received messages.
-
Disable the user account: Disable the user on the Ivanti Connect Secure for the received messages.
-
Change user roles: Change the roles assigned to the user on Ivanti Connect Secure so that restriction/privileges for the user can be changed.
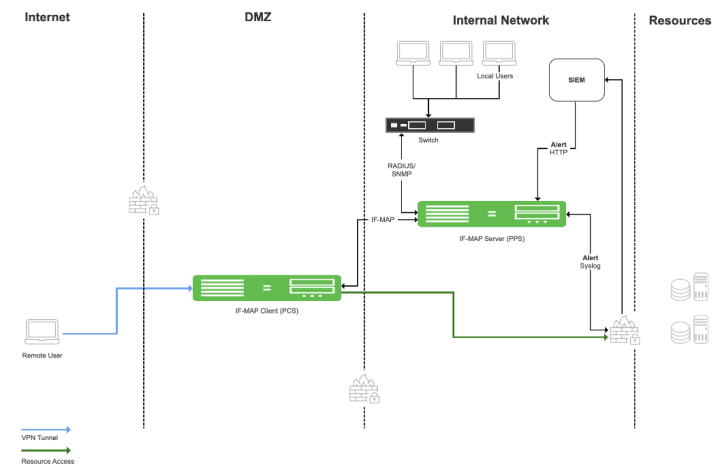
The end user flow is described below:
- Remote user logs in and the user session is created on Ivanti Connect Secure.
- User session is exported to IF-MAP server (Ivanti Policy Secure) as fed-wide session.
- User accesses resources and performs a restricted action. For example, accesses a restricted site. The firewall device detects this as a threat and a corresponding event is generated and sent to the Ivanti Policy Secure.
- Ivanti Policy Secure looks for the local session if it is available and applies the action based on the policy configured.
- If local session is not available and if Enable Admission Control on Federation-Wide Sessions is enabled, then the policy applies on the fed-wide session.
- Ivanti Connect Secure IF-MAP client takes the action on local session based on the policy configured.
Configuring Ivanti Connect Secure Admission Control
-
Administrator configures the required admission control client (like firewalls, SIEMs, EPP etc.) on Ivanti Policy Secure Admin UI to receive alert/threat information.
-
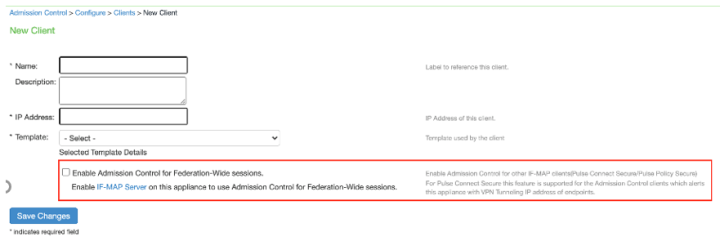
Select Endpoint Policy > Admission Control > Configure > Clients > New Client.
-
Enable Admission Control on Federation-Wide Sessions.
-
Administrator configures a set of policies that define what actions are to be taken on user sessions, based on the data in the threat events.
-
On Ivanti Policy Secure Admin UI and Ivanti Connect Secure Admin UI, administrator enables IF-MAP server under System > IF-MAP > Overview.
-
On Ivanti Connect Secure Admin UI, administrator enables IF-MAP client under System > IF-MAP > Overview and add IF-MAP server url. Once configured, Ivanti Connect Secure (IF-MAP client) connects to IF-MAP server (Ivanti Policy Secure).
9.1R12 or later build is required for both Federation client and Fed server to use this feature.
Admission Control is supported with the following vendors:
- Palo Alto Networks Firewall
- Check Point Next Generation Firewall
- McAfee ePO Server