Configuring Ivanti Policy Secure for Session Bridging
Configuring Mac OS X Native Supplicant for Ivanti Policy Secure 802.1X Authentication
This section details the procedure for configuring native Mac OS X supplicant for Ivanti Policy Secure 802.1X authentication.
Requirements:
- Apple Mac OS X endpoint
- iPhone Configuration utility
- Client certificate must be installed on Mac OS X endpoint
Configuring MAC OS X Native Supplicant
Authentication to a Ivanti Policy Secure 802.1X server in MAC OS X endpoints is achieved using Apple Configurator. This tool allows you to easily create, maintain, and install configuration profiles, track and install provisioning profiles, and capture device information including console logs.
The latest MAC OS X endpoints can be configured using Apple Configurator 2 tool.
Configuring 802.1x profile
You can create various profiles (TTLS/PAP, TTLS/MS-CHAP-V2, and PEAP/MS-CHAP-V2) required for Ivanti Policy Secure 802.1x authentication using Apple Configurator. The generated configuration profiles can be exported to a Mac OS X endpoint. To create profiles, install the profiles (by double clicking on the exported files) on their OS X endpoints and that will provision Layer 2 access when connected to 802.1x enabled switch port.
Configuring 802.1x profiles -PEAP applies only for General and Wi-Fi settings. If the authentication server is Certificate Auth Server, use EAP-PEAP/EAP-TLS.
Configuring PEAP Authentication Profile
To configure PEAP, perform the following:
-
On the iPhone configuration utility (IPCU) navigate to Configuration Profiles tab.
-
On configuration Profiles page, select General and enter the required values.
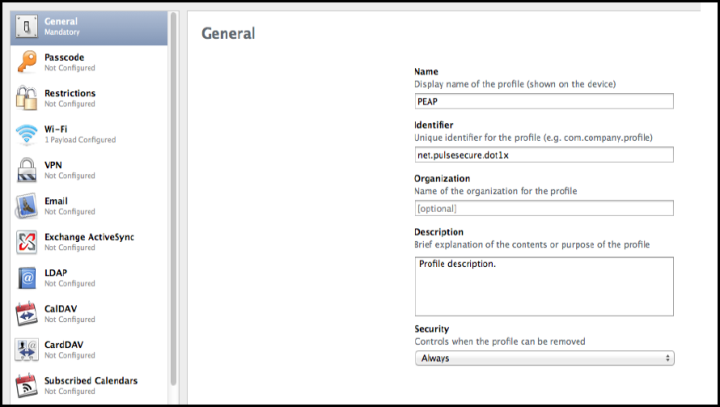
-
Select Wi-Fi and enter the required values. Ensure TLS/PEAP are selected under Accepted EAP types.
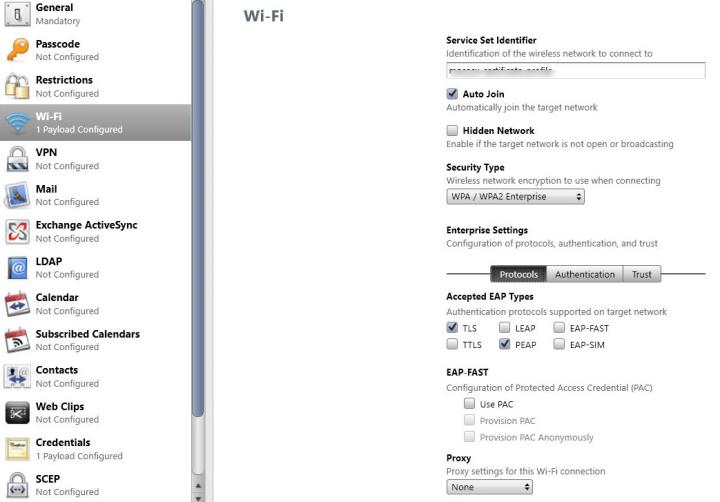
Once the profile is successfully imported, you see the below screen shot.
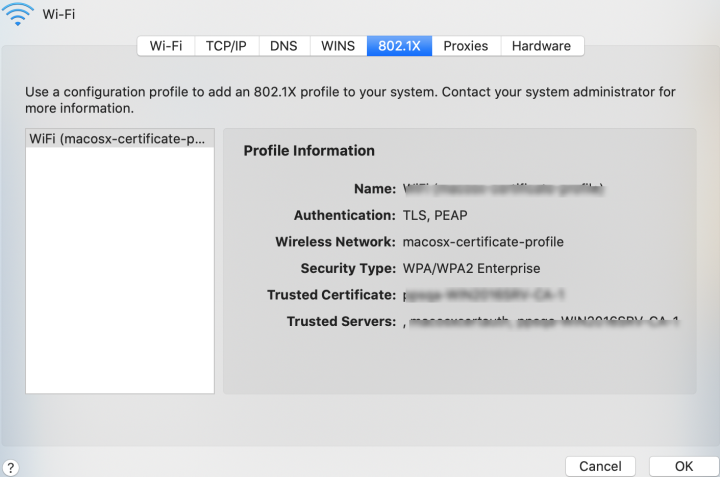
Configuring Ivanti Policy Secure
To configure Ivanti Policy Secure for guest wireless authentication:
-
Select System > Configuration > Certificates > Trusted Client CAs. Install the certificate from the CA that Ivanti Policy Secure is using for trusted Client CAs.
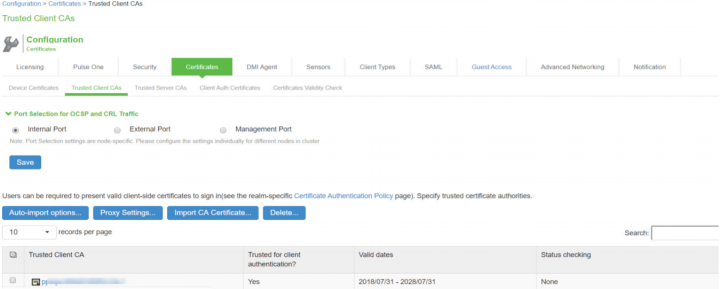
-
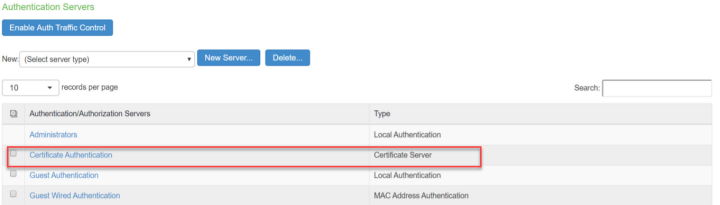
Select Authentication > Auth.Servers. The Authentication Servers screen appears. Use the Default Certificate Authentication Server.
-
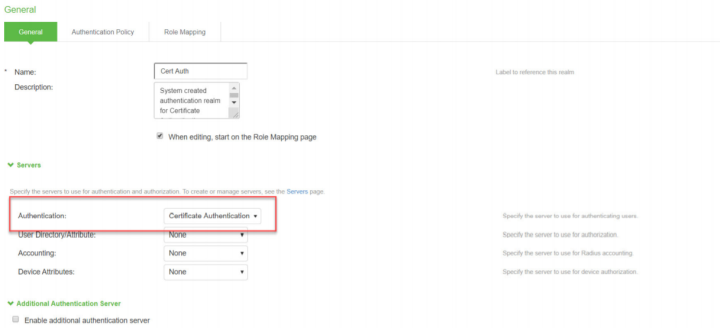
Select Users > User Realms, Click Cert Auth realm available by default to view the settings. Under Servers, Select the Certificate Authentication server.
-
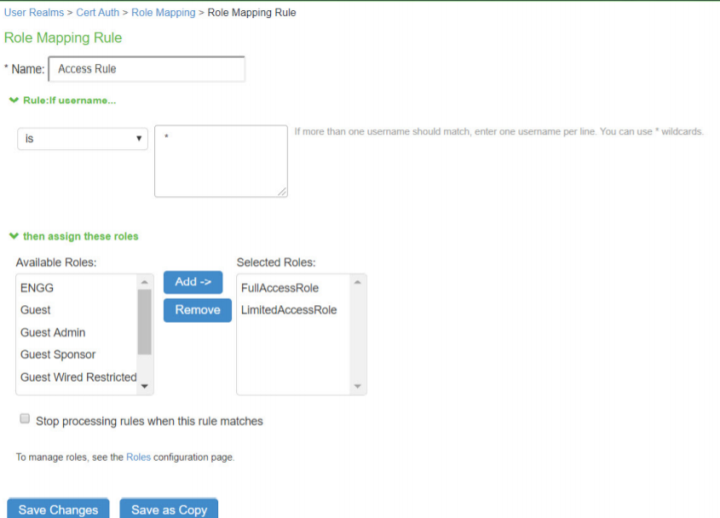
Create Role Mapping rules to associate with the roles.
-
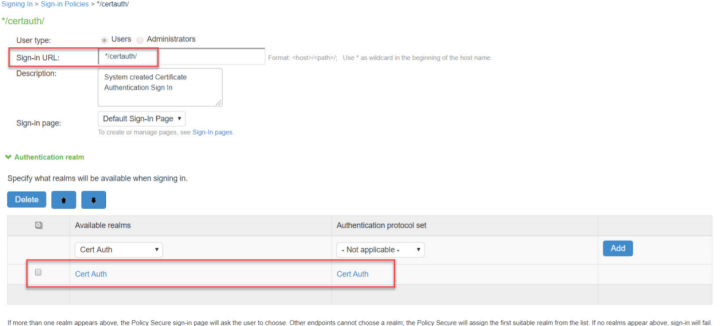
Selecting Authentication > Signing In > Sign-In Policies. Associate the default Cert Auth authentication protocol set with the realm.
-
Select Endpoint Policy > Network Access > Location Group. Select the default */certauth/ sign-in policy.
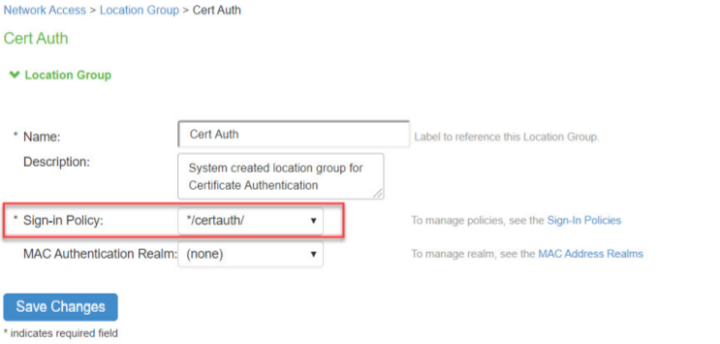
-
Configure the RADIUS client. Ensure that the default Cert Auth location group and Support Disconnect Messages and Support CoA Messages options are enabled.
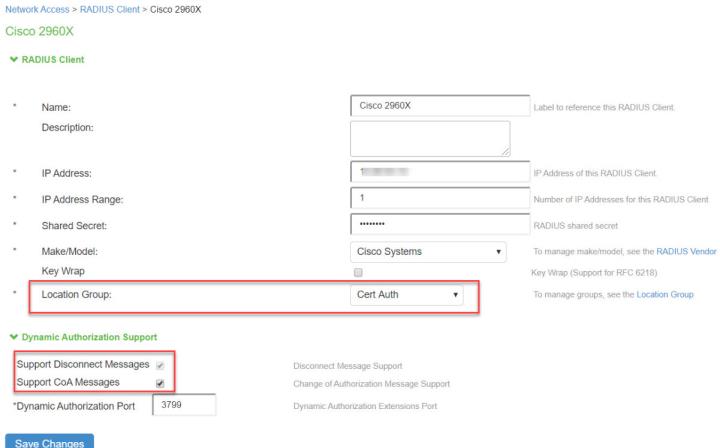
-
Configure the RADIUS return attributes for Guest Wired policy. Select Endpoint Policy > Network Access > RADIUS Return Attribute Policies. Click New Policy. Under RADIUS Attributes tab, select the check box for Return Attribute.The RADIUS return attributes are required for MAB authentication initially when the user connects to the SSID (where the redirection happens) and then the session is bridged after the user authenticates.
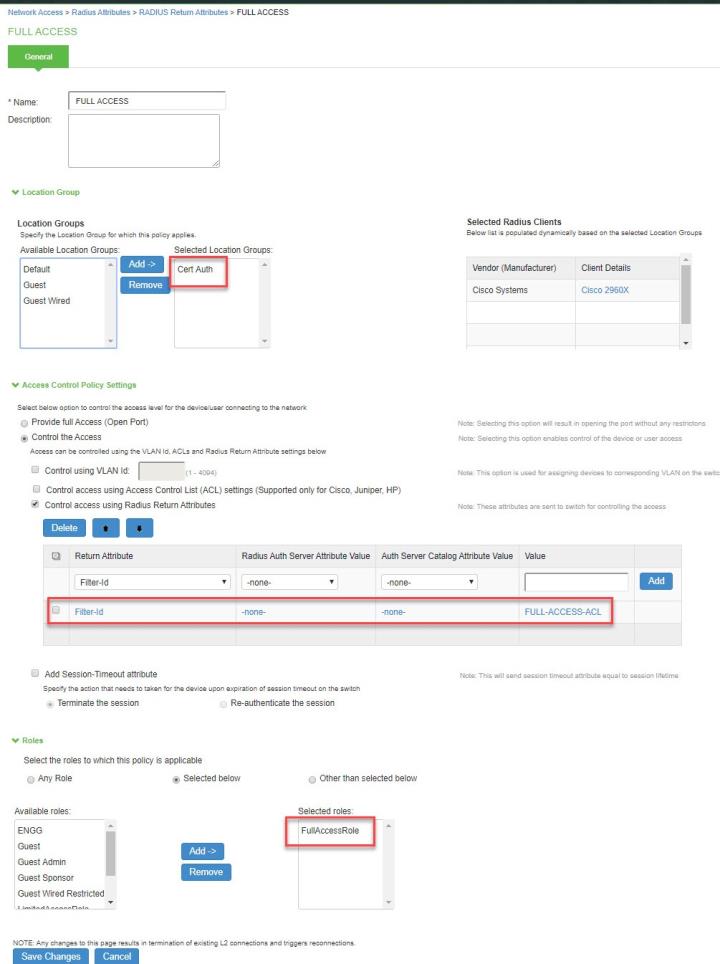
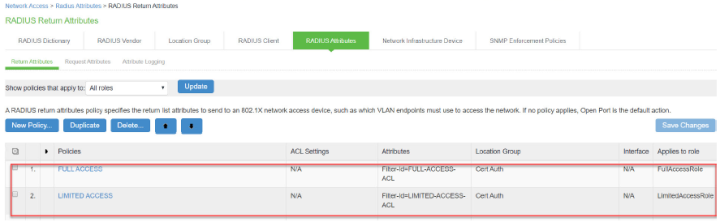
Configuring Cisco Switch
CLI command to configure session bridging on Cisco switch. The switch configuration varies for each switch type.
Run the show run command on your switch to ensure that your access interface connections are set up.
aaa accounting network default start-stop group PPS-QA
aaa accounting Identity default start-stop broadcast group PPS-QA
aaa accounting send stop-record authentication failure
aaa accounting update periodic 3
!
aaa server radius dynamic-author
client PPS-SERVER server-key 7 000E06080D4B0E14
server-key 7 051B150A22595C0C
port 3799
ignore session-key
ignore server-key
!
radius server PPS-SERVER
address ipv4 <IPS-SERVER-IP> auth-port 1812 acct-port 1813
key 7 1315021E1809557878
radius-server attribute 6 on-for-login-auth
radius-server attribute 8 include-in-access-req
radius-server attribute 32 include-in-access-req
radius-server attribute 55 include-in-acct-req
radius-server attribute 25 access-request include
radius-server dead-criteria time 2 tries 5
radius-server retransmit 3
!
aaa group server radius PPS-QA
server name PPS-SERVER
!
!
aaa local authentication PPS-QA authorization PPS-QA
aaa new-model
aaa session-id common
Extended IP access list FULL-ACCESS-ACL
10 permit ip any any
Extended IP access list LIMITED-ACCESS-ACL
10 permit ip any host <IPS IP>
20 permit ip any host <PATCH-MGMT-SERVER>
30 permit udp any any eq domain
40 permit tcp any any eq domain
50 permit udp any eq bootps any
60 permit udp any any eq bootpc
70 permit udp any eq bootpc any
80 deny ip any any
Troubleshooting
For troubleshooting you can verify the user access logs.
“Agent session bridged for macuser/Cert_Realm from 10.20.30.40 with Junos-Pulse9.1.2.xxxx (Macintosh) Pulse/9.1.2.xxxxx”