Certificate Authentication Support
This feature enables users to login to the client using their certificates. The supported scenario is “certificate-based login only" the Ivanti Secure Access Client setup is now switched to this authentication method. In a typical enterprise environment, each user will be provided with certificate which can be used for VPN login. This mechanism can be used only as a primary authentication mechanism.
Configuring Client Certificate in Ivanti Connect Secure
To configure trusted client CA certificate:
1.Select System > Configuration > Certificates > Trusted Client CAs.
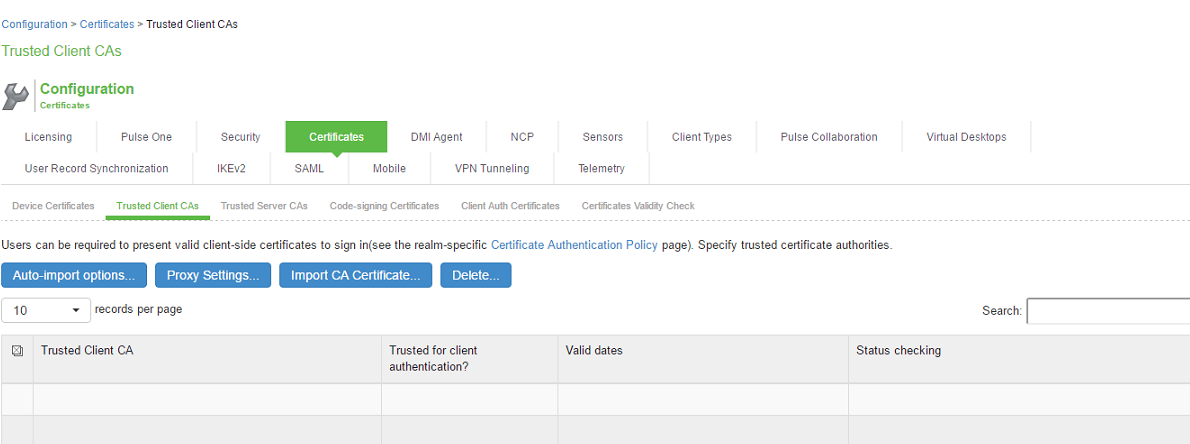
2.Click Import CA Certificate to display the configuration page.
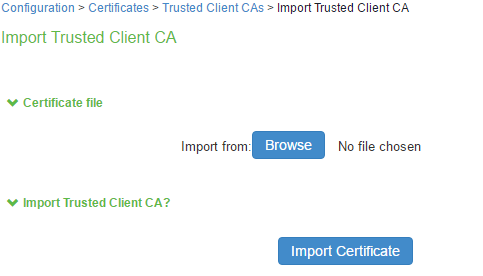
3.Browse to the certificate file and select it.
4.Click Import Certificate to complete the import operation.
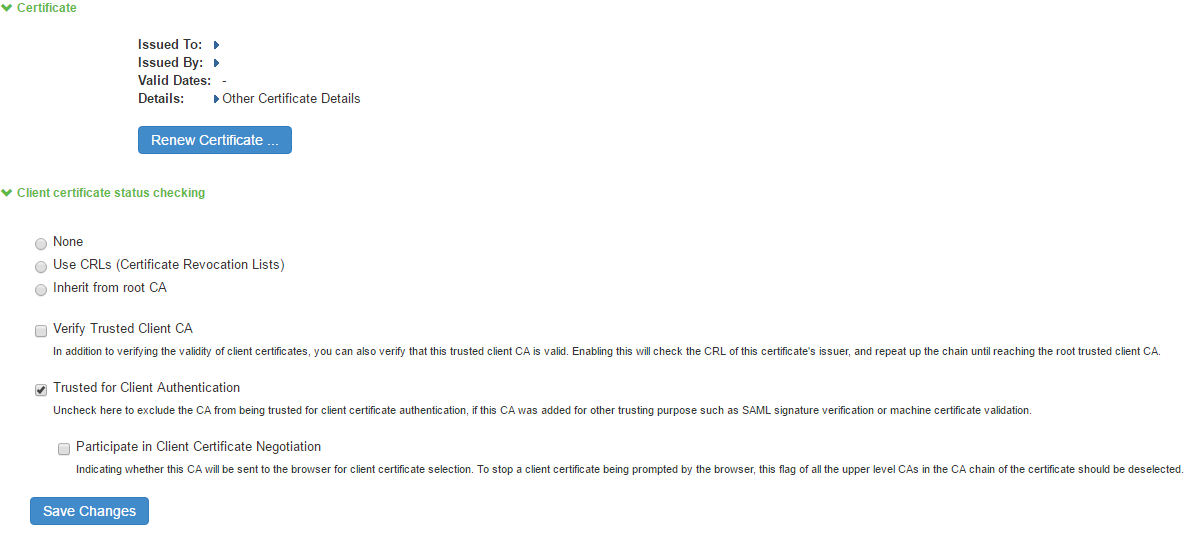
5.Click the link for the Trusted Client CA to configure.
Configuring Authentication with the Certificate Server
To configure authentication with the certificate server, follow the steps below:
1.Select Authentication > Auth Servers.
2.Select Certificate Server and Click New Server to display the configuration page.
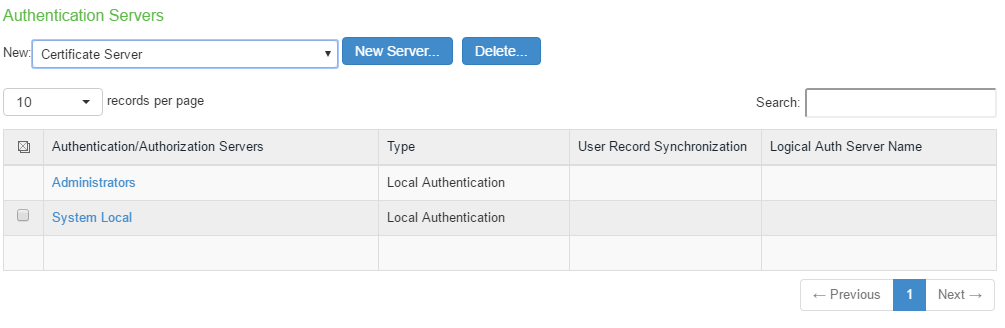
3.Complete the configuration as described in following table:
|
Settings |
Guidelines |
|
Name |
Specify a name to identify the server within the system |
|
User Name Template |
Specify a username template. Specify how the system should construct a username. You may use any combination of certificate variables contained in angle brackets and plain text. NOTE: This value populates the <USER> and <USERNAME> session variables for use throughout the rest of the system configuration. |
|
User Record Synchronization |
This applies only to Connect Secure. |
|
Enable User Record Synchronization |
Select this option to retain the bookmarks and individual preferences regardless of which system you log in to. |
|
Logical Auth Server Name |
Specify a logical authentication server name. |
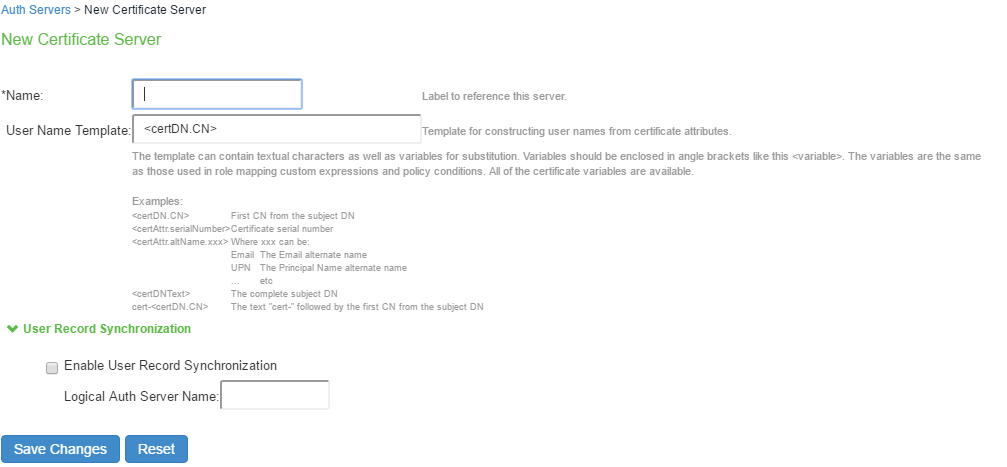
4.Save the configuration.
Client Certificate Installation
The installation of the certificates can be facilitated through a script. Client certificates can be installed using util script “certificate_installer.sh”. Use the following commands to install or delete the certificates:
•To install the certificate:
/opt/pulsesecure/bin/certificate_installer.sh install_certificates [-inpfx < PFX /P12 file >] [-inpriv <private file> -inpub <public file>]
Password is required to install private and public keys separately.
•To list the certificates on the certificate store
/opt/pulsesecure/bin/certificate_installer.sh list_installed_certificates
•To delete the Certificate from certificate store
/opt/pulsesecure/bin/certificate_installer.sh delete_certificates -certName <certificate name>
To delete certificates from CEF certificate store:
/usr/bin/certutil -d sql:/ /$HOME/.pki/nssdb -D -n <Nickname>
where, 'Nickname' is available in list of installed certificates
Public Certificates
|
Extensions |
Certificate Formats |
|
der, cer |
DER |
|
pem, crt, key, pub |
PEM |
Private Keys
|
Extensions |
Certificate Formats |
|
der, cer |
DER |
|
pem, crt, key |
PEM |
PFX file (Contains both Private Key and Public Keys)
|
Extensions |
Certificate Formats |
|
Pfx, p12 |
PFX |
Default Certificate Selection
If multiple certificates are available for a connection, the certificates list allows the user to select the certificate and authenticate to establish the connection.
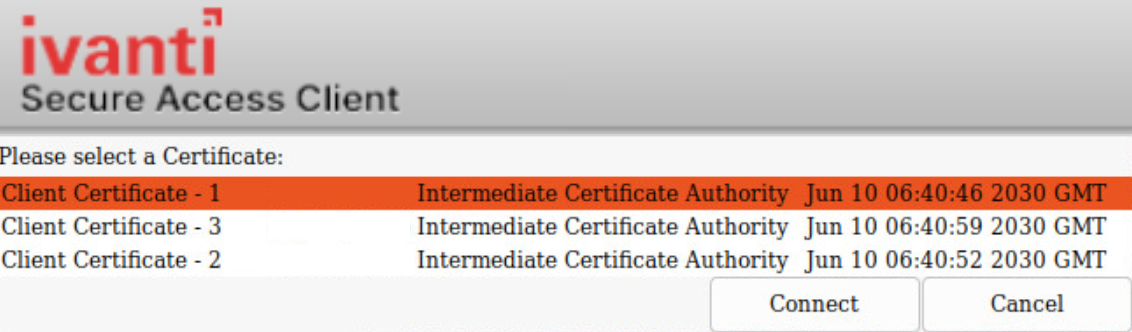
Client certificate authentication through smart cards is not supported.