Credential Provider Authentication for Ivanti Connect Secure Overview
When Microsoft introduced Windows Vista, it moved away from a login integration interface based on GINA (Graphical Identification and Authentication) in favor of credential provider authentication. Ivanti Secure Access Client credential provider integration enables connectivity to a network that is required for the user to login to the Windows domain. For example, the domain controller might reside behind a firewall and the endpoint uses credential provider login to connect to Ivanti Connect Secure prior to domain login. Ivanti Secure Access Client integrates with Microsoft credential providers to enable password-based login and smart card login. Credential provider login is supported on Windows 8.1 and later Windows platforms.
You can use Ivanti Secure Access Client’s support for credential provider to provide single sign-on capabilities. Ivanti Secure Access Client establishes a connection to the network and then uses the same credentials to login the Windows domain.
You enable Ivanti Secure Access Client credential provider support on a Ivanti Secure Access Client connection, (connection type UAC 802.1X (UAC) or SSL VPN (L3)). After the connection has been downloaded to the endpoint through the normal Ivanti Secure Access Client distribution methods, Ivanti Secure Access Client annotates the credential provider tile that appears on the user login screen by adding a Ivanti Secure Access Client icon in the lower right corner of the tile.
Ivanti Secure Access Client supports the following credential provider types:
•user-at-credprov: The connection is established before the user login using credentials collected at the selected credential tile, which provides single-sign-on functionality. The connection is maintained as an active connection on the user’s desktop.
•machine-then-user-at-credprov: The connection is established using machine credentials when no user is logged in. When a user clicks a login tile and provides user credentials, the machine connection is disconnected and a new connection is established. When the user logs out, the user connection is disconnected and the machine connection is reestablished. In one typical machine-then-user-at-cred prov implementation, the machine connection and the user connection are mapped to different VLANs.
Ivanti Secure Access Client credential provider support usage notes:
•If the endpoint includes more than one Ivanti Secure Access Client Layer 2 connection, Windows determines which connection to use:
1.If a network cable is attached to the endpoint, Layer 2 wired connections are attempted, and then wireless connections. If there is more than one wireless network available, the order is determined by the scan list specified as a Ivanti Secure Access Client connection option.
2.After all Layer 2 options are attempted, Ivanti Secure Access Client runs location awareness rules to find one or more eligible Layer 3 connections that are configured for credential provider login. If more than one Layer 3 connection is found, Ivanti Secure Access Client prompts the user to select a connection. A user can cancel the network connection attempt by clicking the cancel button.
3.After Ivanti Secure Access Client evaluates all configured connection options, Ivanti Secure Access Client returns control to Windows, which enables the user login operation.
•For connections that use user credentials, the Ivanti Secure Access Client connection can be configured so that prompts are presented during the login process, for example, prompts for realm or role selection or a server certificate trust prompt. For connections that use machine credentials, Ivanti Secure Access Client prompts cause the connection to fail because there is no interface to allow a response to the prompts. You can suppress any potential realm and role choice by specifying a preferred realm and role for the connection.
•Ivanti Secure Access Client upgrade notifications and actions are disabled during credential provider login and postponed until the user connection is established. Host Checker remediation notifications are displayed.
Configuring Role Options for Ivanti Connect Secure
All of the options for role configuration tabs are described in User Access Management Framework Feature Guide.
To configure role options for Ivanti Secure Access Client endpoints:
1.From the Ivanti Connect Secure admin console, select Users > User Roles.
2.Click the role you want to configure and then click the VPN Tunneling tab.
3.Under "Split Tunneling Options", select your options:
General VPN Options apply to all Layer 3 VPN clients, Ivanti Secure Access Client (Windows, OS X, iOS, and Android), Network Connect, and third-party IKEv2 clients:
•Split Tunneling: Split tunneling options let you define how network traffic flows on the client.
•Enable: Ivanti Secure Access Client modifies routes on the client so that traffic meant for the corporate intranet uses the virtual adapter created by Ivanti Secure Access Client (the Ivanti Secure Access Client tunnel) and all other traffic goes through the local physical adapter.
•Disable: When the client session is established, predefined local subnet and host-to-host routes that might cause split-tunneling behavior are removed, and all network traffic from the client goes through the Ivanti Secure Access Client tunnel. With split tunneling disabled, users cannot access local LAN resources during an active VPN session. However, when you create a Ivanti Secure Access Client connection for users, if you allow users to override you can enable an option that allows the user to suspend their VPN connection. While a Ivanti Secure Access Client connection is in the suspended state, all traffic goes through the local physical adapter.
Ivanti Secure Access Client options apply only to Ivanti Secure Access Client and Network Connect:
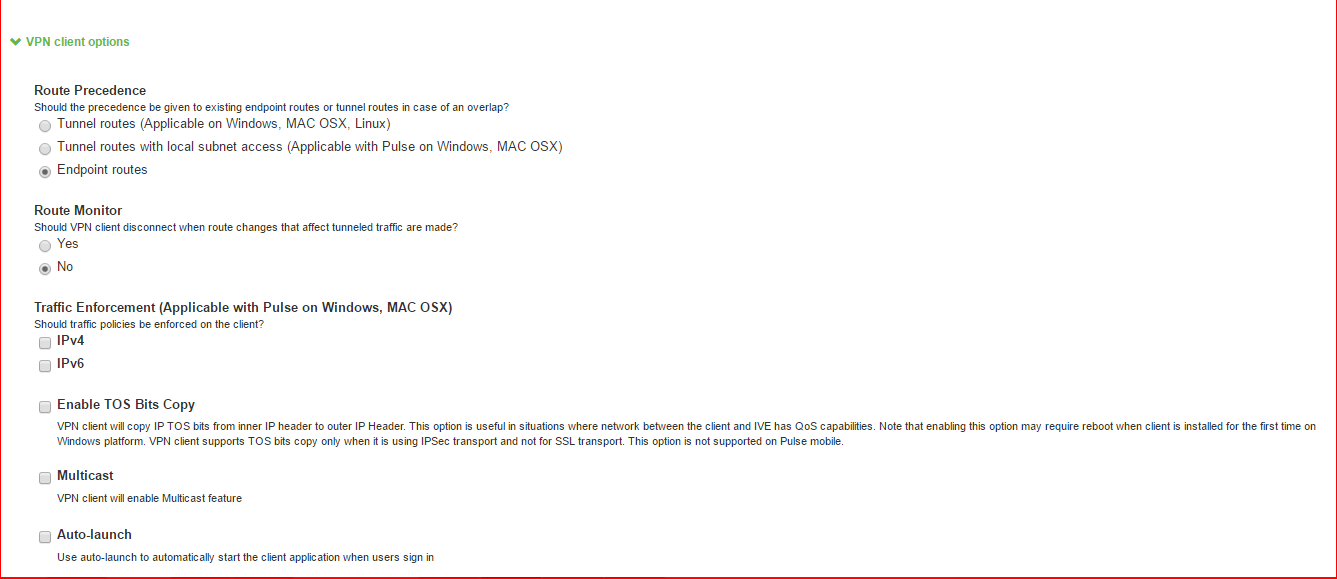
•Route Precedence: You can define which routing table takes precedence:
Tunnel Routes: The route table associated with the Ivanti Secure Access Client virtual adapter takes precedence. Ivanti Secure Access Client overwrites the physical interface routes if there is conflict between the Ivanti Secure Access Client virtual adapter and the physical adapters. Ivanti Secure Access Client restores the original routes when the connection is ended.
Tunnel Routes with local subnet access (Ivanti Secure Access Client on Windows and macOS only): Network traffic addressed to the networks defined in the split tunnel resource policies goes through the VPN tunnel. Network traffic that is addressed to the directly-connected (local) subnet goes to the local subnet. The default route is set to the local subnet so all other network traffic is subject to the original endpoint routing table.
Endpoint Routes: The route table associated with the endpoint’s physical adapter take precedence.
Route Monitor: Ivanti Secure Access Client can monitor the route tables and take appropriate action.
Yes: VPN tunneling ends the connection only if the route change affects the VPN tunnel traffic. For example, if the route metric is changed higher, it should not disconnect VPN tunneling.
No: Route tables are allowed to change on the client endpoint.
•Traffic Enforcement: When Traffic Enforcement is enabled, Ivanti Secure Access Client creates rules on the endpoint’s firewall (macOS and Windows) that ensure that all traffic conforms to the Ivanti Connect Secure tunnel configuration.
A local program might bypass the endpoint’s routing tables and bind traffic to the physical interface instead of allowing it to go through the Ivanti Secure Access Client virtual interface. If you enable traffic enforcement, you ensure that all traffic is bound by the Ivanti Connect Secure tunnel configuration.
IPv4: When this check box is selected all IPv4 traffic is bound by the Ivanti Connect Secure tunnel configuration.
IPv6: When this check box is selected all IPv6 traffic is bound by the Ivanti Connect Secure tunnel configuration.
Typically, if you wanted to enable traffic enforcement, you enable both options. Enabling only one option is useful for nested tunnel (tunnel-in-tunnel) configurations. See the Ivanti Secure Access Client Supported Platforms Guide for supported nested tunnel configurations.
•Enable TOS Bits Copy: Enables you to control the client behavior in networks that employ Quality of Service (QoS) protocols. When you enable this check box, Ivanti Secure Access Client copies IP Type of Service (TOS) bits from the inner IP header to outer the IP Header. Note that enabling this option might require a reboot of the client endpoint when Ivanti Secure Access Client software is installed for the first time on Windows endpoints. Ivanti Secure Access Clients support TOS bit copy only for IPSec transport and not for SSL transport.
•Multicast: Enables the multicast feature on Ivanti Secure Access Client when this option is selected.
•Auto-launch: Activates Ivanti Secure Access Client software automatically when the endpoint is started when this option is selected.
Options for Ivanti Secure Access Client on Windows apply only to Ivanti Secure Access Client and Network Connect on Windows endpoints:
•Launch client during Windows Interactive User Logon: When this option is enabled, Ivanti Secure Access Client starts when the user logs into Windows. Note that this setting is not the same as the Ivanti Secure Access Client connection settings that control machine authentication and credential provider authentication. Choose one of the following options:
Require client to start when logging into Windows
Allow user to decide whether to start client when logging into Windows
•Windows: Session start script: Specify a script (.bat, .cmd, or .exe) to run for users assigned to the role after Ivanti Secure Access Client connects with Ivanti Connect Secure. For example, you can specify a script that maps network drives on an endpoint to shares on protected resources.
•Windows: Session end script: Specify a script (.bat, .cmd, or .exe) to run for users assigned to the role after Ivanti Secure Access Client disconnects from Ivanti Connect Secure. For example, you can specify a script that disconnects mapped network drives. If there is no start script defined, or the start script has not been run, the end script does not run.
•Skip if Windows Interactive User Logon Enabled: Select this option to bypass the specified Windows session start script.
•If the client signs in to their Windows Domain via the Credential Provider automatic sign-in function, a script is executed by the Windows Ivanti Secure Access Client. In this case, the sign-in script might be identical to the specified VPN Tunneling start script. You can use this option, therefore, as a way to avoid executing the same script twice.
Options for Ivanti Secure Access Client on Mac apply only to Ivanti Secure Access Client and Network Connect on Apple OS X endpoints:
•Mac: Session start script: Specify a script (.bat, .cmd, or .exe) to run for users assigned to the role after Ivanti Secure Access Client connects with Ivanti Connect Secure. For example, you can specify a script that maps network drives on an endpoint to shares on protected resources.
•Mac: Session end script: Specify a script (.bat, .cmd, or .exe) to run for users assigned to the role after Ivanti Secure Access Client disconnects from Ivanti Connect Secure. For example, you can specify a script that disconnects mapped network drives. If there is no start script defined, or the start script has not been run, the end script does not run.
4.In the Session scripts area, optionally specify a location for the following:
•Windows: Session start script: Specify a script (.bat, .cmd, or .exe) to run for users assigned to the role after Ivanti Secure Access Client connects with Ivanti Policy Secure. For example, you can specify a script that maps network drives on an endpoint to shares on protected resources. The script must be in a location (either local or on the network) that is accessible by the user.
•Windows: Session end script: Specify a script (.bat, .cmd, or .exe) to run for users assigned to the role after Ivanti Secure Access Client disconnects from Ivanti Policy Secure. For example, you can specify a script that disconnects mapped network drives. If there is no start script defined, or the start script has not been run, the end script does not run. The script must be in a location (either local or on the network) that is accessible by the user.
5.Click Save Changes.