Endpoint Security Monitoring and Management for Ivanti Connect Secure
You can configure and enable Host Checker policies to perform an endpoint security assessment before allowing the endpoint to connect. Host Checker is supported on the following operating systems:
•Windows (including 8.1 and later versions of Windows RT and Windows Phone)
•macOS
•Google Android
•Apple iOS
You can invoke Host Checker at the role level or the realm level to specify access requirements for endpoints seeking authentication. Host Checker policies that are implemented at the realm level occur before the user is authenticated. Host Checker policies at the role level are implemented after authentication but before the user is permitted to access protected resources. When an endpoint first connects to Ivanti Connect Secure, the latest version of the IMC is downloaded to the host computer. The initial check can take 10-20 seconds to run. Outdated IMC files are automatically updated at subsequent checks.
The first time an endpoint connects to Ivanti Connect Secure that has a patch assessment policy, if the connection is a Layer 2 connection, the IMC cannot download. In this case, you should configure a remediation role that displays instructions to direct the user to retry with a Layer 3 connection or to contact the administrator.
If a realm has a Host Checker policy enabled that is for Ivanti Secure Access Clients, and a mobile device user employs a browser on the mobile device to connect to the Web portal, the login is denied because the desktop Host Checker program is not compatible with the mobile client OS. If Ivanti Secure Access Client mobile users are mapped to multiple roles, the login operation assigns them to a role where Host Checker is not enabled if possible. If all the roles have Host Checker enabled, the mobile users will not be allowed to login from the browser. You can create and enable Host Checker policies that are specific to each mobile operating system and then Host Checker runs when Ivanti Secure Access Client connects to the server.
For patch management on Windows systems, Host Checker uses a list of the most current patch versions from the vendor for predefined rules in the Host Checker policy. Host Checker does not scan for non-security patches. Server and Host Checker manage the flow of information between the corresponding pairs of TNC-based integrity measurement collectors (IMCs) and integrity measurement verifiers (IMVs). IMCs are software modules that run on the endpoint and collect information such as antivirus, antispyware, patch management, firewall, and other configuration and security information about the host. IMVs are software modules that run on the server and verify a particular aspect of a host’s integrity. Each IMV works with the corresponding IMC on Ivanti Secure Access Client to verify that the endpoint meets the Host Checker rules. IMCs scan the endpoint frequently for changes in security status. For example, if the user turns off virus checking, the IMC can detect this and then trigger a new check to make sure the modified system complies with the requirements of the Host Checker policy. You can configure Host Checker to monitor third-party IMCs installed on client computers by using third-party IMVs that are installed on a remote IMV server.
You obtain the most current patch version information from a Ivanti staging site. You can manually download and import the list into the Ivanti Connect Secure server, or you can automatically import the list from the Ivanti staging site or your own staging site at a specified interval.
Monitoring is based on one or more specified products or on specific patches, though not in the same policy. For example, you could check for Microsoft Edge with one policy, and Patch MSOO-039: SSL Certificate Validation Vulnerabilities with a second policy. Then, apply both policies to endpoints at the role or realm level to ensure that the user has the latest browser version with a specific patch. In addition, for Microsoft products, you can specify the severity level of patches that you want to ignore. For example, you could ignore low or moderate threats.
Remediation Options
Host Checker can identify issues on an endpoint. However, Host Checker and Ivanti Connect Secure cannot resolve issues, that is, perform remediation tasks, on non-compliant endpoints. To repair those issues Ivanti Connect Secure supports the following remediation options:
•Instructions to the user: The Ivanti gateway can send a message to the user describing the non-compliant patches or software and a link to where the user can obtain the required software. Endpoint Security Monitoring and Management for Ivanti Connect Secure shows a typical Ivanti Secure Access Client remediation message.
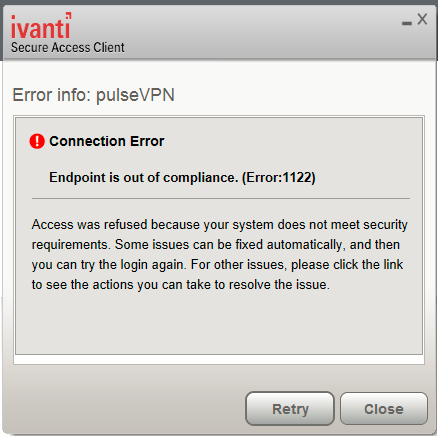
•Initiate SMS/SCCM remediation: For remediation using Microsoft System Center Configuration Manager (ConfigMgr or SCCM), formerly Systems Management Server (SMS), a preinstalled SMS/SCCM client on the endpoint is triggered by Host Checker to get patches from a preconfigured SMS/SCCM server. This mechanism installs only those patches that are published on the SMS/SCCM server.