Ivanti Connect Secure Split Tunneling Overview
Ivanti Secure Access Clients for Windows, Apple OS X, Google Android, and Apple iOS and the Ivanti Network Connect client all support split tunneling. Split tunneling is configured as part of the role that is assigned to a user after authentication. When Ivanti Secure Access Client and Ivanti Connect Secure establish a VPN tunnel, Ivanti Connect Secure takes control of the routing environment on the endpoint to ensure that only permitted network traffic is allowed access through the VPN tunnel. Split tunneling settings enable you to further define the VPN tunnel environment by permitting some traffic from the endpoint to reach the local network or another connected subnet. When split tunneling is enabled, split tunneling resource policies enable you to define the specific IP network resources that are excluded from access or accessible through the VPN tunnel.
Figure shows a simple network configuration with three possible routes: through the default router, to the local subnet, or to a router connection to an indirectly connected subnet.
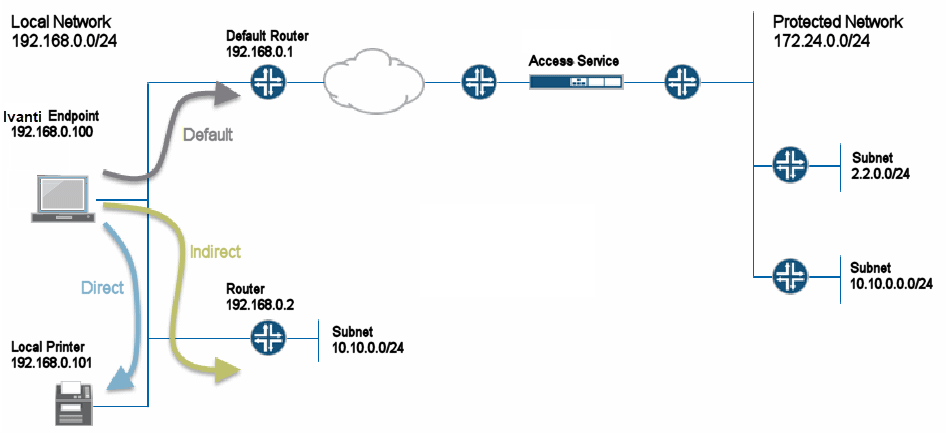
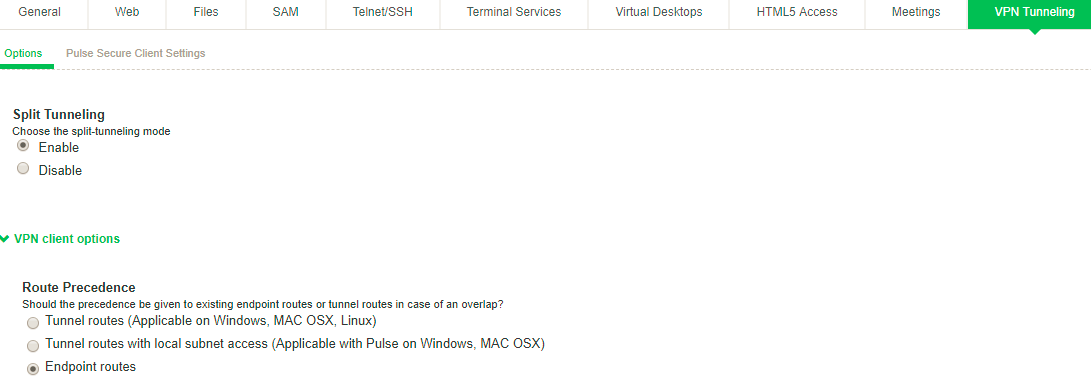
The network configuration in figure shows that the local network and the protected network at the other end of the VPN tunnel both have a subnet with the same private IP address, 10.10.0.0/24. In this case, the endpoint needs more information to determine where to send traffic addressed to that IP address range. You use the route precedence setting in the split tunneling settings to define which routing table takes precedence, either the tunnel routes (the routing table associated with the VPN tunnel) or the endpoint route (the routing table associated with the physical interface). If you select tunnel routes for route precedence, traffic addressed to network 10.10.0.0/24 in figure goes through the VPN tunnel and the 10.10.0.0/24 network available on the local indirect network is not reachable. If you select endpoint routes for route precedence, traffic addressed to network 10.10.0.0/24 goes through the physical adapter and the 10.10.0.0/24 network available through the VPN tunnel is not reachable. Ivanti Secure Access Client restores the original routes when the VPN tunnel is disconnected. However, no matter which way you define route precedence, the endpoint loses connectivity to one of the other of the networks if there are duplicate IP address networks.
Split Tunneling Disabled
When the endpoint has an active VPN tunnel connection, and split tunneling is disabled, the default route is modified to send all network traffic from the endpoint through the VPN tunnel where it is bound by the VPN access control and resource polices. If you set route precedence to endpoint routes, all network traffic goes through the VPN tunnel except traffic that is destined for directly-connected (local) subnets and indirectly connected (routed) subnets. Ivanti Secure Access Clients for Windows and OS X also support the following option to permit limited access to the local network:
•If the Ivanti Secure Access Client connection set is configured to allow the user to override the connection policy, the user can manually suspend the active Ivanti Secure Access Client connection to enable access to the local network. In the network in Figure the user could suspend the Ivanti Secure Access Client connection to access the local printer, which resides on the same subnet as the Ivanti Secure Access Client endpoint. Suspending the Ivanti Secure Access Client connection is a manual method. The user must suspend the connection to access to local subnet and then resume the connection to restore connectivity through the tunnel. While the connection is suspended, no traffic goes through the tunnel.
•You can configure the split tunneling properties to allow access to the local subnet. With split tunneling disabled and local subnet access allowed, network traffic goes through the tunnel except for addresses that are on the local subnet. In the network in figure the user could print to the local printer but other traffic would go through the default route to the tunnel. No traffic would go through the subnet router 192.168.0.2.
Split Tunneling Enabled
When the endpoint has an active VPN connection, and split tunneling is enabled for the role, Ivanti Connect Secure adds or modifies routes on the endpoint so that traffic meant for specific subnets uses the VPN tunnel, and all other traffic goes through the local physical adapter. You specify the subnets that are excluded from access or accessible through the VPN tunnel by defining split tunneling resource policies. In a case where you have identically numbered subnets on both the local network and the tunnel network, (that is, the specified split-tunnel subnet conflicts with an existing endpoint route), the route precedence setting determines the traffic path. The route monitoring option, when enabled, enhances network security by terminating the VPN tunnel if another process on the endpoint makes a change to the routing table.
Ivanti Secure Access Client Split Tunneling Summary
The following scenarios summarize the traffic flows that are possible with each split tunnel configuration. Split tunneling options enable you to control the network traffic on the endpoint so that you can allow the needed connectivity to users while maintaining network security.
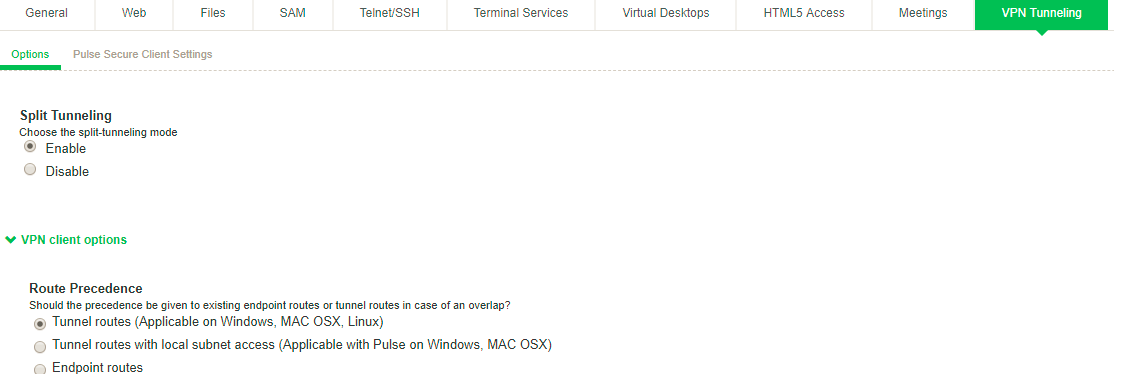
All network traffic from the endpoint goes through the VPN tunnel. Local networks are not available. Ivanti Secure Access Client users may choose to suspend the Ivanti Secure Access Client connection to allow local access if the Ivanti Secure Access Client connection set has the property Allow users to override connection policy enabled. VPN tunneling access control resource policies in effect for the user’s role determine which IP resources the user can access. Split tunneling resource policies are not in effect with split tunneling disabled.
This configuration provides the best security. However, the user has no access to local network resources.
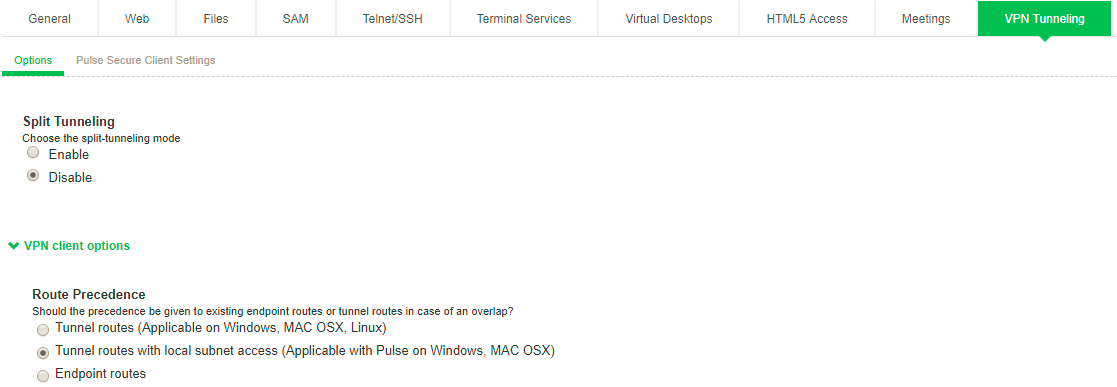
All network traffic goes through the VPN tunnel except traffic that is destined for directly-connected (local) subnets. VPN tunneling access control resource policies in effect for the user’s role determine which IP resources the user can access. Split tunneling resource policies are not in effect with split tunneling disabled.
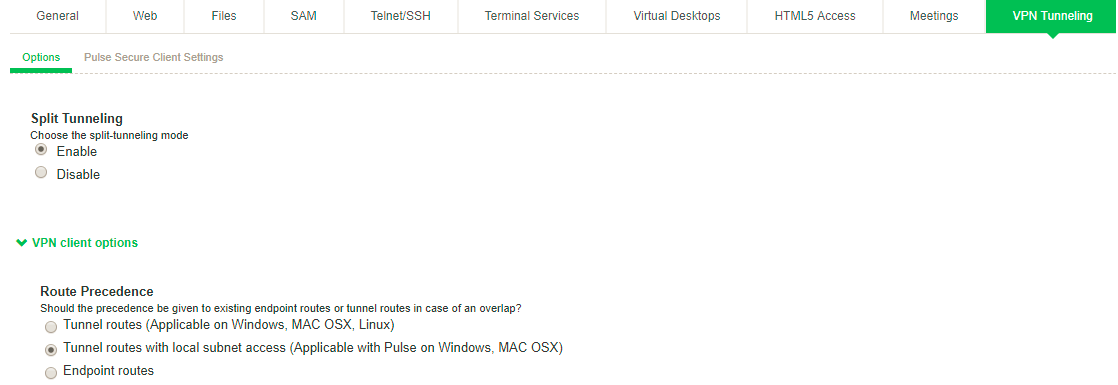
Network traffic addressed to the networks defined in the split tunnel resource policies goes through the VPN tunnel.
Network traffic that is addressed to the directly-connected (local) subnet goes to the local subnet. The default route is set to the local subnet so all other network traffic is subject to the original endpoint routing table.
Network traffic addressed to the networks defined in the split tunnel resource polices goes through the VPN tunnel.
The default route is set to the local subnet so all other network traffic is subject to the original endpoint routing table.
This configuration provides the greatest flexibility for the user.
IPv6/IPv4 Split Tunneling
Ivanti Secure Access Client now allows accessing both IPv4, IPv6 corporate resources from IPv4 and IPv6 endpoints and FQDN resources. It enables client to access both corporate network and local network at the same time. The network traffic designated are directed to tunnel interface for corporate network by configuring route policies, whereas other traffics are sent to direct interface.
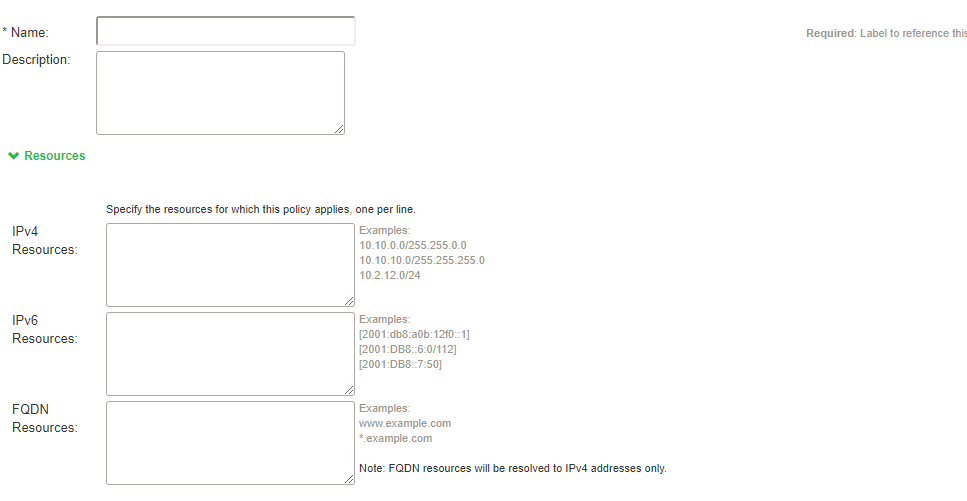
All configurations to IPv6 are similar to IPv4.
|
Split Tunnel |
IPv4 Tunnel Address |
IPv6 Tunnel Address |
IPv4 Include Policy |
IPv4 Exclude Policy |
IPv6 Include Policy |
IPv6 Exclude Policy |
Expected Client Behavior |
|
Disabled |
Yes |
No |
NA |
NA |
NA |
NA |
All IPv4 traffic should go through tunnel. |
|
Disabled |
Yes |
Yes |
NA |
NA |
NA |
NA |
Both IPv4 and IPv6 traffics should go through tunnel. |
|
Enabled |
Yes |
No |
IPv4 include subnet Eg: 10.0.2.0/24 |
IPv4 exclude subnet if any otherwise Empty. |
Empty |
Empty |
All IPv4 include traffic should go through tunnel. All IPv4 exclude traffic should go directly through physical interface. |
|
Enabled |
Yes |
Yes |
IPv4 include subnet Eg: 10.0.2.0/24 |
IPv4 exclude subnet if any otherwise Empty. |
Empty |
Empty |
All IPv4 include traffic should go through tunnel. All IPv4 exclude traffic should go directly through physical interface. All IPv6 traffic should go through the tunnel. |
|
Enabled |
Yes |
Yes |
Empty |
Empty |
IPv6 include subnet Eg: [fc00:0:0:2::/64] |
IPv6 exclude subnet if any otherwise Empty |
All IPv4 traffic should go through the tunnel. All IPv6 traffic included traffic should go through tunnel. All IPv6 exclude traffic should directly go through physical interface. |
|
Enabled |
Yes |
Yes |
IPv4 include subnet Eg: 10.0.2.0/24 |
IPv4 exclude subnet if any otherwise empty |
IPv6 include subnet [fc00:0:0:2::/64] |
IPv6 exclude subnet if any otherwise Empty |
All IPv4 include traffic should go through tunnel. All IPV4 exclude traffic should go directly through physical interface. All IPv6 include traffic should go through tunnel. All IPv6 exclude traffic should go directly through physical interface. |
|
Enabled |
Yes |
Yes |
1st policy: 10.0.2.0/24 2nd policy: empty |
Empty
Empty |
1st policy: Empty 2nd policy: [fc00:0:0:2::/64] |
Empty
Empty |
All IPv4 traffic to 10.0.2.0/24 should go through tunnel. Other IPv4 traffic should directly go through physical adapter. All IPv6 traffic to [fc00:0:0:2::/64] should go through tunnel. Other IPv6 traffic should go to physical adapter. |
For FQDN deployment scenarios, refer to FQDN based Split Tunneling Deployment Guide.
FQDN is not supported on IPv6.
FQDN resource has given higher preference than IPv4 resource in case of conflict.
Split Tunneling Notes
•Ivanti Connect Secure tries to resolve all DNS requests through the endpoint’s physical adapter first, and then routes those that fail to the VPN tunneling adapter.
Split Tunneling considerations on Mobile
While accessing Split tunnel IPV4 ( 10.10.10.1) resources using FQDN name on mobiles, ensure you configure the following pre-requisites to access the resource through the tunnel.
1.Configure DNS domain with domain suffix in Network Overview page.
2. If Manual DNS settings are configured in Tunnel connection profile, then configure DNS domain with domain suffix of the Resoruce.
For example, x.y.z is the hostname of 10.10.10.1 in domain y.z then specify y.z as the domain specific.
Split DNS
Split DNS for FQDN split tunneling looks up for FQDN through ICS DNS server or physical adapter DNS based on the Split Tunnel policy.
Split DNS allows to resolve DNS requests for specific domains that are explicitly resolved using virtual adapters while others DNS requests can continue resolve using Physical Adapter DNS Servers.
By default all the ICS DNS Domain(s) queries are resolved through ICS DNS servers. For example, if Ivanti Connect Secure is configured with DNS Domain(s) suffix list: company.com, company.net:
•company.com and company.net DNS queries are resolved through Ivanti Connect Secure DNS servers
•*.company.com and *.company.net DNS queries also are always resolved through Ivanti Connect Secure DNS servers
DNS feature has the following considerations:
- Supported on Windows 10 or later with FQDN split tunneling feature enabled
- Disabled by default
- Affects DNS search order
- Not supported on Windows ARM64
- Not supported on IPv6
- Not supported for co-existence of L3 and L4 connections
- Not supported on ZTA
To enable loading of split DNS, on the ICS UI navigate to System --> Configuration --> Advance Client Configuration. Under, Advanced Configuration for Ivanti Secure Access Client, set the <enable-SplitDNS-driver>true</enable-SplitDNS-driver>.