ISAC Application Deployment through Intune on Apple iOS
To deploy ISAC application using Intune, refer to Intune documentation for complete procedure.
- Create Users and Groups. For more information on User management, refer Create a user in Intune and Create a group to manage users.
- Enrol devices: Device enrollment guide for Microsoft Intune and https://www.youtube.com/watch?v=mJyv6YcHi7c.
- Add ISAC application to Intune: Add apps to Microsoft Intune.
- Setup the application assignment: Include and exclude app assignments in Microsoft Intune.
- Assign the application to specific user and endpoints: Assign apps to groups in Microsoft Intune.
Set Up Groups
Groups in Intune provide great flexibility for managing the mobile devices and users. You can set up specific mobile device groups based on your organizational requirements.
For more information device categorization, refer Categorize devices into groups in Intune.
For more information on User management, refer Create a user in Intune and Create a group to manage users.
When the policies are created, you can deploy them to one or more devices or user groups.
Compliance Policies
Create compliance policy for each platform, click Create Policy. Select Platform and the Profile Type. Refer to Device compliance policies in Microsoft Intune.
Configuration Profiles
Microsoft Intune policies provide settings that help you control the security settings on mobile devices. Using its capability of controlling access to company resources, you can deploy certificates, VPN profiles, and so on.
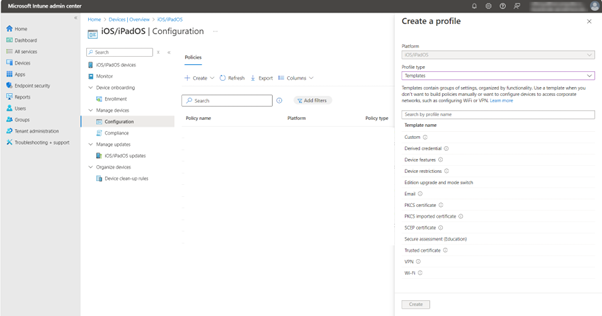
Creating Trusted Certificate Profile
Before proceeding, ensure you have exported the Trusted Root Certification Authorities (CA) certificate as a .cer file from the issuing CA.
To create trusted certificate profile in Intune:
- Navigate to Home > Devices > iOS/iPadOS > Configuration.
- In the Create a profile window, select Profile type as Templates, select Trusted Certificate and click Create.
- Enter a name and description for the policy. Under certificate settings, upload the root certificate file and the select the required destination store. Assign to the required groups and create the Policy.
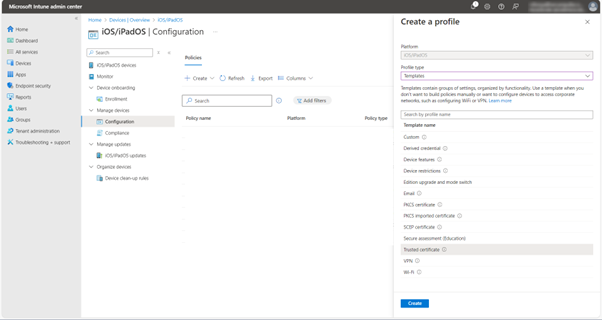
Creating Certificate Profile
Before proceeding with VPN profile creation, the certificate profile MUST be created in Intune. Configure the SCEP certificate profiles to use for VPN connections. For more information see, Use SCEP certificate profiles with Microsoft Intune.
Creating VPN Profile
Mobile devices use a VPN connection profile to initiate a connection with the VPN server. Use VPN profiles in Microsoft Intune to deploy VPN settings to mobile devices in your organization, so they can easily and securely connect to the network.
Before proceeding, make sure you have IP address or FQDN name of Ivanti Connect Secure (ICS) server that mobile devices will connect to.
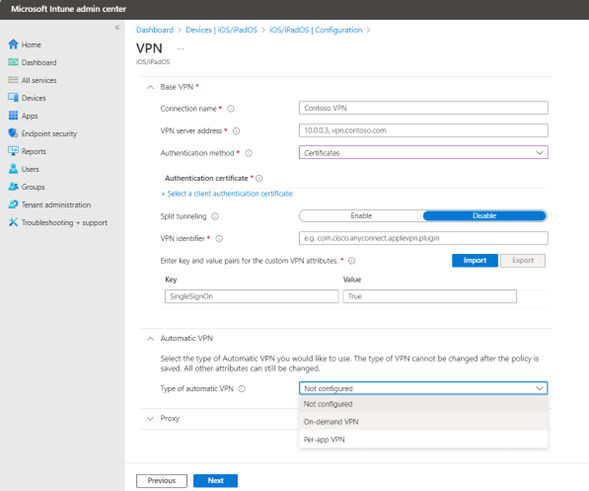
To create a VPN profile:
- In the Intune admin console, navigate to Home > Devices > iOS/iPadOS > Configuration.
- Under Policies, click Create and select New Policy.
- In the Create a profile window, select Profile Type as Templates and choose VPN as Profile Name.
- In the Basics details, enter a name and description for the policy.
- In the Configuration settings, from the Connection type drop-down list, select Custom VPN.
- Under Base VPN details, enter the ICS server name for Connection Name.
- For VPN IP address name, enter the ICS sign-in URL or the server IP address.
- From the Authentication method, drop down list. You can select to use credential based or certificate-based authentication.
- If you select Certificates, click Select and choose client certificate for authentication. Enter the SCEP Certificate profile name created before; for details, see Creating Certificate Profile
- Split Tunnelling is set to Disable by default. The split tunnelling is controlled from ICS.
-
Use Identifier “net.pulsesecure.pulsesecure” for Ivanti VPN. Set Key as follows:
VPN SubType: net.pulsesecure.pulsesecure
VPNType: VPN -
Continue to set the VPN profile type: Under Automatic VPN,
-
Select Not configured to proceed with default settings. This is default value. User needs to manually connect to VPN.
-
Select Per-App VPN and create rules as required.
-
Provider Type: Use App-proxy for L4 connections and Packet-tunnel for L3 connections.
-
Enter the Safari URL to connect to VPN for Safari domains.
Use Safari Domains or Application specific traffic to establish VPN. -
For On-demand VPN, click Add and enter the rule. This is applicable to L3 VPN on Demand (VOD). Refer, Configure VPN settings to iOS/iPadOS devices in Microsoft Intune.
ISAC is named as Pulse Secure VPN. You can use Pulse Secure as VPN. Ensure to re-push the profiles in case the profiles are not recognised by the VPN application.
For more information on VPN profile, refer Configure VPN settings to iOS/iPadOS devices in Microsoft Intune.
If required, Proxy can be configured for the VPN profile. Refer to VPN Settings - Proxy.
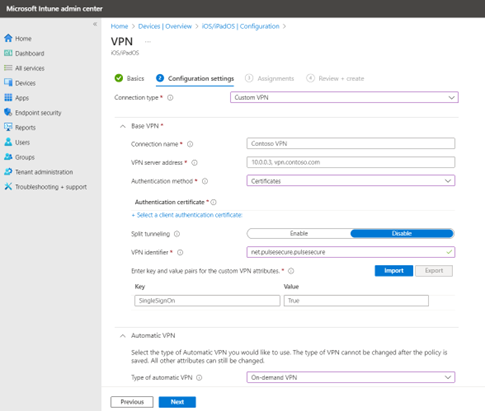
Configure Per-App VPN
To create per-app VPN
- On the Intune portal, create a VPN profile.
- Click Next and Configure Profile Name.
- Under Automatic VPN, select Per-App VPN, enter the Safari URL to connect to VPN, Associated Domains, and Excluded Domains as applicable.
- Navigate to Apps > App configuration policies, click Add and select Managed Devices. Add line of bussiness or app store.
- Two ways of per-app VPN config:
- Safari based: Add safari Domain URL.
- Application based: Link the VPN profile with application. Refer to Per-app VPN Settings
Configure On-Demand
Refer Automatic VPN settings -- On-Demand to create rules.
This is applicable to L3 VPN on Demand (VOD).
Configure Always-on VPN
To create Always-On VPN profile:
- On the Intune portal, create a VPN profile.
- Click Next and Configure Profile Name.
- Configure Custom VPN using Identifier “net.pulsesecure.pulsesecure” for Ivanti VPN.
- Configure Automatic VPN rules in the right below order and save the profile.
- Disconnect rule for Office SSID’s.
- Connect rules for All Domains
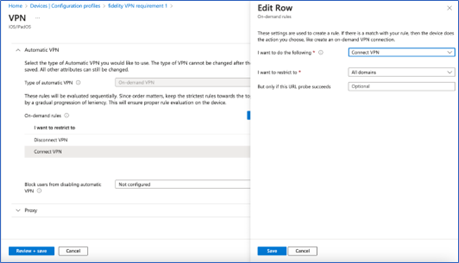
- Enrol the device to receive the Required profiles and ensure the VPN On Demand rules are configured / updated by MDM to the ISAC client in the specified order only.
- Connect to Office SSID’s specified in Disconnect rule and verify the VPN does not trigger.
- Now move to LTE or any other SSID except the Office SSID and see the VPN auto connects and allows the resource access as per the Split tunnelling policy configured in the ICS.
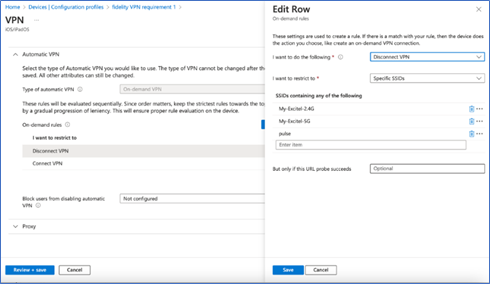
ICS Configuration to import CA certificate
To import a trusted client CA certificate:
- On ICS console, select System > Configuration > Certificates > Trusted Client CAs to display the configuration page.
- Click Import CA Certificate to display the configuration page.
- Browse to the VPN certificate file, select it, and click Import Certificate to complete the import.
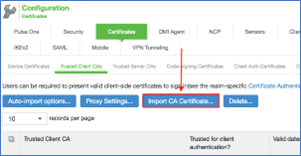
To configure authentication with the certificate server:
- On the ICS console, select Authentication > Auth. Servers.
- Select Certificate Server and click New Server to display the configuration page.
- Specify a name to identify the server within the system.
- Specify a username template. Specify how the system should construct a username. You may use any combination of certificate variables contained in angle brackets and plain text.
To implement certificate restrictions at the realm level:
- On ICS console, select Users > User Realms > <Select Realm>, select the corresponding User Realm used for L3 connections.
- Under Servers, select the certificate auth server from the authentication drop-down menu.
ICS Configuration for L3 VPN
For L3 VPN, in ICS server navigate to Users > User Roles > General. In the Access features section, enable VPN tunneling. For more details, refer to the section “Configuring General Role Options” in Ivanti Connect Secure Administration Guide.
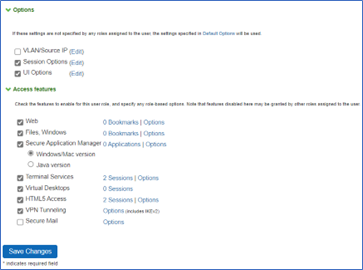
ICS Configuration for L4 VPN
For L4 Per App VPN proxy, in ICS server navigate to Users > User Roles > General. In the Access features section, enable Secure Application Manager (Windows version). For more details, refer to the section “Configuring General Role Options” in Ivanti Connect Secure Administration Guide.
In ICS server, configure access control policies (ACLs) by navigating to Users > Resource Policies > SAM > Access Control. For more details, refer to the section “Specifying Application Servers that Users Can Access” in Ivanti Connect Secure Administration Guide.
Limitations
•No Support for FQDN based Split Tunnelling.
Conditional Access on iOS ISAC client
Conditional access feature allows to use identity-driven signals as part of the access control decisions. Conditional Access brings signals together, to make decisions, and enforce organizational policies. This feature allows administrators to restrict access to approved client apps using Intune app protection policies.
For detailed information, refer What is Conditional Access in Microsoft Entra ID?
Ensure you follow the steps to enable Conditional Access feature.
- Configure a SAML cloud app on Azure IdP and Ivanti Connect Secure. See, Deploying a BYOD Policy for Microsoft Intune Managed Devices and Client application configuration.
- Create Device Feature policy configuration in Intune MDM under Devices > Manage devices > Configuration > Create > New policy.
-
3. Under Device feature configuration edit “Single sign-on app extension configuration and add below three key value pairs.
Field
Value
Value Type
browser_sso_interaction_enabled
1
Integer
AppAllowList
net.pulsesecure.pulsesecure
String
disable_explicit_app_prompt
1
Integer
-
Configure conditional access policy, See Plan a Microsoft Entra Conditional Access deployment.
- Create Conditional access policy on Azure IdP.
- Select the user to apply the policy.
- Select the target resource as the ISAC client name.
- Choose conditions. Select Device platform as iOS for iOS devices,
- Select Client apps as Browser, mobile devices use browser for login.
- Block or grant access to the resources based on the above conditions and device compliance state. Ensure “Required Device to be marked as Compliant” is checked.
Identity based restriction is configured from MDM, Conditional access policy gets applied based on the compliance state fetched from Intune MDM.