Managing Server Certificate Authorities
ISAC Linux clients verifies server certificate with trusted Certificate Authorities (CA) store in the system. Follow the instructions to add issuing CA certificate to store.
CA certificates are stored in PEM format in trusted CA store. Following command is used to convert CA certificates to PEM format from DER format.
openssl x509 -in cert.crt -inform der -outform pem -out cert.pem
Linux (Ubuntu, Debian)
To Add CA certificate into system store:
-
Install the ca-certificate package
sudo apt-get install ca-certificates
-
Copy the CA certificate which has been used to sign the device certificate, to /usr/local/share/ca-certificates directory:
sudo cp device-ca.crt /usr/local/share/ca-certificates/device-ca.crt
-
Copy the CA certificate which has been used to sign the certificate of Identity Provider (IdP) (in case of SAML authentication), to /usr/local/share/ca-certificates directory:
sudo cp idp-ca.crt /usr/local/share/ca-certificates/idp-ca.crt
-
Update the CA store:
sudo update-ca-certificates
Linux (Fedora)
To add CA certificate into system store:
-
Become Super User of the machine using the following command:
su-
-
Install the ca-certificates package:
yum install ca-certificates
-
Copy the CA certificate which has been used to sign the device certificate, to /usr/local/share/ca-certificates directory:
sudo cp device-ca.crt /etc/pki/ca-trust/source/anchors/
-
Enable the dynamic CA configuration feature:
update-ca-trust force-enable
-
Copy the CA certificate which has been used to sign the certificate of Identity Provider (IdP) (in case of SAML authentication), to /usr/local/share/ca-certificates directory:
sudo cp idp-ca.crt /usr/local/share/ca-certificates/idp-ca.crt
-
Use command:
update-ca-trust extract
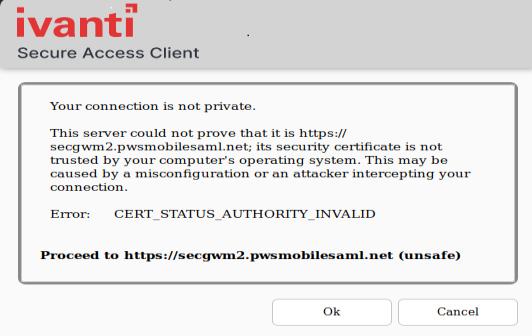
If the user connects to servers which have certificates not trusted by the machine the following error message displays:
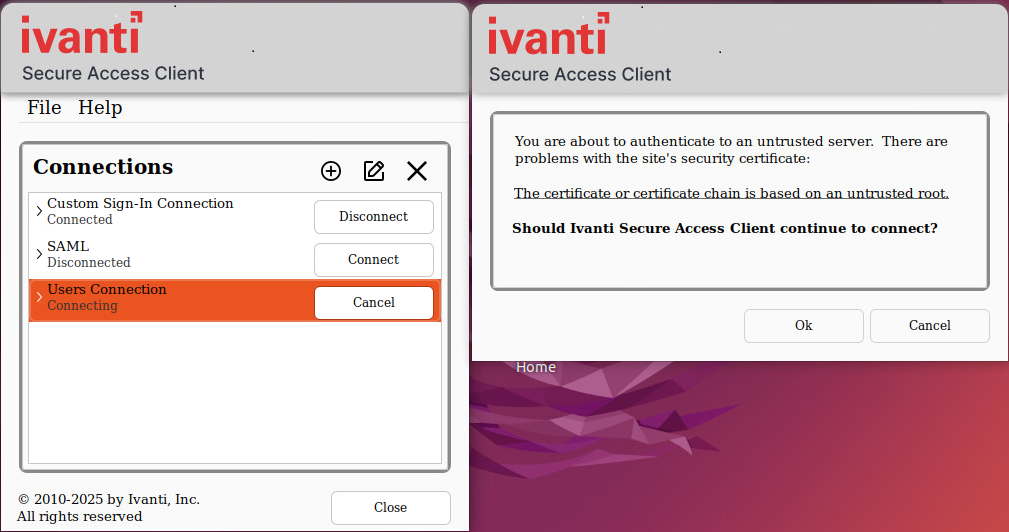
If connecting to untrusted sites through Embedded browser, the following error displays: