Using Enterprise Integration to Export Your Logs for External Analysis
•Introduction and Prerequisites
•Importing a Trusted Server CA Certificate
•Adding a Client Certificate to the NSA
•Adding a Public Syslog Server to the NSA
•White-listing Required IP Addresses for your Services
Introduction and Prerequisites
Ivanti Neurons for Secure Access (NSA) gathers data for events that occur on your ICS Gateways and from the NSA's Authentication, Authorization and Accounting (AAA) service. These events are categorized and stored in the following log files:
- Access Logs
- Admin Logs
- Event Logs
- Tenant Admin Audit Logs
NSA enables you to configure external syslog server to forward ICS Gateway logs and NSA Tenant Admin logs. You can view and obtain these logs at any time through the NSA Tenant Admin Portal (for details, see Checking the Logs ).
NSA enables you to automatically export log data for analysis in an external third-party enterprise analytics or visualizer tool through Enterprise Integration. This enables enhanced visibility into the health and efficiency of the services running in your ICS Gateways, or to facilitate debugging in the event of unexpected service behavior.
To receive the log data exported from ICS Gateway, your analytics endpoint should employ a syslog service that supports ingestion of data in JSON or WELF format. Syslog is a protocol defined through RFC 5424, and NSA supports exporting log data to any Security Information and Event Management (SIEM) system that can accept and parse syslog messages. Supported configurations are:
- A publicly-reachable syslog server for your NSA.
This requires you to configure NSA with the hostname or IP
address and port on which the analytics service is listening, and with
the client certificate to use to authenticate NSA to the syslog service.
NSA exports log data at 30 minutes intervals. Syslog forwarding is not real-time.
- An on-prem syslog server for your ICS Gateway(s). This requires you to configure ICS Gateway with the hostname or IP address and port on which the analytics service is listening, and with the required protocol for the syslog service. In this case, syslog forwarding is real-time.
To use this facility, you must:
- Obtain and import a trusted Server Certificate Authority (CA) certificate suitable for the analytics service, see Importing a Trusted Server CA Certificate.
- Obtain and import a client authentication certificate for NSA, see Adding a Client Certificate to the Controller.
A client certificate is not required for an on-prem syslog server.
•Configure NSA with the details of your publicly-reachable syslog server, see Adding a Public Syslog Server to NSA.
Importing a Trusted Server CA Certificate
To export your logs to an analytics service, you first need to add a certificate for a Trusted Server Certificate Authority (Server CA).
Make sure you have a suitable certificate file, in PEM (Base64 ASCII encoded) format, stored on your local workstation before starting this procedure.
NSA supports certificate files in PEM format only. Other formats, such as PFX, are not currently supported.
To import a certificate for a trusted server CA:
-
Log into the NSA as a Tenant Admin, see Logging in to Ivanti Neurons for Secure Access.
-
From the Ivanti Connect Secure menu, select Integrations, then select Enterprise Integrations > Trusted Server CA.
The Server CAs page appears.
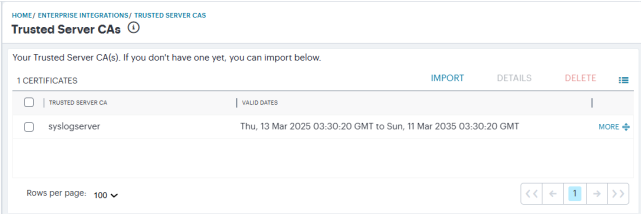
-
To import a Server CA certificate, click Import.
The Import Server CA page appears.
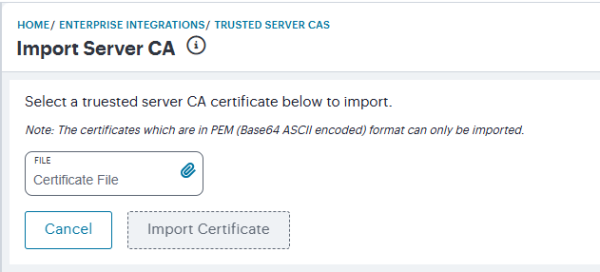
-
Click Certificate File and use the subsequent dialog to locate the certificate file from your local workstation file system.
-
To import the selected certificate, click Import Certificate.
The Trusted Server CAs page appears showing the successfully imported certificate.
-
(Optional) To view the details stored in a certificate, select the certificate check box and click Details.
-
(Optional) To delete a certificate, select the certificate check box and click Delete.
You can import more than one trusted server CA certificate.
After you have imported your trusted server CA certificate to the Controller, proceed to add your client certificate (see Adding a Client Certificate to NSA).
Adding a Client Certificate to NSA
Before you can export your logs to an analytics service, you must add a client certificate to verify the identity of NSA to the external service.
A client certificate is not required for an on-prem syslog server.
Make sure you have a suitable client certificate file, in PEM (Base64 ASCII encoded) format, stored on your local workstation before starting this procedure.
NSA supports certificate files in PEM format only. Other formats, such as PFX, are not currently supported.
To import a client certificate:
-
Log into NSA as a Tenant Admin, see Logging in to Ivanti Neurons for Secure Access.
-
From the Ivanti Connect Secure menu, select Integrations, then select Enterprise Integrations > Client Authentication.
The Client Authentication page appears.
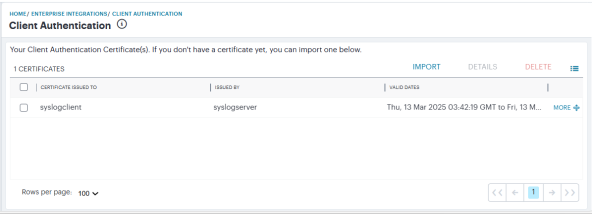
-
To import a client certificate, click Import.
The Import Certificate page appears.
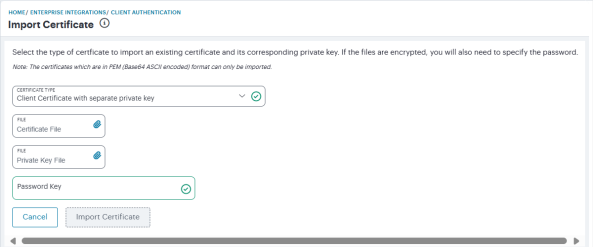
-
Click Certificate Type and select one of the following options:
- Client Certificate with embedded private key: Use this option if you are importing a certificate file with an embedded private key.
- Client Certificate with separate private key: Use this option if you are importing a certificate file with a separate private key file.
NSA updates the page to show the relevant import fields based on your selected option.
-
Click Certificate File and use the subsequent dialog to locate the certificate file from your local workstation file system.
-
(Optional) If you selected to use a separate private key, click Private Key File and use the subsequent dialog to locate the private key file from your local workstation file system.
-
(Optional) For Password Key, enter your private key passphrase.
-
To import the selected client certificate, click Import Certificate.
The Client Authentication page appears showing the successfully imported client certificate.
-
(Optional) To view the details stored in a certificate, select the certificate checkbox and click Details.
-
(Optional) To delete a certificate, select the certificate checkbox and click Delete.
You can import more than one client certificate.
After you have imported your Trusted Server CA certificate and Client certificate to NSA, proceed to add the details of your external analytics service (see Adding a Public Syslog Server to NSA).
Adding a Public Syslog Server to NSA
Before you configure a publicly-reachable Syslog server on NSA, ensure that:
- Your Syslog server is publicly-reachable, and that you know the hostname or IP address and port of the service.
- You have already added suitable Server CA and Client certificates.
Server CA Selection
To optimize Syslog server connectivity and performance, the Syslog Server configuration interface now includes a new drop-down enabling users to explicitly select the Server CA (Certificate Authority) when setting up secure connections. This enhancement complements the existing client certificate option and addresses latency issues during SSL handshakes.
Key Improvements
•Targeted Server CA Selection:
Administrators can now specify which Server CA to use when configuring Syslog servers. Previously, if no Server CA was selected, the system sequentially tested all Trusted CAs in the tenant during connection establishment, which increased connection times. This results in a better performance and a better user experience.
•Reduced Latency and Streamlined Handshakes:
Enhanced the syslog forwarding mechanism to enable real-time log delivery by directly consuming gateway log events.
•Improved Security and Accuracy:
By ensuring the correct Server CA is always used, this enhancement minimizes the risk of mismatched certificates and strengthens secure logging communications.
•Enhanced User Experience:
The refined UI makes Syslog server setup more intuitive and efficient, speeding up configuration and accelerating message delivery.
Administrators are encouraged to specify the relevant Server CA when adding or editing Syslog server configurations to gain the benefits of this enhancement.
To configure a Syslog server in NSA:
-
Log into NSA as a Tenant Admin, see Logging in to Ivanti Neurons for Secure Access.
-
From the Ivanti Connect Secure menu, select Integrations, then select Enterprise Integrations > Syslog Servers.
The Enterprise Integrations page appears.
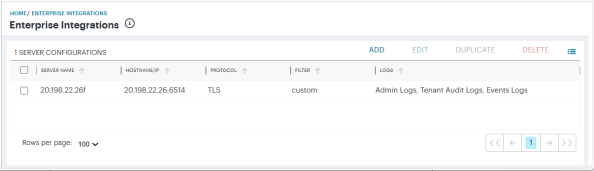
-
Click Add.
The Add New Configuration page appears, on the Configuration tab.
-
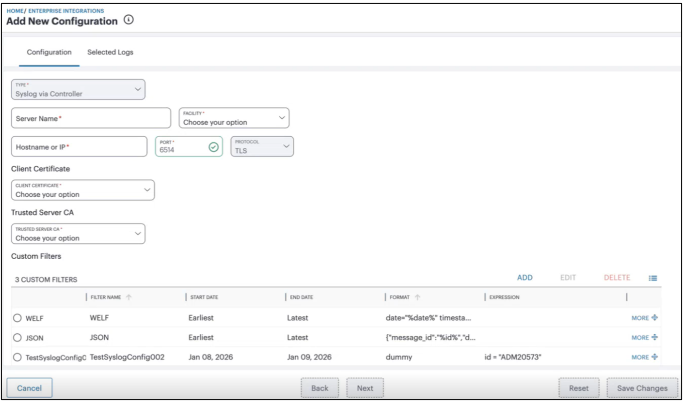
For Type, select Syslog via Controller.
-
Enter data for the following fields:
- Server Name: An identifying name for this Syslog server configuration. The server's name must match the CN in the subject DN in the certificate obtained from the server.
- Facility: The syslog facility level NSA should use while exporting log data. Facility level allows to logically separate syslog messages. Local0 to Local7 allow admin to define log categories specific to your business operations or applications.
- Hostname or IP: The hostname or IP address of the Syslog server. This must match the value contained in the Subject Alternative Name specified in the Server CA certificate applicable to this configuration.
- Port: The port on which the Syslog server is listening.
- Protocol: This field is read-only.NSA supports only the TLS protocol in this instance.
- Client Certificate: The client certificate you want to use with this Syslog server.
- Trusted Server CAs: Select Trusted Server CA to use from the drop-down list.
-
Specify or create a Custom Filter to select the log data sent to the Syslog server. Choose from:
- Use either of the predefined "JSON" or "WELF" filters. These do not place restrictions on the log data and forward all logs to the external Syslog server, using the respective data format.
- Create your own filter, based on log parameter rules you define yourself, see Setting a Custom Syslog Filter.
The predefined JSON and WELF filters are fixed and cannot be updated or deleted.
-
Click Next to select the required log files.
The Selected Logs tab appears.
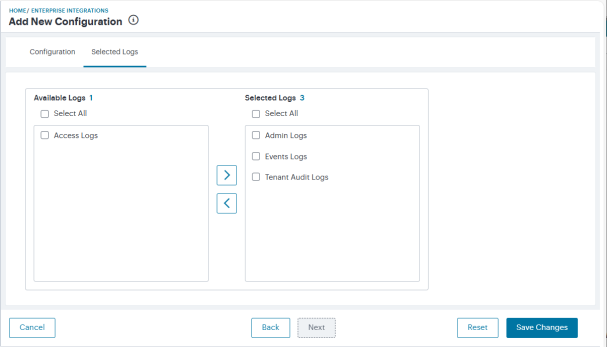
-
From the list of Available Logs, select the check box adjacent to the desired log and click the arrow to move it to the the Selected Logs list.
Repeat this step for each log you want to include. Use the reverse process to remove included logs.
-
To create a Syslog server configuration with the current settings, click Save Changes.
When a Syslog server is configured for the first time on a tenant, the system forwards logs from the past 15 minutes as part of the initial setup. Post that it follows 30-minute schedule.
Optionally:
- To edit an existing Syslog server configuration, select the check box adjacent to the configuration entry and click Edit.
- To duplicate an existing Syslog server configuration, select the check box adjacent to the configuration entry and click Duplicate. This creates a complete copy of the chosen configuration using the same server name appended with "-copy".
- To delete an existing Syslog server configuration, select the check box adjacent to the configuration entry and click Delete.
Setting a Custom Syslog Filter
NSA enables you to create a custom filter that builds a query to specify the data items exported to your Syslog server. You can specify criteria based on matching log data fields, date selection, and log output format.
This procedure assumes you are in the process of creating or editing a Syslog server configuration. To learn more, see Adding a Public Syslog Server to the Controller.
To add a custom syslog filter:
-
From the Add New Configuration page, locate the Custom Filters section and click Add.
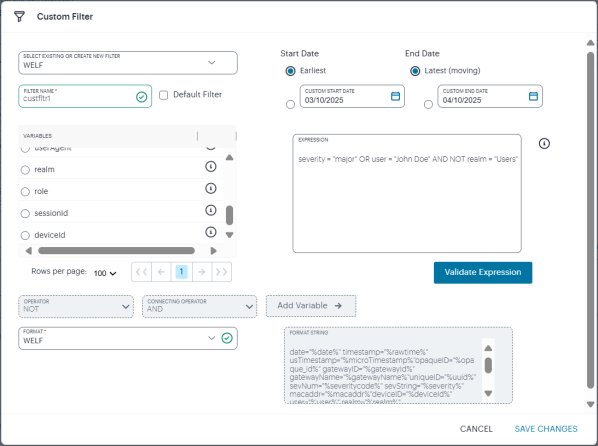
The Custom Filter dialog appears.
-
Use Select existing or create new filter to either:
- Create a new filter from scratch.
- Select an existing filter as a template. This option pre-populates the Expression and Format String fields with values used in the selected filter, which you can then use to create your new filter.
-
Enter a Filter Name.
-
Select a Start Date and End Date for the log data to be included. Use the default Earliest and Latest values to include all data, or select custom start and end dates, or a combination.
- NSA stores log data for the previous 30 days.
- Logs are forwarded in 30-minute intervals, with each job processing logs generated in the last 30 minutes.
- Syslog forwarding is not real-time. -
(Optional) To use this filter as the default for your Syslog Server configurations, select Default Filter.
-
(Optional) Select from the list of available log data Variables, select an Operator, and then click Add Variable to add a filter based on the chosen value.
NSA populates the Expression field with an expression matching your selection. An example value is added to the right of the operator, but this can be freely edited to your required value. Validate the expression by clicking Validate Expression.
Hover your pointer over the (i) icon to the right of each variable to view a tooltip showing example usage.
Examples of valid query expression:
- valid: user = "John Doe" AND realm = "Users"
invalid: user = "John" realm = "Users"
- valid: severity = "MAJOR" OR user = "John Doe" AND NOT realm = "Users"
invalid: severity = "MAJOR" OR invalid = 1
Valid expression: (sourceip = "1.1.1.1" AND id = "ADM32324" AND severitycode = 1 AND user = "user1") AND gatewayName = "fz55" -
(Optional) Repeat the previous step as required for each log data variable you want to include in the syslog filter.
-
Select an output Format for the log line. Choose from JSON or WELF. The resultant formatted string is shown in the box provided.
-
To save your filter settings, click Save Changes.
The Add New Configuration screen appears, showing your new filter as selected. Continue to create your syslog server configuration.
White-listing Required IP Addresses for your Services
The controller service uses a series of IP addresses and ports to facilitate access to the admin and user web consoles, for user enrollment, and for connections to a ICS Gateway. To ensure network access, make sure the following IP addresses and ports are white-listed (or added to the allowed list) in your network firewalls and routing infrastructure. Select the IP addresses and ports for your corresponding region only:
-
North America:
52.186.44.249 (port 443)
52.188.33.186 (port 443)
-
Europe:
51.138.111.17 (port 443)
20.50.150.82 (port 443)
-
APJ:
20.44.238.229 (port 443)
20.44.237.67 (port 443)
-
UAE
20.233.40.108 (port 443)
20.233.41.69 (port 443)
-
Canada:
20.220.157.85 (port 443)
20.220.157.158 (port 443)