Deploying a BYOD Policy for Microsoft Intune Managed Devices
This example shows how to use policies to enable security based on device identity, device posture, or user identity in a bring your own device (BYOD) environment for an enterprise that uses Microsoft Intune® for mobile device management (MDM).
Requirements
The following Component Version Information table lists version information for the solution components shown in this example.
|
Component |
Version |
|
Connect Secure |
Release 9.2r1 or later is required. |
|
Microsoft Intune MDM |
Release version 2002 is used in this example. Any version that supports the device ID and device attributes you plan to query is compatible. |
Supported Devices
•Google Android 5.0 and later
•iPhone iOS 8.0 and later
Configuring the Microsoft Intune MDM Service
When the user installs the MDM application on the device and completes enrollment, the MDM pushes the device certificate to the device. After enrollment, the MDM maintains a database record that includes information about the enrollee—attributes related to device identity, user identity, and posture assessment against MDM policies.
The following Microsoft Intune Device Attributes table describes these attributes. In this solution, these attributes are used in PCS role mapping that is the basis for network access and resource access policies. When you configure role-mapping rules, you specify the normalized attribute name.
From 9.1R12, Windows users can use the MAC address option under Device Identifier to register to Microsoft Intune.
|
Intune Attribute |
Normalized Name |
Description |
Data Type |
|
complianceState |
isCompliant |
True or false (string) based on whether device is compliant or non-compliant. |
Boolean |
|
isManaged |
isEnrolled |
True or false (indicating whether the client is managed by Intune or not). |
Boolean |
|
macAddress |
macAddress |
MAC address of the device. |
String |
|
serialNumber |
serialNumber |
Serial number of the device. Applies to iOS Devices only. |
String |
|
imei |
IMEI |
The device unique identifier. IMEI (15 decimal digits: 14 digits plus a check digit) or IMEISV (16 digits) includes information on the origin, model, and serial number of the device. |
String |
|
udid |
UDID |
The device unique identifier. Unique Device Identifier (UDID), which is a sequence of 40 letters and numbers that is specific to iOS devices. |
String |
|
meid |
MEID |
MEID is 56 bits long (14 hex digits). It consists of three fields, including an 8-bit regional code (RR), a 24-bit manufacturer code, and a 24-bit manufacturer-assigned serial number. |
String |
|
osVersion |
osVersion |
OS Version of the device. |
String |
|
model |
Model |
Model of the device. |
String |
|
manufacturer |
manufacturer |
Device Manufacturer. |
String |
|
azureDeviceId |
deviceId |
The device Id of the device after it has work place joined with Azure Active Directory. |
String |
|
lastContactTimeUtc |
lastSeen |
The date time when the device last checked in with the Intune management service endpoint. |
String The format is MM/DD/YYYY HH:MM:SS |
Refer to third-party documentation for complete information and configuration details.
To configure the MDM:
1.Enroll devices in the MDM using the methods supported by the MDM.
2.Create a profile. The profile determines many MDM management options. The following configurations are key to this solution:
•Create trusted certificate profiles in Intune. For detailed steps, refer to the procedure in the Microsoft Intune document.
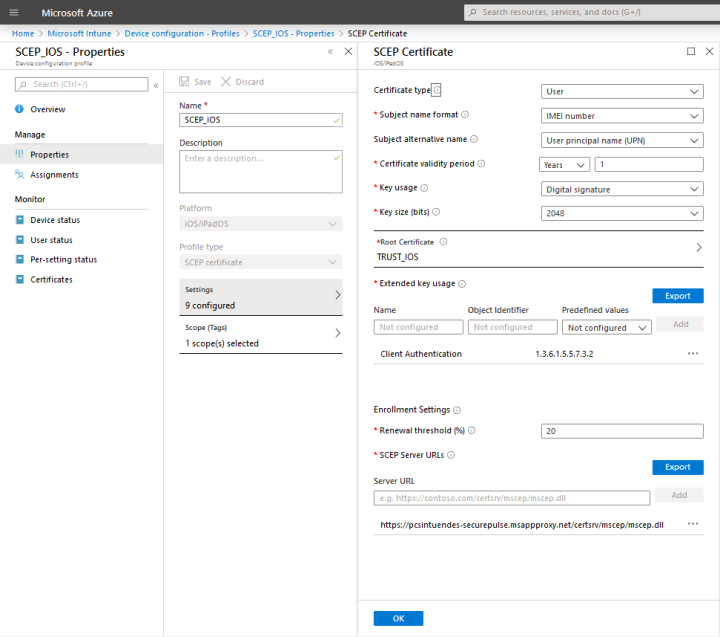
•Create and assign SCEP certificate profiles in Intune. For detailed steps, refer to the procedure in Microsoft Intune document.
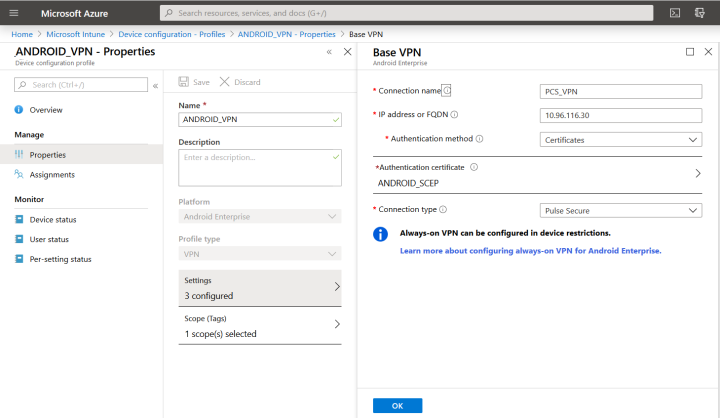
•Create VPN profile in Intune. For detailed steps, refer to the procedures in Microsoft Intune document.
Configuring PCS with Microsoft Intune
Microsoft Intune is an MDM server which provides the device compliance status for the mobile devices. PCS retrieves the device attributes from Microsoft Intune and uses it for compliance assessments and role assignment. This feature integrates Microsoft Intune and PCS for providing compliance check and onboarding of devices.
To configure Microsoft Intune MDM server:
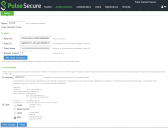
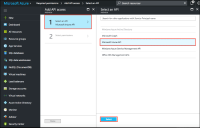
1.Select Authentication > Auth. Servers > New MDM Server.
2.Enter the server name, select Microsoft Intune as MDM.
•Enter the Azure AD Tenant ID.
•Enter the Web application ID or Client ID that is registered in Azure AD.
•Enter the Client Secret key registered in the Azure AD.
•Enter the Timeout duration in seconds. Default is 15 seconds.
To obtain Tenant ID, Client ID, Client Secret Key, see Viewing Client ID, Tenant ID, and Client Secret.
3.Click Save changes.
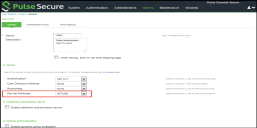
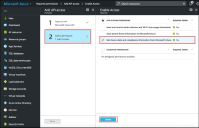
4.Select Users > User Realms and select the Device Attribute server for Microsoft Intune.
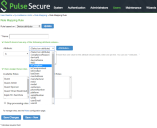
5.Select Role Mapping tab of the user realm to create role mapping rules. Configure the role mapping rules based on the Microsoft Intune supported device attributes.
The following table demonstrates Microsoft Intune Role Mapping Attributes.
|
Role Mapping Attribute Name |
Microsoft Intune Attribute Name |
Description |
Data Type |
|
deviceid |
azureDeviceId |
The device Id of the device after it has work place joined with Azure Active Directory. |
String |
|
IMEI |
imei |
The device unique identifier. IMEI (15 decimal digits: 14 digits plus a check digit) or IMEISV (16 digits) includes information on the origin, model, and serial number of the device. |
String |
|
isCompliant |
complianceState |
True or false (string) based on whether device is compliant or non-compliant. |
Boolean |
|
isEnrolled |
isManaged |
True or false (indicating whether the client is managed by Intune or not). |
Boolean |
|
lastSeen |
lastContactTimeutc |
The date time when the device last checked in with the Intune management service endpoint. |
String The format is MM/DD/YYYY HH:MM:SS |
|
macAddress |
macAddress |
MAC address of the device. |
String |
|
manufacturer |
manufacturer |
Device Manufacturer. |
String |
|
meid |
meid |
MEID is 56 bits long (14 hex digits). It consists of three fields, including an 8-bit regional code (RR), a 24-bit manufacturer code, and a 24-bit manufacturer-assigned serial number. |
String |
|
model |
model |
Model of the device. |
String |
|
osVersion |
osVersion |
OS Version of the device. |
String |
|
serialNumber |
serialNumber |
Serial number of the device. Applies to iOS Devices only. |
String |
|
UDID |
udid |
The device unique identifier. Unique Device Identifier (UDID), which is a sequence of 40 letters and numbers that is specific to iOS devices. |
String |
|
UUID |
uuid |
Universal unique device identifier. |
String |
Configuring the Microsoft Intune MDM Server
Microsoft Intune acts as the Mobile Device Management (MDM) Server for PCS solution. PCS users have to register their mobile devices with Microsoft Intune. As part of registration, the relevant Profiles get automatically provisioned to mobile device.
To configure the Microsoft Intune MDM:
1.Enroll the devices with the MDM server.
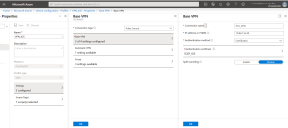
2.Create an enterprise WiFi profile.
•Configure PCS with a role and realm for the user. Microsoft Intune provides the user with a link to provision the created policy and then pushes the profile information. PCS does the role assignment and either allows or denies based on the device assessment.
3.Create Azure Active Directory (AAD) web application.
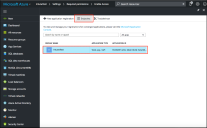
4.Go to portal.azure.com, click on the Azure Active Directory on the left of the screen, click on the App registrations and then click on New application registration.
5.Enter the application name, select Web app/API as application type, and enter the IP address/FQDN for sign-on-URL and click Create.
The Application Registration page appears if the registration is successful.
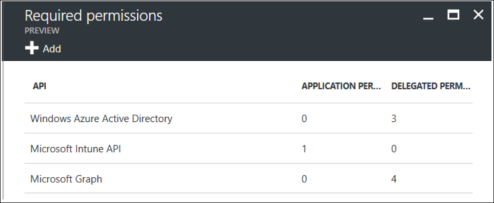
6.Click the application, then select the required permissions and click Add.
7.Click Grant Permission.
8.Select Microsoft Intune API.
9.Under Application Permissions, select Get device and compliance information from Microsoft Intune.
10.(Optional) You must add the following delegated permissions for Microsoft Graph API.
•Sign in and read user profile
•Sign Users in
•View users’ email address
•View users’ basic profile
11.(Optional) Add the following delegated permissions for Azure Active Directory.
•Sign in and read user profile
•Read all users' basic profiles
•Access the directory as the signed-in user.
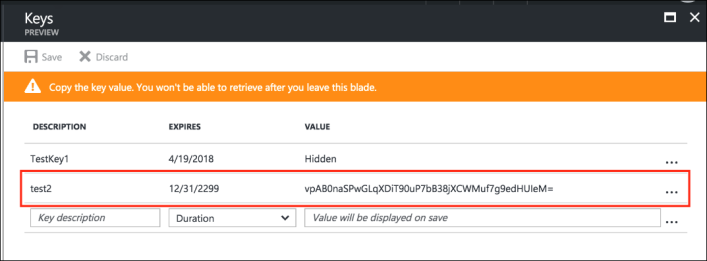
Viewing Client ID, Tenant ID, and Client Secret
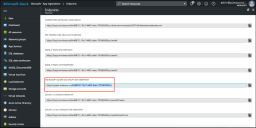
The Client ID/Application ID is created automatically once the AAD web application/API is created. You can view the client ID/application ID from the application properties page.
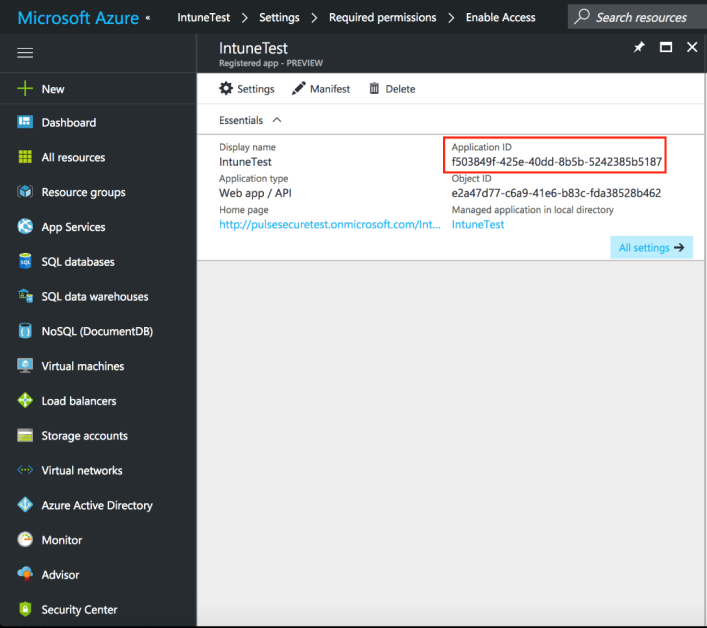
Every organization in Microsoft cloud is called tenant and it is organization specific. Each Tenant will be having a unique Tenant ID. Select the web application/API and click Endpoints tab and then you can copy the tenant ID.
To create the secret key, click the Web Application/API and then click Keys.