Using Logs to Verify Proper Configuration
|
Settings |
Guidelines |
|
Name |
Specify a name for the configuration. |
|
Description |
Describe the purpose of the configuration so that other administrators are aware of it. |
|
Resources |
|
|
Resources |
Specify the resources for which this policy applies, one per line. |
|
Roles |
|
|
Roles |
Select the roles to which the policy applies. In this example, Android is selected. |
|
Action |
|
|
Action |
Select one of the following actions: Allow Access Deny Access Use Detailed Rules In this example, we deny access from Android devices. |
Using Logs to Verify Proper Configuration
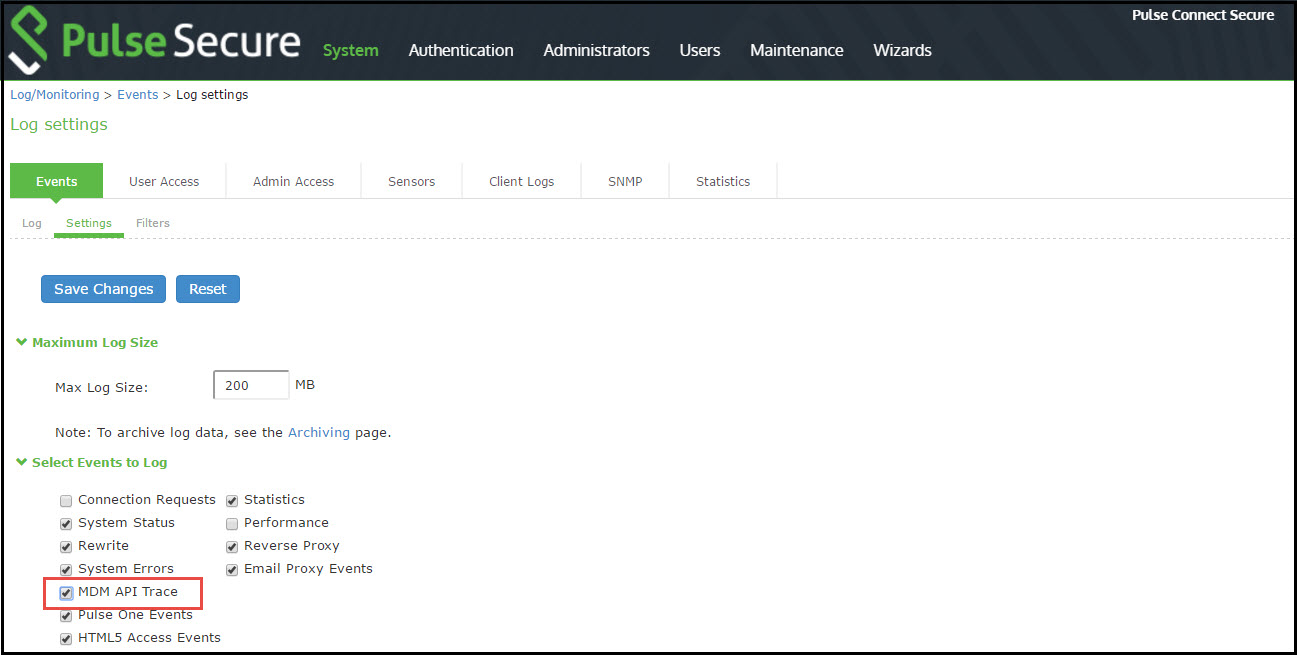
During initial configuration, enable event logs for MDM API calls. You can use these logs to verify proper configuration. After you have verified proper configuration, you can disable logging for these events. Then, enable only for troubleshooting.
To enable logging for MDM API calls:
1.Select System Log/Monitoring.
2.Click the Events tab.
3.Click the Settings tab to display the configuration page.
Figure shows the configuration page for Pulse Connect Secure.
4.Enable logging for MDM API events and save the configuration.
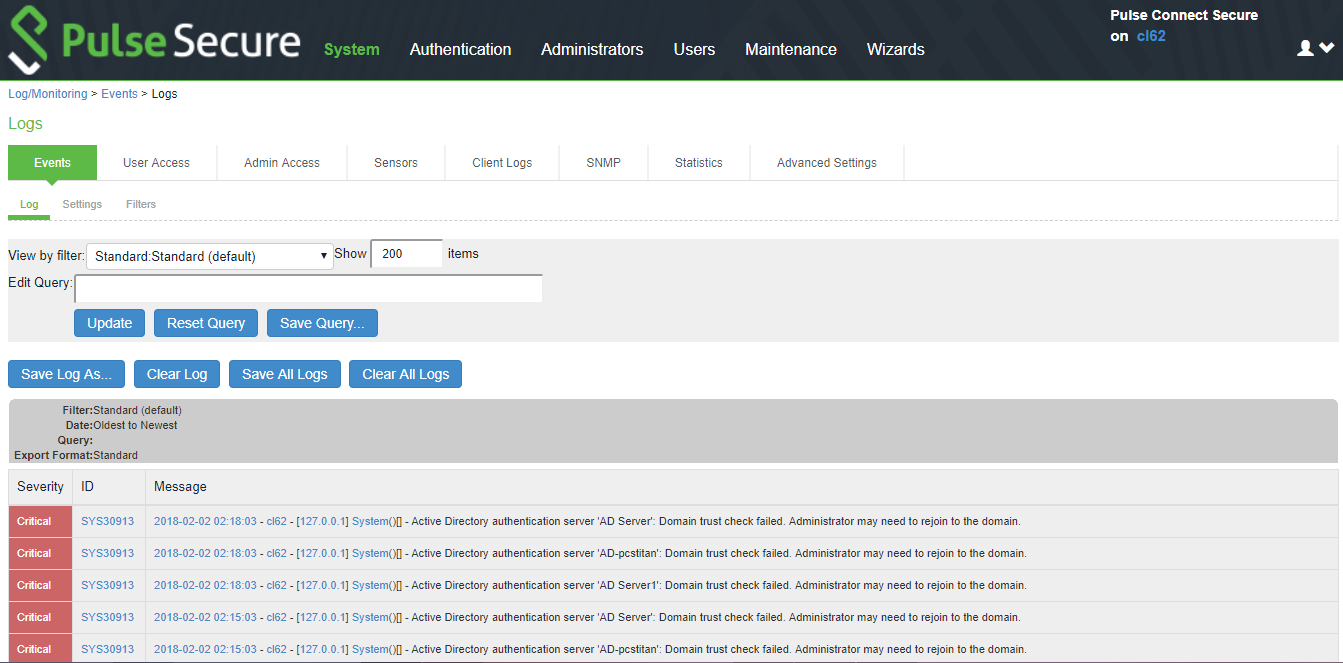
After you have completed the MDM server configuration, you can view system event logs to verify that the polling is occurring.
To display the Events log:
1.Select System Log/Monitoring.
2.Click the Events tab.
3.Click the Log tab.
The following figure shows the Events log for Pulse Connect Secure.
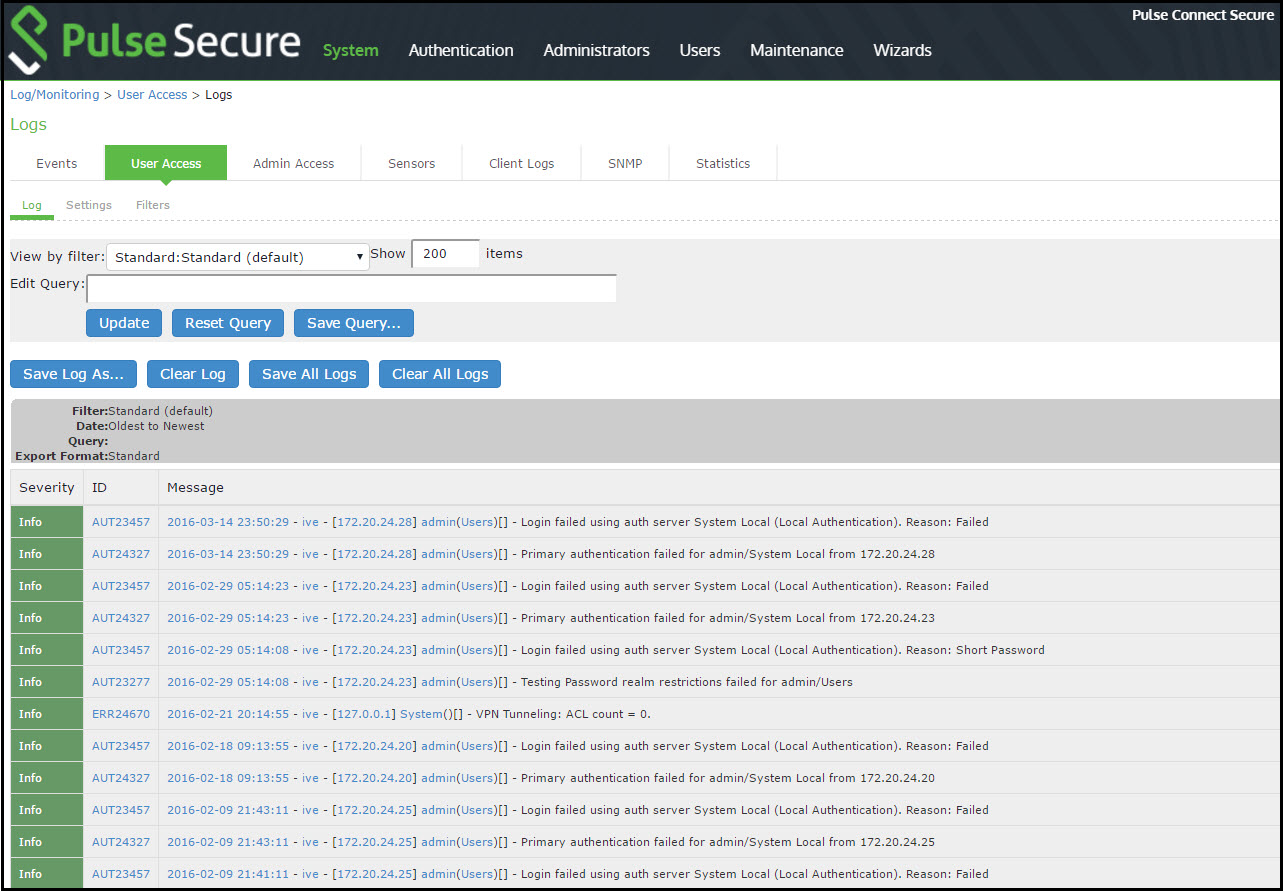
Next, to verify user access, you can attempt to connect to a wireless access point with your smart phone, and then view the user access logs.
To display the User Access log:
1.Select System Log/Monitoring.
2.Click the User Access tab.
3.Click the Log tab.
The following figure shows the User Access log for Pulse Connect Secure.