Cloud Secure ADFS Integration
Pulse Secure's Cloud Secure solution is capable of providing authentication as well as secure single sign-on to Office 365 services as a standalone Identity Provider. Most of the companies who are using Office 365 have also implemented Active Directory Federation Services (ADFS) for authentication.
In many cases, it would not be feasible for a company that has already deployed ADFS as their Identity Provider to change their Office 365 configuration.
The deployment discussed in the guide explores an alternative approach called IdP chaining, where Cloud Secure (PCS) acts as IdP for ADFS and handles all the authentication requests. This helps the customer to get the benefits of Cloud Secure such as compliance checks, secure single sign-on through VPN tunneling without making major changes to the existing setup. Pulse Connect Secure (PCS) is used as Identity Provider in Cloud Secure solution.
Deployment Scenarios
ADFS allows Pulse Connect Secure (PCS) to be configured as Third-Party Identity Provider and redirects all the SAML Authentication requests from Service Providers (SP) to PCS and vice-versa.
In this deployment scenario,
•ADFS is configured as Service Provider (SP) in PCS
•PCS is configured as claims provider in ADFS
•ADFS is configured as Identity Provider in SP
Cloud Secure integration with ADFS supports both SP initiated and IdP initiated SSO.
Office 365 access through applications (SP Initiated SSO)
When a user tries to access cloud service, the SAML enabled Service Provider generates SAML request and redirects it to ADFS. ADFS in turn redirects the incoming SAML authentication requests to PCS. PCS authenticates the user, and generates SAML AuthNResponse after compliance posture assessments. ADFS relays the response to Service provider thus providing access to the cloud resource
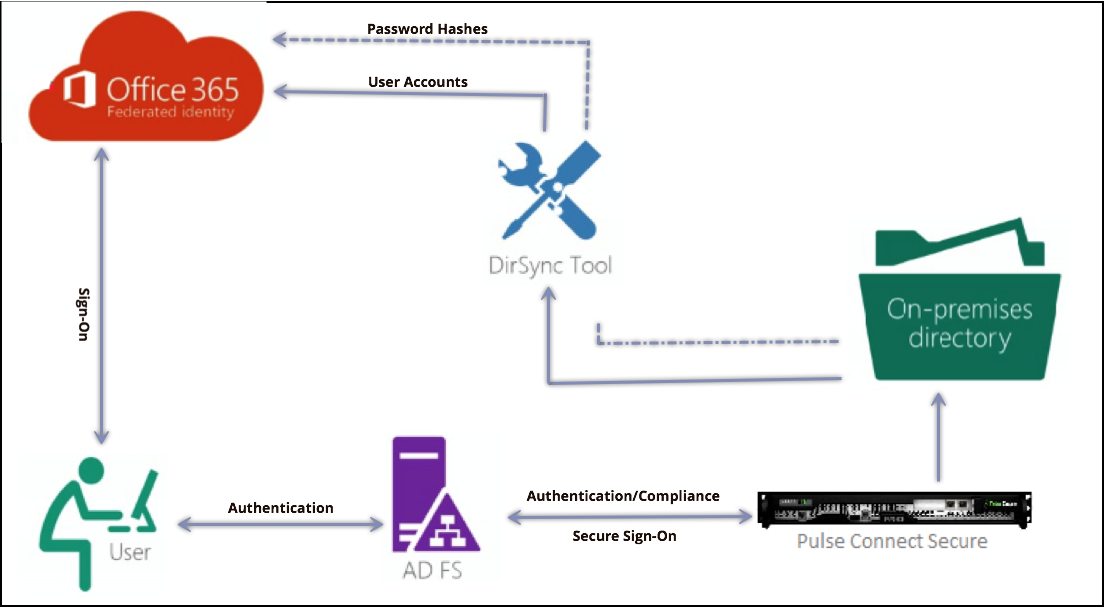
If the client has an existing VPN connection to PCS, then the same session will be reused and provides seamless SSO without asking for credentials
MobileIron and AirWatch Third-party MDM servers can also be used in this solution to manage devices and to evaluate compliance posture of the mobile devices
Office 365 access through bookmark (IdP Initiated SSO)
In IdP Initiated Single Sign-on, user first logs into PCS through browser. After authentication and compliance posture assessments, PCS shows up the browser page with all the configured bookmarks. When the user access the Office 365 bookmark, PCS generates the SAML assertion and relays it to ADFS. ADFS again relays the Assertion to Office 365 and provides seamless access to cloud resource
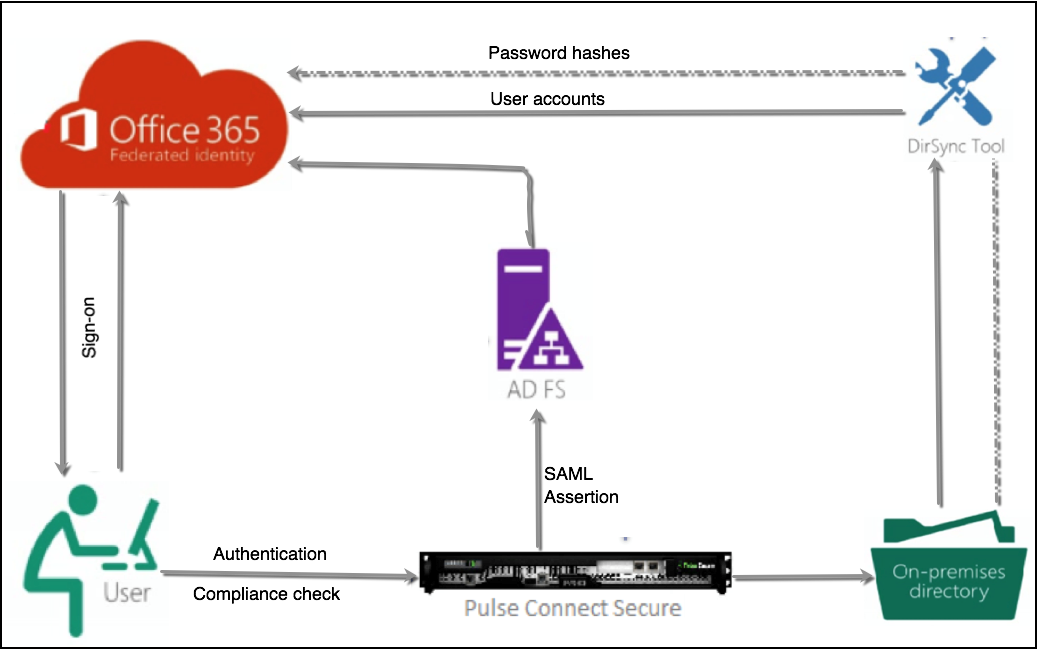
Cloud Secure ADFS integration solution works well with all Service Providers (like Salesforce, Zendesk etc.,), provided the SPs should be configured as Relying Party Trusts in ADFS
Pre-requisites
Prerequisites for this solution include:
•Identity Management Provider: Active Directory Federation Services (ADFS)
•Service Provider (Office 365): Office 365 Subscription. Office 365 Service Provider should be configured as Relying Party Trust in ADFS and ADFS is configured as Identity Provider in Office365 SP
•Wildcard or SAN Certificates: Wildcard or Subject Alternative Name (SAN) Certificates are required. SAN certificate should include the fqdn of PCS as well as ADFS.
•AD/LDAP Server: AD/LDAP with directory synchronization enabled
•Clients: iOS Device/ Android Device/ Windows/ MAC OS X Desktops
•(Optional) MDM Servers: Pulse Workspace Server/ MobileIron/ AirWatch servers are used for Mobile Device Management and Mobile Compliance posture assessments
Limitations
•Email Access through Native Email Client in iOS and GMAIL in Android are yet to be validated
Supported Platforms
•Browsers (Chrome, Safari, Firefox, Internet Explorer)
•Microsoft Outlook 2016 on desktops and mobiles
•Microsoft Outlook 2013 with a registry update
•Microsoft applications (Word, PowerPoint, Excel) on desktops and mobiles ?