Adaptive Authentication
Overview
Enterprises deal with constant and ever-increasing magnitude of threat vectors, which includes Data Loss Prevention (DLP), Domain Generation Algorithms (DGA) attacks and so on. With changing business requirements and new types of threats, Administrators must understand how users and devices are accessing company's data and services to ensure that the access control policies are up to date. Even after successful authentication, the user's activity should be monitored fully to ensure device compliance.
Behavioral Analytics feature analyzes user's action along with other context data to derive conclusions about any anomalous activities. It provides information/visibility based on real time user or device context thus helping in advanced attack detection and helps in proactive policy-based enforcement.
The following figure depicts Behavioral Analytics:
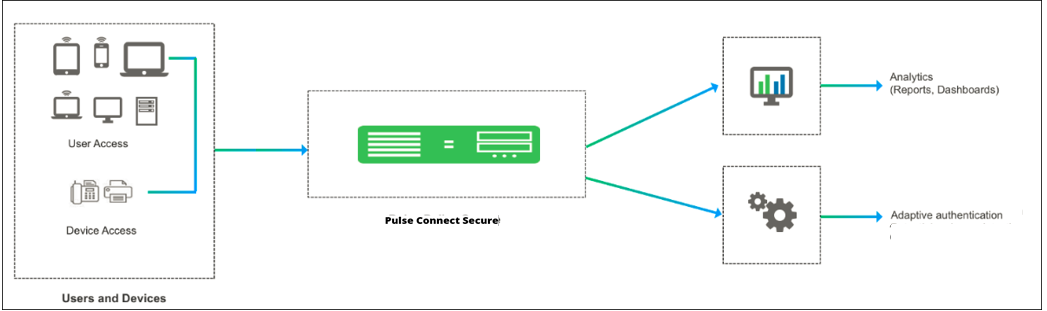
The Behavioral Analytics feature addresses the following types of anomaly detection:
•User/device is prompted for second level of authentication based on the threat profile determined for the corresponding user/device.
Below are some scenarios where second level of authentication is required:
•User authenticating from new device: This is detected by using the device MAC address.
•User authenticating from new location: Location details are obtained by using the location configurations.
Adaptive Authentication User Flow
1.Users connect to PCS.
2.PCS performs the primary authentication.
3.PCS checks for any anomalies using Behavioral Analytics.
4.PCS prompts for secondary authentication to connect to network to ensure only the valid users accesses the network.
5.User enters the credentials required for secondary authentication.
6.If a user is logging in for the first time or if the user location changes, then PCS performs the secondary authentication and allows/rejects access to the user/device.
Benefits
•PCS monitors the traffic from users and helps in determining the possible anomalous activities such as:
•If the user is authenticating from a new device / new location.
•If the device traffic is different from previous instances.
•Data collected as part of Behavior Analytics is stored so that it can be used later for determining the anomalies.
Configurations
•Configuring PCS for Enabling Behavioral Analytics
Summary of Configuration
1.Administrator enables the behavior analytics and configures PCS for Adaptive Authentication
2.Once the anomalies are detected, PCS tags the corresponding user profiles in the data.
3.Administrator configures the role mapping rules to consume these flags and control the access to the corresponding users.
4.Administrator enables the secondary authentication for the users in case they are tagged with anomalies activities to ensure additional level of authentication for security purpose.
5.View the Dashboard and Reports for any detected anomalies.
6.Administrator can also choose to clear the detected anomalies from the Reports page.
Behavior Analytics configuration is synched across the nodes in the cluster (including config-only clusters). However, data collected and analyzed is synched across the nodes but not in case of config-only clusters.
Configuring PCS for Enabling Behavioral Analytics
The Behavioral Analytics package is available by default for detecting the anomalies. If you plan to upgrade to the latest package, it can be downloaded from the Pulse Secure support portal.
Configuring PCS for Adaptive Authentication
To enable behavioral analytics:
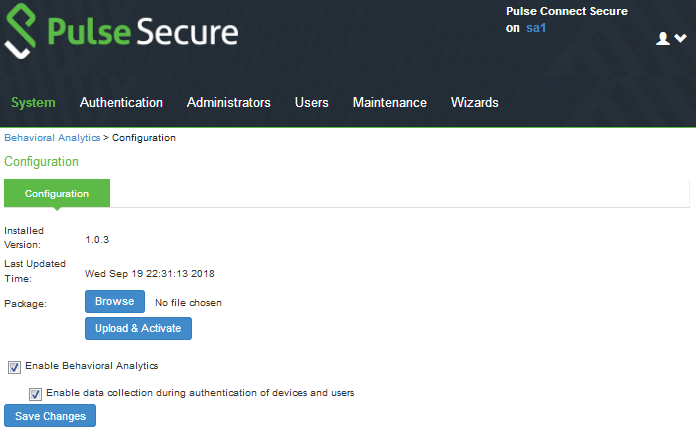
1.Select System > Behavioral Analytics > Configuration.
2.Under Configurations, select Enable Behavioral Analytics.
3.For enabling Adaptive Authentication, select Enable data collection during authentication of devices and users.
In case you have a Fresh Installation of PCS/PPS, then it will NOT have UEBA package by default with it. Please add the UEBA package before using Adaptive Authentication. In case of Upgrade of PCS/PPS from R7 or earlier to R8 or later, then UEBA package is carried forwarded as is and you can still update it to latest version by uploading new package. You may download latest UEBA package from Pulse Secure Support Site (my.pulsesecure.net)
The following figure depicts the Behavioral Analytics Configuration:
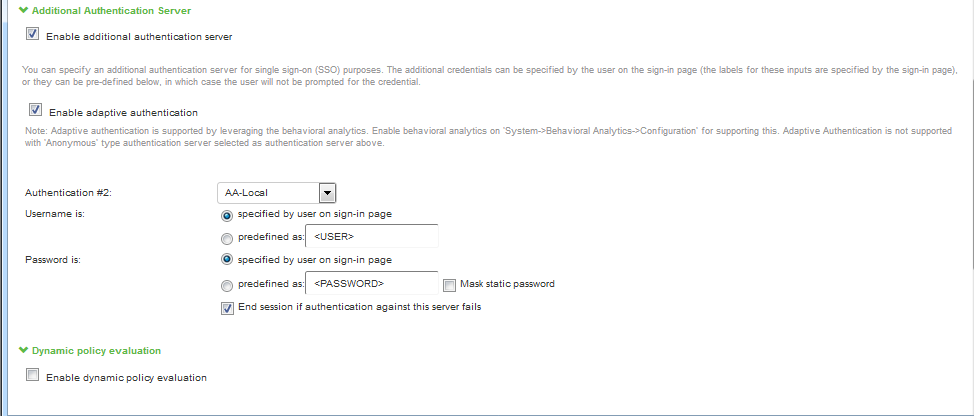
4.Navigate to Administrators > Admin Realms or Users > User Realms.
5.Under Additional Authentication Server, select Enable Additional Authentication Server.
•Select Enable adaptive authentication.
•Under Authentication #2, select the desired secondary authentication server from the drop-down list.
The following figure depicts the Additional Authentication Server:
6.Click Save Changes.
Dashboard and Reports
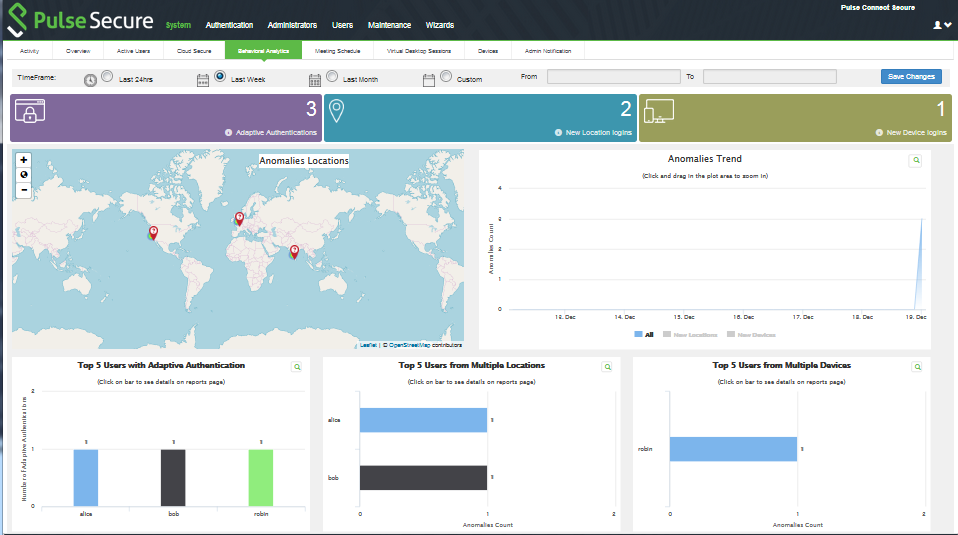
The Behavioral Analytics dashboard provides visibility to many anomalies in the network. It provides visibility of any known, active anomalies, devices with potential malware, IoT devices with anomalous traffic, anomalies location, trend and so on.
To view the Behavioral Analytics dashboard:
1.Select System > Status > Behavioral Analytics.
2.Select the desired timeframe from available options.
3.Click Save Changes.
You can also view the drill down reports such as:
•Top 5 Users with Adaptive Authentication
•Top 5 Users from Multiple Locations
•Top 5 Users from Multiple Devices
The following figure depicts the Behavioral Analytics Dashboard Page:
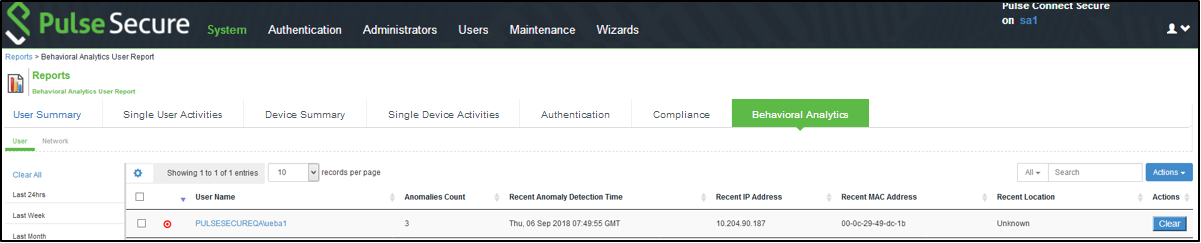
The Reports page is enhanced to view the behavioral analytics related reports. To view the reports, select System > Reports > Behavioral Analytics.
The following figure depicts the Behavioral Analytics Reports Page:
Troubleshooting
The event and debug logs can be used for troubleshooting.
The Event logs are generated for the user-related anomalies:
•User authentication from new device/location.
You can use the User Access and Admin Logs in case of any issues. The user access logs are generated whenever there are any user related anomalies such as user logging from new location/new user. The Admin Logs are generated whenever there is a change with Behavioral Analytics options and if there are any changes with respect to application policies.
You can also use Maintenance > Troubleshooting > Monitoring > Debug Log for debugging issues.