Dashboard
The Cloud Secure Dashboard captures the cloud secure applications that are getting accessed by users and the device platform from where these applications are getting accessed. It provides a consolidated view of the different applications being accessed to the administrators.
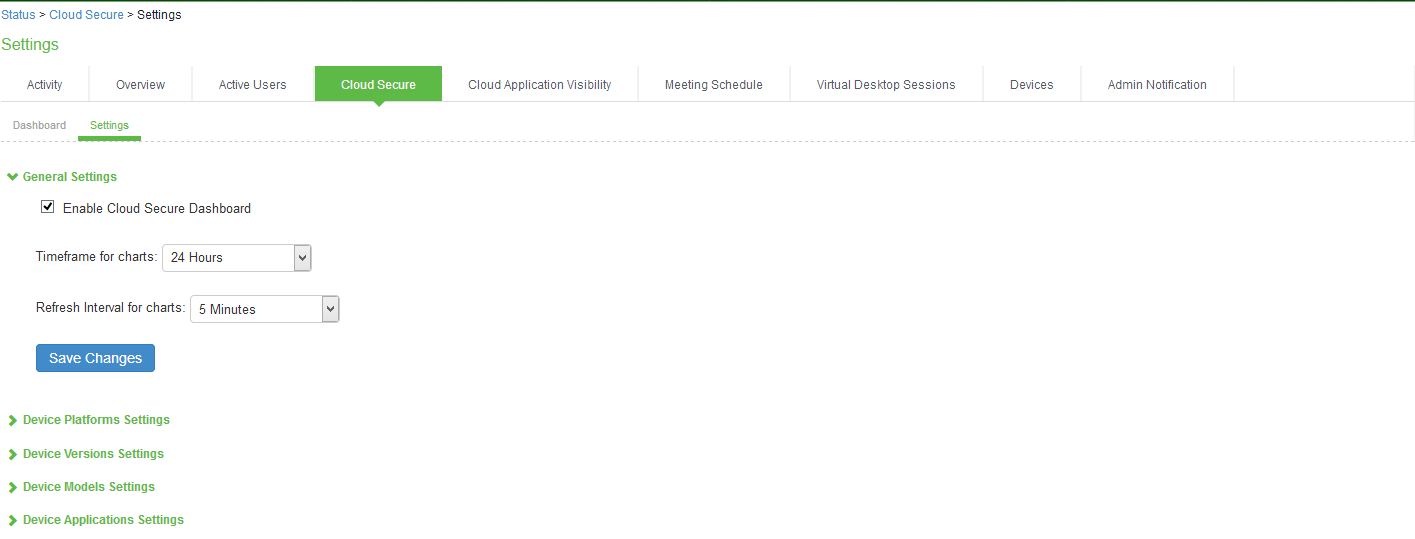
1.To improve the visibility and experience, administrators are given options to configure the regex patterns for matching the applications and device details to the display strings in dashboard. Select System > Status > Cloud Secure > Dashboard > Settings page:
- Enable the Dashboard by selecting Enable Cloud Secure Dashboard under General Settings.
- Configure the required Timeframe for the charts and Refresh interval under General Settings.
- Click Save Changes.
By default, some of the regular expression patterns for Device Platforms, Device Versions, Device Models and Applications are present on ICS.
2.Navigate to System > Status > Cloud Secure > Dashboard page for accessing the Cloud Secure Dashboard page.
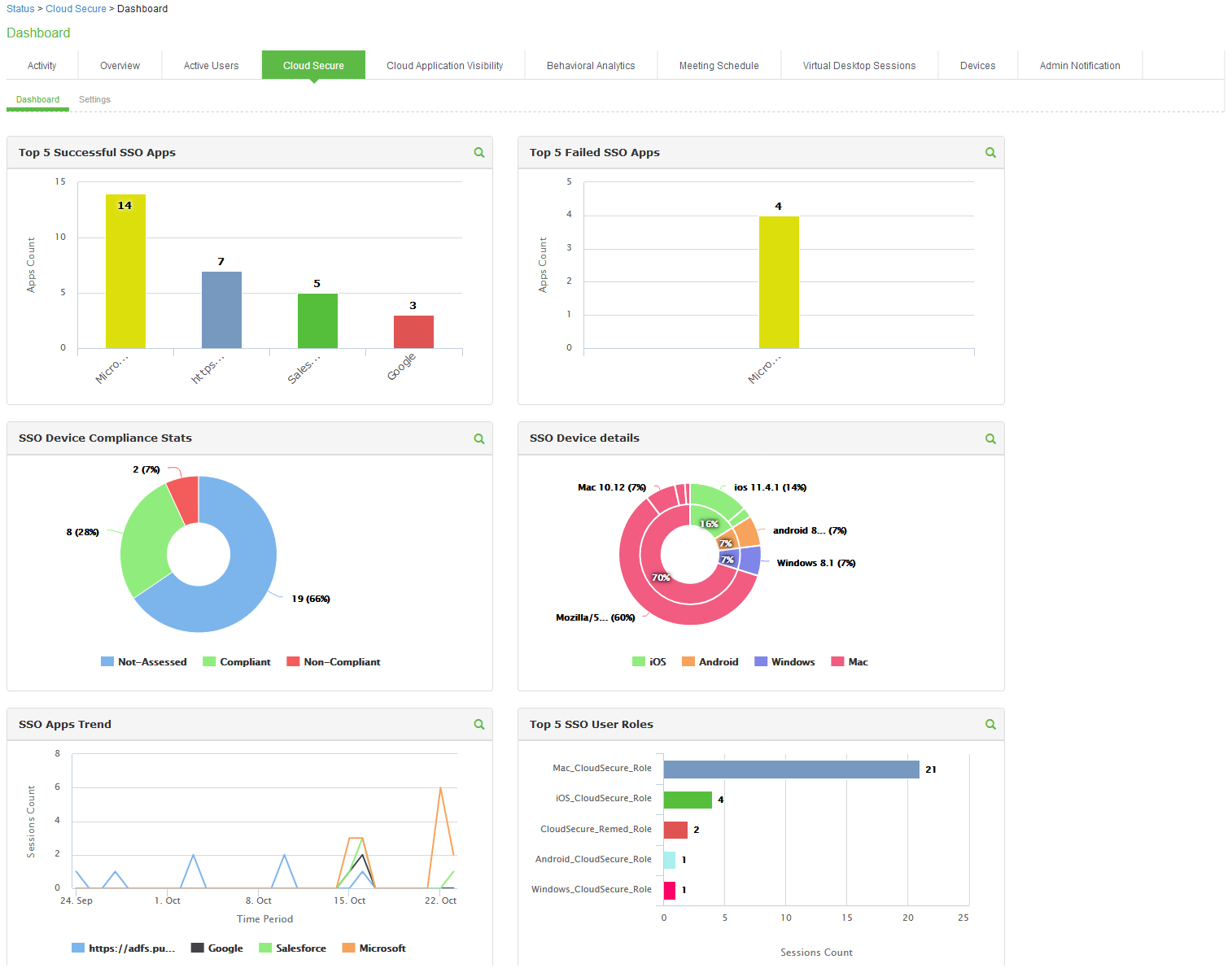
This page contains 6 charts capturing the applications and device details.
•Top 5 Successful SSO Apps: This chart is used for capturing the details about the applications that end users are able to access successfully. Top 5 such successful applications are represented in form of bar chart.
•Top 5 Failed SSO Apps: This chart captures details of applications for which access is failed for the end users. This chart displays top 5 such failed applications.
•SSO Device Compliance Details: This chart captures the details of compliance status of the devices from which users are accessing the applications. This chart captures the compliance status and represents them in the form of pie chart.
•SSO Device Details: This chart captures details of the device OS version and platform from which the applications are getting accessed. These details are captured in form of Donut chart.
•SSO Apps Trend: This chart contains details about applications trend. This captures trend of top 5 application in form of line chart.
•Top 5 SSO User Roles: This chart captures details about the roles that are given to the end users. This captures top 5 roles in form of bar chart.
Points to note:
•‘Top 5 Failed Apps’ chart captures details of only applications for which access failed due to Role Based Access Control restrictions or Compliance failure case on end user device.
•Admin can click on the search icon at the top of the chart (![]() ) to view the Cloud Secure report. The drill down report for the corresponding chart is displayed.
) to view the Cloud Secure report. The drill down report for the corresponding chart is displayed.
•All the counters in above charts are incremented once per VPN session. If same application is accessed more than once during same VPN session, it is still counted as one.
•Admin can zoom into any chart by clicking on the chart in the dashboard.