Ivanti Connect Secure Overview
As you plan your Pulse Client configuration, be sure you know how you want to deploy Pulse Client software. You can use one or more of the following Pulse Client deployment options:
•Use the defaults or make changes to the Pulse Connect Secure default component set and default connection set, and then download and distribute Pulse Client by having users log in to the Ivanti server’s user Web portal and be assigned to a role. After the installation is complete, users have all the connections they need to access network resources.
•Create the connections that an endpoint needs for connectivity and services, download the settings file (.pulsepreconfig), and download default Pulse Client installation program. For Windows endpoints you run the Pulse Client installation program by using an msiexec command with the settings file as an option. For OS X endpoints, you run the default installer and then import the .pulsepreconfig file using a separate command.
•Distribute Pulse Client with no preconfiguration. You can download the default Pulse Client installation file (.msi format for Windows; .dmg format for Mac) from Pulse Connect Secure, and then distribute the file to endpoints using your organization’s standard software distribution methods. Because the installer does not contain preconfigured connections, users must define network connections manually. Or you can create dynamic connections on each Pulse Connect Secure. These connections are automatically downloaded to the installed Pulse Client when users provide their login credentials to the Ivanti server’s user Web portal, and then starts Pulse Client through the Web portal interface. Dynamic connections are created as manual rather than automatic connections, which means that they are run only when the user initiates the connection or the user browses to a Pulse Connect Secure and launches Pulse Client from the server’s Web interface.
For a Windows installation (.msi) that uses an automated distribution mechanism and where the users do not have administrator privileges, you should ensure that the installation is run in the proper context, typically the USER context. To install in USER context, first advertise the .msi while in the SYSTEM context. For example, to advertise the 64-bit Windows installation to all users, use the following msiexec command:
The advertisement allows the installation to be run in USER context even if the user is a restricted (non-admin) user. The location where the advertisement is run and where the actual installation is run must be the same. If the installation is an upgrade, you must advertise the upgrade version before running it.
It is much easier to upgrade Pulse Client by not disabling the automatic upgrade feature on Ivanti Connect Secure.
After the installation is run by the user, Pulse Client will use the correct user certificate and context.
The following tasks summarize how to configure Ivanti Connect Secure
•Create and assign user roles to control who can access different resources and applications on the network. If you are converting your access environment from agentless or a Network Connect environment, you should create new roles that are specific for Pulse Client.
•Define security restrictions for endpoints with Host Checker policies.
•Define user realms to establish authentication domains. If you are converting your access environment from agentless or a NC environment, typically you can use your existing realms.
•Associate the roles with appropriate realms to define your access control hierarchy using role mapping.
•Define Pulse Client component sets, connection sets, and connections.
•Deploy Pulse Client to endpoints.
Pulse Client and IVS
Ivanti Connect Secure and Pulse Client do not support Instant Virtual System (IVS) feature anymore.
Pulse Client and Traffic Enforcement
The Traffic Enforcement feature (supported on Windows and macOS) enables the user to prevent the leakage of any packet out of the tunnel as per Ivanti Connect Secure tunnel configuration. This is accomplished by applying firewall rules in Pulse Client. These rules are created based on the Ivanti Connect Secure tunnel configuration.
For more information on Ivanti Connect Secure tunnel configuration policies, refer to the section “Defining Split Tunneling Network Policies” and “Defining the Route Precedence Options” of chapter “VPN Tunneling” of Ivanti Connect Secure Administration Guide.
A local program might bypass the routing tables and bind traffic to the physical interface instead of allowing it to go through the Pulse Client virtual interface. If you enable Traffic Enforcement, you ensure that all traffic is bound by the Ivanti Connect Secure tunnel configuration. Traffic Enforcement feature is more useful in macOS because of Apple routing behavior.
For example, If SSH session is created using physical adapter before VPN tunnel, the session will continue to use physical adapter even after the tunnel is established because of macOS scoped routing (Apple functionality). If Traffic Enforcement is enabled, the same SSH session gets terminated because firewall rule finds packet leaking out of tunnel from SSH session and it will deny that traffic.
Advanced Pulse Client Configuration Feature
This topic describes the XML advanced Pulse Client configuration that can be used by the Ivanti Connect Secure administrator to configure the custom settings, which are meant to solve a specific customer scenario without changing the Ivanti Connect Secure admin console. Admin can set these custom settings in the form of XML input through the Advanced Client Configuration UI feature. Pulse Clients supporting these custom settings will consume them when connecting to this Ivanti Connect Secure, and the same would be applied on Pulse Client machines. From 9.0R3 release onwards, this feature will minimize the number of changes going into the Ivanti Connect Secure admin console to fulfill the requirement of a specific customer.
In the earlier Pulse Client releases, i.e. prior to v5.2R2, the virtual adapter MTU was calculated based on the physical adapter MTU (of the host machine) and the MTU sent by the Ivanti Connect Secure.
Basically, the formula used to calculate the virtual adapter MTU is:
MIN (Physical Adapter MTU, MTU from Ivanti Connect Secure, TCP MSS value + 40)
Following is a scenario where Firewall on the data path is stripping the TCP MSS options being advertised by the SA/Ivanti Connect Secure to Pulse Client. In this scenario, the TCP MSS value on Pulse Client will default to a minimum value of 536, and as a result the client-side MTU calculation will result in a minimum MTU value of 576. Here, customer wants to ignore the TCP MSS options while calculating the Virtual Adapter MTU calculation.
If the administrator configures the Ivanti Connect Secure server with the following XML input in “Advanced Client Configuration for Pulse Clients” option, it will ignore TCP MSS options while calculating the virtual adapter MTU on client side.
1.Select System > Configuration > Advanced Client Configuration to display the configuration page.
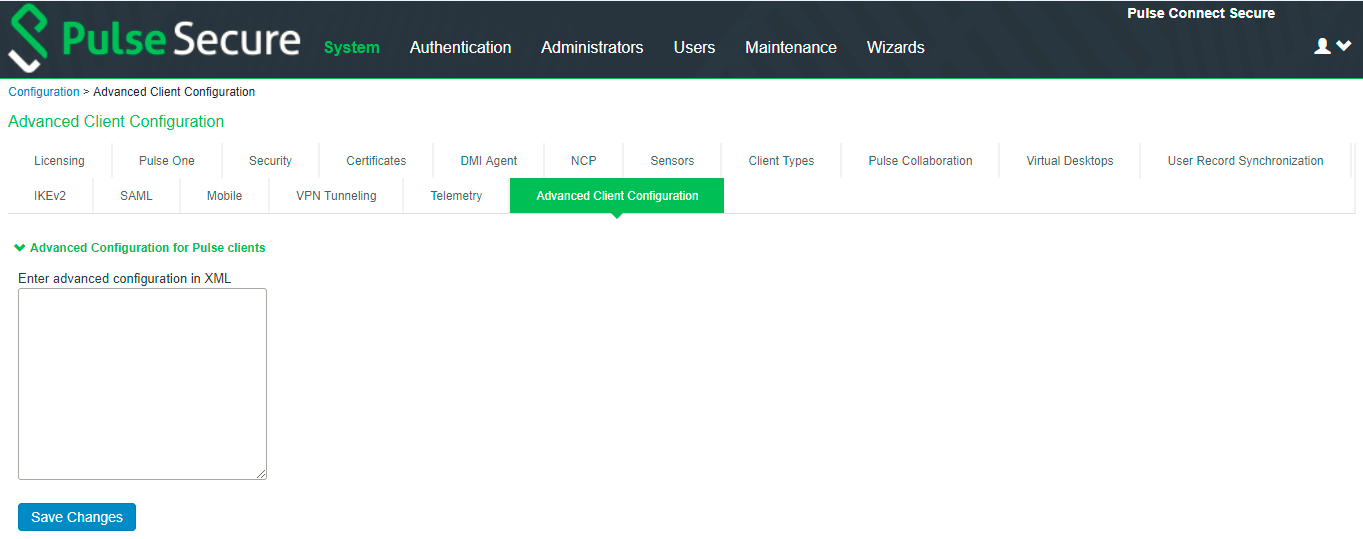
2.Enter the following XML input in “Advanced Client Configuration for Pulse Clients”.
<advanced-config>
<version>9.0.3</version>
<desktop-client-config>
<layer3-connection-config>
<adapter-config>
<ignore-tcp-mss>TRUE</ignore-tcp-mss>
</adapter-config>
</layer3-connection-config>
</desktop-client-config>
</advanced-config>
3.Click Save Changes.
The advanced configuration setting "ignore-tcp-mss" is Layer3 Adapter configuration setting and this will be consumed by Pulse Client as part of the IpsecConfig.
This “ignore-tcp-mss” setting is applicable for the virtual adapter MTU calculation only for IPv4. By default the setting is always false, and therefore the TCP MSS options are always considered for MTU by default. Admin has to explicitly set the ignore-tcp-mss setting to TRUE (case-insensitive), to ignore the TCP MSS.
Disabling NetBIOS driver Using Advanced Client Configuration
This feature provides an option to enable/disable the NetBIOS configurations permanently on the Network Adaptor.
On the ICS UI, navigate to System > Configuration > Advance Client Configuration. Under, Advanced Configuration for Pulse Clients, set the <disable-Netbios> flag to “True”.
Disabling JNPRNS driver Using Advanced Client Configuration
JNPRNS is a Network Driver Interface Specification (NDIS) based Light Weight Filter (LWF) driver used for certain operations in IPSEC SRX L3 Flow. By default, JNPRNS driver is enabled on all the network adapters associated with PDC. Enabling JNPRNS driver can affect the upload and download performance on normal SSL/ESP L3 VPN. To improve the speed, you can disable JNPRNS driver.
Use any one of the methods to disable JNPRNS driver:
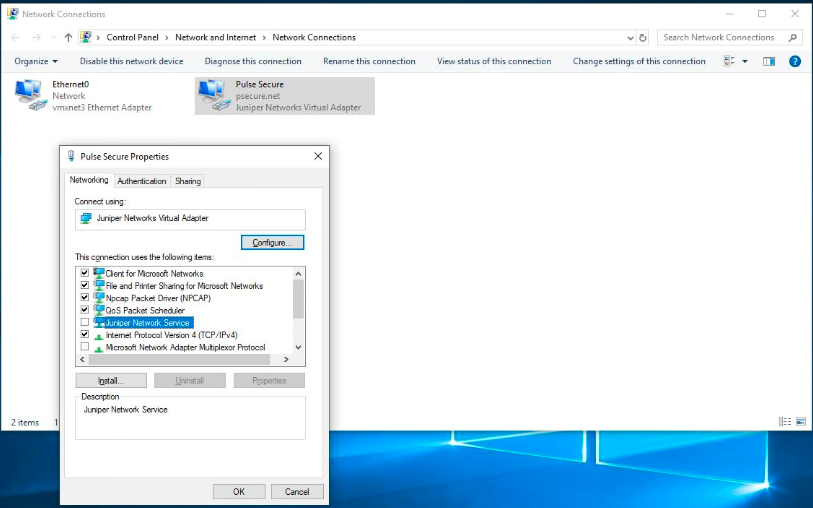
•On windows endpoint, disable JNPRNS driver manually from the network adapter stack using the powershell command
Disable-NetAdapterBinding -Name * -DisplayName "Juniper Network Service"
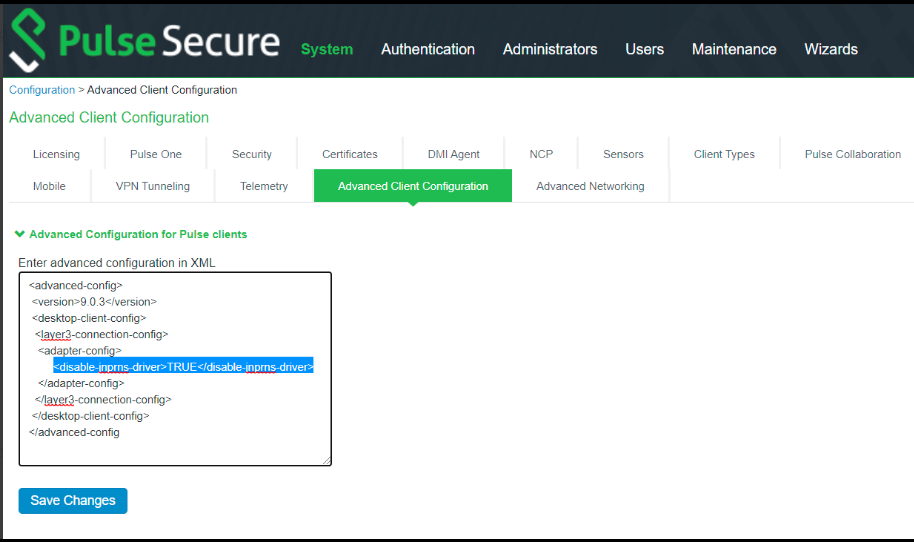
•On the ICS UI, navigate to System --> Configuration --> Advance Client Configuration. Under, Advanced Configuration for Pulse Clients, set the <disable-jnprns-driver> flag to “True” as shown in the figure.
This setting is applicable for clients running on Windows 10 operating system only.