Pulse Client Connection Set Options for Pulse Policy Secure
A Pulse Client connection set contains network options and allows you to configure specific connection policies for client access to any Pulse Secure server that supports Pulse Client. The following sections describe each of the configuration options for a Pulse Client connection set.
Pulse Client Connection Set Options
The following items apply to all connections in a connection set.
•Allow saving logon information: Controls whether the Save Settings check box is available in login dialog boxes in Pulse Client. If you clear this check box, Pulse Client always requires users to provide credentials. If you select this check box, users have the option of saving their credentials.
Pulse Client can retain learned user settings. These settings are retained securely on the endpoint, evolving as the user connects through different Pulse Secure servers. Pulse Client can save the following settings:
•Certificate acceptance
•Certificate selection
•Realm
•Username and password
•Proxy username and password
•Secondary username and password
•Role
If the authentication server is an ACE server or a RADIUS server and authentication is set to Users authenticate using tokens or one-time passwords, Pulse Client ignores the Allow saving logon information option. If the user sees a username and token prompt and the Save settings check box is disabled. Pulse Client supports soft token, hard token, and smart card authentication.
When a user opts to save settings, that information is used for each subsequent connection without prompting. If a setting changes (for example, if a user changes a password), the saved setting is invalid and connection attempts fail. In this case, the user must use the client's Forget Saved Settings feature, which clears all user-saved settings.
•Allow user connections: Controls whether connections can be added by the user.
•Display splash screen: Clear this check box to hide the Pulse Client splash screen that normally appears when Pulse Client starts.
•Dynamic certificate trust: Determines whether users can opt to trust unknown certificates. If you select this check box, a user can ignore warnings about invalid certificates and connect to the target Pulse Secure server.
By default, Dynamic certificate trust check box will be unchecked.
•Dynamic connections: Allows connections within this connection set to be automatically updated or added to a Pulse Client when the user connects to the Pulse Secure server through the user Web portal, and then clicks the Pulse Secure button. Dynamic connections are created as manual rather than automatic connections, which means that they are run only when the user initiates the connection or the user browses to a Pulse Secure server and launches Pulse Client from the server's Web interface.
If dynamic connections are disabled, and the user logs in through the Web portal of a Pulse Secure server that is not already included in Pulse Client's connection set, then starting Pulse Client from the Web portal does not add a new Pulse Client connection for that Pulse Secure server. If you choose to disable dynamic connections, you can still allow users to manually create connections by enabling Allow User Connections.
•FIPS mode enabled: Enable FIPS mode communications for all Pulse Client connections in the connection set. The Federal Information Processing Standard (FIPS) defines secure communications for the U.S. government. When a Pulse Client connection is operating in FIPS mode, "FIPS On" appears in the lower corner of the Pulse Client interface. If the Pulse Secure server hardware does not support FIPS mode operations, FIPS mode configuration options are not present in the admin console interface. FIPS mode operations are supported on PSA-V Series Pulse Secure Gateways and some SA series appliances. The device must be running Pulse Policy Secure R5.0 or later or Pulse Connect Secure R8.0 or later.
Users cannot enable FIPS mode from within Pulse Client. You must create FIPS-enabled connections on the server and deploy them.
•Wireless suppression: Disables wireless access when a wired connection is available. If the wired connection is removed, Pulse Client enables the wireless connections with the following properties:
•Connect even if the network is not broadcasting.
•Authenticate as computer when computer information is available.
•Connect when this network is in range.
Wireless suppression occurs only when the wired connection is connected and authorized. If you enable wireless suppression, be sure to also configure a connection that enables the client to connect through a wired connection.
UAC 802.1X Connection Type Options
Use this connection type to define authenticated connectivity to 802.1X devices, wired or wireless. Users cannot create 802.1X connections from the Pulse Client interface. Users see 802.1X connections in the Pulse Client interface only when the connection has been deployed from the server and the specified network is available.
When configuring an 802.1x connection, Pulse Policy Secure will force Pulse Client to connect using Client IP Address of the same family as of the specified Radius Client's IP Family. When you specify Radius Client as IPV6, Pulse Policy Secure will allow Pulse Client to connect only using IPv6 address in 802.1x scenario. Also Pulse Client does not consider link-local IPv6 Addresses to complete an 802.1x Connection in a scenario where it needs an IPv6 address to connect to Pulse Policy Secure. For more information see PPS Admin Guide.
•Adapter type: Specifies the type of adapter to use for authentication: wired or wireless.
•Outer username: Enables a user to appear to log in anonymously while passing the actual login name (called the inner identity) through an encrypted tunnel. As a result, the user's credentials are secure from eavesdropping, and the user's inner identity is protected. In general, enter “anonymous”, which is the default value. In some cases, you might need to add additional text. For example, if the outer identity is used to route the user's authentication to the proper server, you might be required to use a format such as “[email protected]”.
If you leave the box blank, the client passes the users or the machine's Windows login name as the outer identity.
•Scan list: If you selected wireless as the adapter type, the scan list box is available to specify the SSIDs, including non-broadcast SSIDs, to connect to in priority order. If you leave the list empty, the user can connect to any available wireless network.
•Support Non-broadcast SSID: Allows a user to connect to a non-broadcast wireless network from within the Pulse Client interface. Selecting this field enables the following options:
•Wireless Security Algorithm: Specify wireless authentication:
•WPA
•WPA2
•Wireless Security Cipher: Specify the type of encryption used by the non-broadcast network:
•TKIP
•AES
If the non-broadcast SSID options are configured, the Pulse Client connection configuration includes the values and they are used to configure the wireless profile on the endpoint.
Trusted Server List (for UAC 802.1X Connection)
FQDN criteria for 802.1X/EAP server certificates (with wildcard support) can be specified in the Trusted Server List of the PPS admin console. In the name field, you can enter a fully-qualified-domain name (FQDN) that can be either an exact FQDN or an FQDN that begins with a "." and/or can contain wildcards ("*").
Note the Following:
•The "ANY" entry matches any server certificate name.
•An entry that contains "=" requires an exact Subject:DN (Distinguished Name) match.
•An entry that is neither "ANY" nor contains "=" is an FQDN. It can be either an exact value or include wildcards and/or begin with a "." character. This value will be checked against FQDNs in the server's certificate (Subject:DN:CN=…, SAN:DNS=…).
•An entry that begins with "." will wildcard only the first subdomain (domain component) in the FQDN. For example, " mycompany.com" will match "foo.mycompany.com" but not "foo.bar.mycompany.com". As such, a FQDN beginning with "." is equivalent to the same FQDN beginning with "." (e.g., ".mycompany.com" is equivalent to ".mycompany.com"). Note that this mechanism is more restrictive than what is described in RFC 5280.
•FQDN may contain at most one wildcard per domain component (DC). For example, "a.mycompany.com" is not allowed and will always result in authentication failure.
•A wildcard matches 1 or more characters (but not zero characters). For example, "f*r.mycompany.com" will match "foo-bar.mycompany.com" but not "fr.mycompany.com".
•See RFC 2818 and RFC 6125 for more details and security implications of wildcards.
•Be careful when mixing wildcard FQDN entries with certificates that contain wildcards in their names. For example, the entry "foo*.mycompany.com" will match a certificate with the name "*bar.mycompany.com".
•This wildcarding mechanism does not work with server certificates that contain the "?" character in their names. (This is not a common occurrence.)
•You can choose any server certificate's issuing certificate authority (CA) from the drop-down list. It could be the direct issuer or any CA at higher level in the certificate chain, up to the root.
Connect Secure or Policy Secure (L3) Connection Type Options
Use a Connect Secure or Policy Secure (L3) connection for a Layer 3 connection to Pulse Connect Secure or Pulse Policy Secure.
•Allow user to override connection policy: Allows a user to override the connection policy by manually connecting or disconnecting. Typically, you leave this option selected to make sure that a user can establish a connection under all conditions. If you disable this check box, the user cannot change the endpoint's connection status, suspend/resume a connection to Pulse Connect Secure or shut down Pulse Client.
•Support Remote Access (SSL VPN) or LAN Access (UAC) on this connection: This option must be selected if this connection is for Pulse Policy Secure. If the connection is for Pulse Connect Secure, you can disable this check box and use the connection for accessing Pulse Collaboration meetings only by also selecting Support Remote Access (SSL VPN) or LAN Access (UAC) on this connection.
•Enable Pulse Collaboration integration on this connection: This option must be disabled if this connection is for Pulse Policy Secure. If the connection is for Pulse Connect Secure, you can enable this check box and use the connection for accessing Pulse Collaboration meetings.
•Connect to URL of this server only: Specifies whether the endpoint connects to this Pulse Secure server exclusively or if it can connect to the any of the servers listed in the list of connection URLs. Disable this check box to enable the List of Connection URLs.
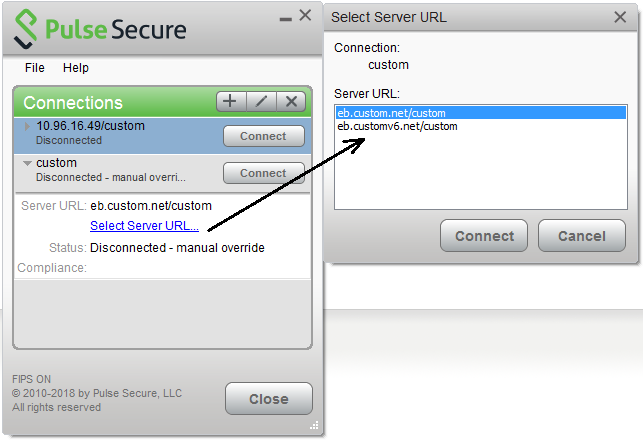
•List of Connection URLs: Allows you to specify a list of Pulse Secure servers (Pulse Policy Secure or Pulse Connect Secure) for this connection. Pulse Client attempts to reach each server in the list, in the order listed, until it succeeds. You can specify up to 8 Pulse Secure servers. If you enable the Randomize URL list order check box, Pulse Client ignores the listed order and chooses from the list randomly. If the Pulse Client connection is configured to use a list of Pulse Secure servers, any preferred roles and realms you specify must be applicable to all of those servers. The default behavior is to start with the most recently connected URL first, then try from top of list. The most recently connected URL is saved across reboots. Connections that use machine authentication always use the ordered list of connection URLs. In the case of an interrupted connection, such as temporarily losing the WiFi link, Pulse Client always tries to reconnect to the most recently connected URL. During a credential provider connection attempt, Pulse Client chooses the URL automatically. It does not display a window to let the user choose a URL. Figure shows how the Pulse Client user can select a server from the list of connection URLs.
•Attempt most recently connected URL first: If you have specified a list of connection URLs, you can select this check box to have Pulse Client always attempt the most recent successful connection. If that connection is not successful, Pulse Client then starts at the top of the list.
•Randomize URL list order: If you have specified a list of connection URLs, select this check box to have Pulse Client ignore the order in which the servers are listed. You can select this option to spread the connection load across multiple Pulse Secure servers. If you enabled Attempt most recently connected URL first, then Pulse Client attempts that connection first. If that connection attempt fails, Pulse Client chooses randomly from the list for the next connection attempt. During a credential provider connection attempt, Pulse Client chooses the URL automatically. It does not display a window to let the user choose a URL.
- IF-MAP federation must be configured to ensure that a suspended session can be resumed to a different URL.
- When this feature is used with Pulse Policy Secure, all of the Pulse Secure servers in the list must be configured for failover, so that any one of them can provision the firewall enforcer.
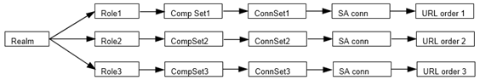
The connection list enables you to support different URL ordering for different users. You can use custom expressions in a realm's role mapping rules to associate different users to different roles. For example, you could use a custom expression that is based on the OU (Organization Unit) when using an LDAP authentication server, (UserDN.OU = "Americas"). Each role is associated with a different Pulse Client connection set, and each Pulse Client connection within the connection set is configured with different URL lists. Figure shows the role mapping for providing different URL lists for different users.
SRX (for Dynamic VPN) Connection Type Options
Use an SRX connection for a dynamic VPN connection to an SRX Series Services Gateway.
•Address: Specifies the IP address of the SRX Series device.
•Allow user to override connection policy: Allows users to override the connection policy by manually connecting or disconnecting. Typically, you leave this option selected to make sure that a user can establish a connection under all conditions. If you disable this check box, the user cannot change the endpoint's connection status or shut down Pulse Client.
Pulse Client Connection is Established Options
For all connection types, specify how the connection is established. The options vary according to the type of connection. Automatic connections include machine authentication and credential provider connections. Connections can be established using the following options.
All connections that are configured to start automatically attempt to connect to their target networks at startup time. To avoid multiple connection attempts, be sure that only one connection is configured to start automatically, or configure location awareness rules.
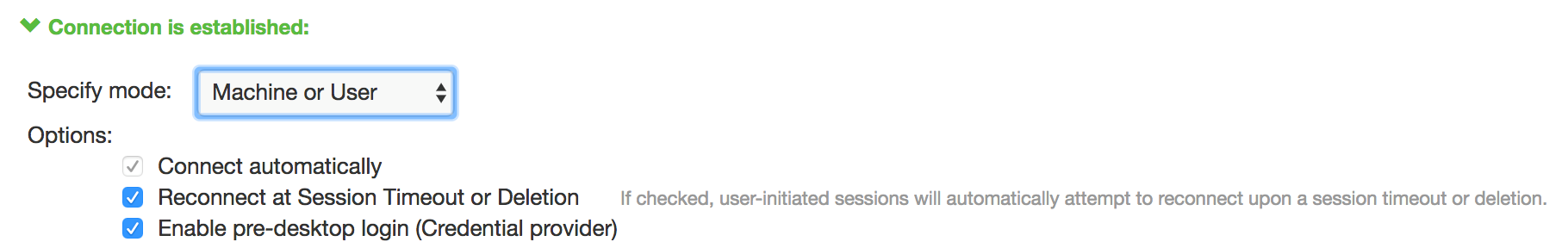
•Modes:
•User: Enables user authentication.
•Machine: Enables machine authentication, which requires that Active Directory is used as the authentication server and that machine credentials are configured in Active Directory. A machine connection is, by default, an automatic connection.
•Machine or user: Enables machine authentication for the initial connection. After user authentication, the machine authentication is dropped. When the user logs out, the machine authentication connection is restored.
•Options:
•Connect automatically: Connections are attempted when the conditions specified in the location awareness rules are true, and disconnected when the conditions are no longer true.
•Enable pre-desktop login (Credential provider): Enables Pulse Client interaction with the credential provider software on the endpoint. The user credentials are used to establish the authenticated Pulse Client connection to the network, login to the endpoint, and login to the domain server.
•Reconnect at Session Timeout or Deletion): If this option is enabled, user initiated sessions automatically attempt to reconnect upon a session timeout or deletion. If this option is disabled, then user initiated sessions remain disconnected upon a session timeout or deletion.
Pulse Client Connection is Established Examples
The following configurations show how to select the Connection is established options of a Pulse Client connection set for specific user login behavior:
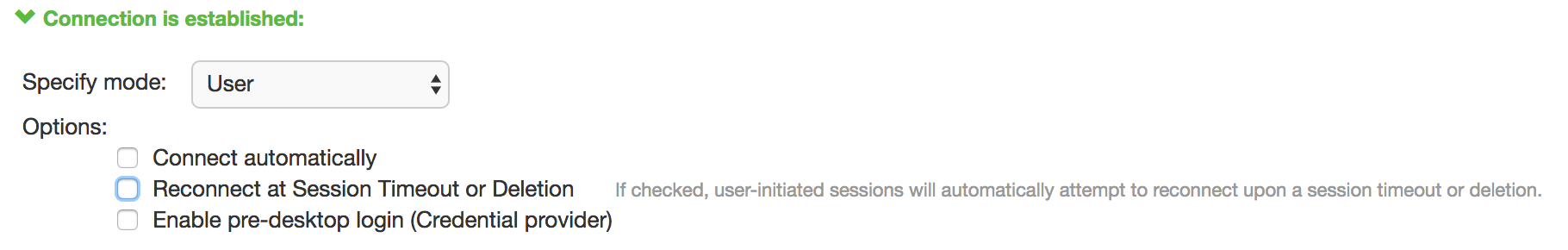
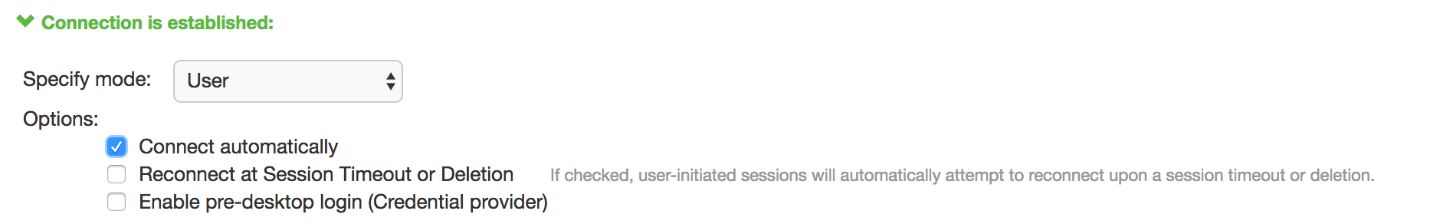
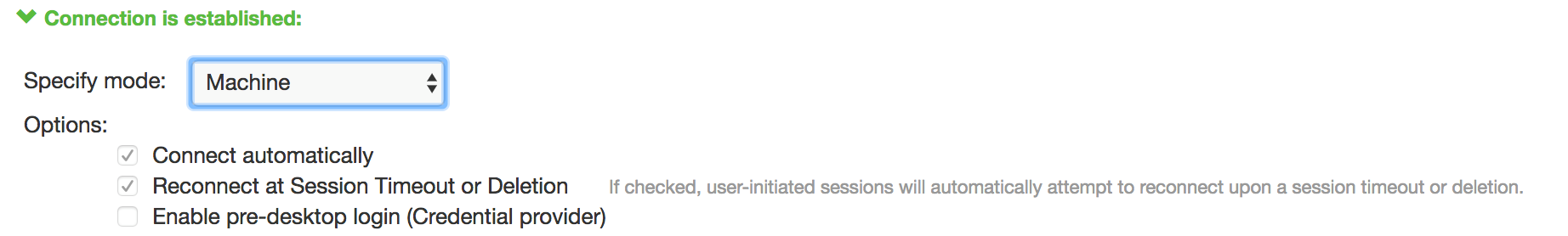
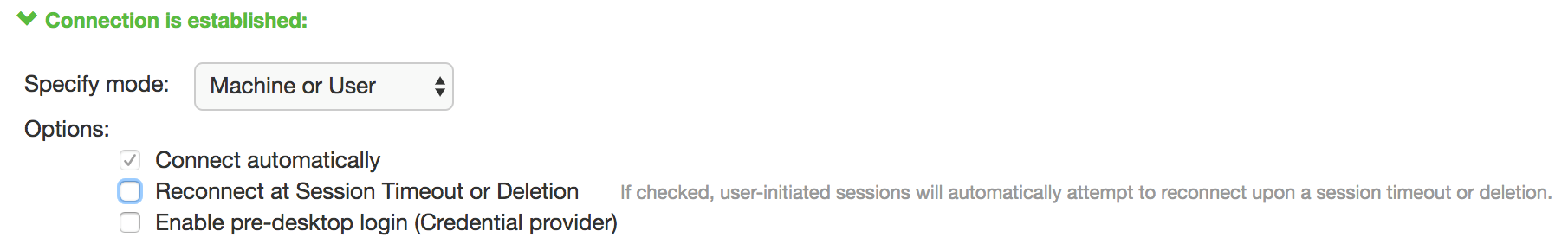
When you use machine credentials for authentication and no user credentials, Pulse Client cannot perform user-based tasks. The following tasks can be run only when the user is logged in:
- Run session scripts
- Detect or modify proxy settings
- Run automatic Pulse Client upgrade
- Install or upgrade Pulse Client components
The configuration in figure enables machine authentication for the initial connection. After the user connects with user credentials, the machine authentication is dropped. When the user logs out, the machine authentication connection is restored. In one typical use case, the machine credentials provide access to one VLAN, and the user credentials provide access to a different VLAN.
If the machine and user have different roles, each role should map to the same connection set. Otherwise, after the user connects, the existing connection set might be replaced.
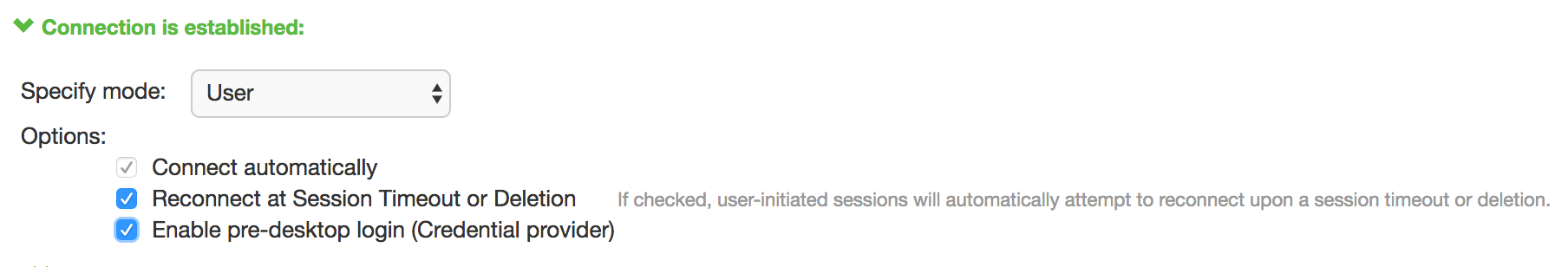
The configuration in figure enables Pulse Client interaction with the credential provider software on the endpoint. The user credentials are used to establish the authenticated Pulse Client connection to the network, to log in to the endpoint, and to log in to the domain server.
The configuration in enables Pulse Client interaction with the credential provider software on the endpoint. Machine credentials are used to establish the authenticated Pulse Client connection to the network. When the user provides user credentials, the connection is authenticated again. In one typical use case, the machine credentials provide access to one VLAN, and the user credentials provide access to a different VLAN.
Location Awareness Rules
For Connect Secure or Policy Secure (L3) and SRX connections that are set to have the connection established automatically, you should define location awareness rules that enable an endpoint to connect conditionally. If you do not have location awareness rules defined, Pulse Client attempts to connect with each connection that is defined as an automatic connection until it connects successfully. Location awareness rules allow you to define an intelligent connection scheme. For example, the endpoint connects to Pulse Policy Secure if it is connected to the company intranet, or it connects to Pulse Connect Secure if it is in a remote location.
A Pulse Client connection uses the IP address of a specified interface on the endpoint to determine its network location. Each location awareness rule includes the following settings:
•Name: A descriptive name, for example, "corporate-DNS." A name can include letters, numbers, hyphens, and underscores.
•Action: The method the connection uses to discover the IP address. Choose one of the following values:
•DNS Server: Allows the endpoint to connect if the endpoint's DNS server on the specified interface is set to one of the specified values. Use the Condition box to specify IP addresses or address ranges.
•Resolve Address: Allows the endpoint to connect if the hostname specified in the DNS Name box can be resolved by the DNS server for the specified interface. If one or more address ranges are specified in the Address Range box, the address must resolve to one of the ranges to satisfy the expression.
•Endpoint Address: Allows the endpoint to connect if the IP address of the specified interface is within a range specified in the IP Address Range box.
To create a negative location awareness rule, you first create the positive state and then use rule requirement logic to use the rule as a negative condition.
Machine Connection Preferences
The Machine Connection Preferences appear if you have selected one of the machine authentication options for how the connection is established. Normally Pulse Client presents a selection dialog box if more than one realm or role is available to the user. However, a connection that is established through machine authentication fails if a dialog box is presented during the connection process. To suppress the selection dialogs, either ensure that only one role and realm is available to users, or specify a preferred realm and role for this connection.
•Preferred Machine Realm: Specify the realm that this connection uses when establishing the machine connection. The connection ignores any other realm available for the specified login credentials
•Preferred Machine Role Set: Specify the role or the name of rule for the role set that this connection uses when establishing the machine connection. The role or rule name used must be a member of the preferred machine realm.
User Connection Preferences
The User Connection Preferences options enable you to specify a realm and role for automatic connections that would otherwise present a selection dialog box to the user. To suppress the selection dialogs, either ensure that only one role and realm is available to users, or specify a preferred realm and role for this connection.
If the Pulse Client connection is configured to use a list of Pulse Secure servers, the preferred roles and realms you specify must be applicable to all of those servers.
•Preferred User Realm: Specify the realm for this connection that is used when a user logs onto the endpoint. The connection ignores any other realm available for the user's login credentials
If one of the credential provider connection options is enabled, the following options are available:
•Preferred Smartcard Logon Realm: Preferred realm to be used when user logs in with a smart card.
•Preferred Password Logon Realm: Preferred realm to be used when user logs in with a password.
Be sure that the authentication realms you specify exist, and that they support the appropriate login credential option.
•Preferred User Role Set: Specify the preferred role or the name of the rule for the role set to be used for user authentication. The role or rule name used must be a member of the preferred user realm.
•Select client certificate from machine certificate store: Enables you to specify the location of the client certificate on a Windows endpoint as part of a Pulse Client connection that verifies the identity of both the machine and the user before establishing a connection. When this check box is selected, the Pulse Client connection looks at client certificates located in the Local Computer personal certificate store. When this check box is not selected, the connection accesses the user certificate store a Windows endpoint. For more information, see Machine and User Authentication Through a Pulse Client Connection for Pulse Policy Secure.
Related Documentation
Creating a Pulse Client Connection Set for Pulse Policy Secure
A Pulse Client connection (also called a client configuration) set contains network options and allows you to configure specific connection policies for client access to any Pulse Secure server that supports Pulse Client.
To create a Pulse Client configuration:
1.From the admin console, select Users > Pulse Secure > Connections.
2.Click New.
3.Enter a name and, optionally, a description for this connection set.
You must enter a connection set name before you can create connections.
4.Click Save Changes.
5.From the main Pulse Client Connections page, select the connection set.
6.Under Options, select or clear the following check boxes:
•Allow saving logon information: Controls whether the Save Settings check box is available in login credential dialog boxes in Pulse Client. If you clear this check box, Pulse Client always requires users to provide credentials. If you select this check box, users have the option of saving their credentials.
•Allow user connections: Controls whether connections can be added by the user through the Pulse Client interface.
•Display splash screen: Clear this check box to hide the Pulse Client splash screen that normally appears when Pulse Client starts.
•Dynamic certificate trust: Determines whether users can opt to trust unknown certificates. If you select this check box, a user can ignore warnings about invalid certificates and connect to the target Pulse Secure server.
By default, Dynamic certificate trust check box will be unchecked.
•Dynamic connections: Allows new connections to be added automatically to Pulse Client when the user connects through the Pulse Secure server's Web portal and then starts Pulse Client through the Web portal interface.
•FIPS mode enabled: Enable FIPS mode communications for all Pulse Client connections in the connection set. The Federal Information Processing Standard (FIPS) defines secure communications for the U.S. government. When a Pulse Client connection is operating in FIPS mode, "FIPS On" appears in the lower corner of the Pulse Client interface. If the Pulse Secure server hardware does not support FIPS mode operations, FIPS mode configuration options are not present in the admin console interface. FIPS mode operations are supported on PSA-V Series Pulse Secure Gateways and some SA series appliances. The device must be running Pulse Policy Secure R5.0 or later or Pulse Connect Secure R8.0 or later.
Users cannot enable FIPS mode for connections that are created on the client. You must deploy connections with FIPS mode enabled using a pre-configured connection set with FIPS mode enabled or have users establish a browser session to the FIPS enabled Pulse Secure server.
•Wireless suppression: Disables wireless access when a wired connection is available. Wireless suppression occurs only when the wired connection is connected and authorized.
7.Under Connections, click New to define a new connection.
8.Enter a name and, optionally, a description for this connection.
9.Select a type for the connection. Type can be any of the following:
•UAC 802.1X
•Connect Secure or Policy Secure (L3)
•SRX
10.1If you select UAC 802.1X from the type list, enter a value or select or clear the following check boxes:
•Adapter type: Select Wired or Wireless.
•Outer username: Enter the outer username.
•Scan list: If you selected wireless as the adapter type, the scan list box is available to specify the SSIDs, including non-broadcast SSIDs, to connect to in priority order. If you leave the list empty, the user can connect to any available wireless network.
•Support Non-broadcast SSID: Allow users to connect to a non-broadcast wireless network from within the Pulse Client interface.
11.Wireless Security Algorithm: Specify the type of wireless security that the client uses to connect to the non-broadcast wireless network:
•WPA
•WPA2
12.Wireless Security Cipher: Specify the type of encryption that the client uses to communicate with the non-broadcast network:
•TKIP
•AES
13.Click Save Changes.
14.If you selected "Connect Secure" or "Policy Secure (L3)" for the type, configure the following:
•Allow user to override connection policy
If you disable this check box, the user cannot change the endpoint's connection status or shut down Pulse Client.
•Enable Pulse Collaboration integration on this connection
•Support Remote Access (SSL VPN) or LAN Access (UAC) on this connection
•Connect to URL of this server only: Specifies whether the endpoint connects to this Pulse Secure server exclusively or if it can connect to the any of the servers listed in the list of connection URLs. Disable this check box to enable the List of Connection URLs.
•List of Connection URLs: Allows you to specify a list of Pulse Secure servers (Pulse Policy Secure or Pulse Connect Secure) for this connection. Pulse Client attempts to reach each server in the list, in the order listed, until it succeeds. You can specify up to 8 Pulse Secure servers. If you enable the Randomize URL list order check box, Pulse Client ignores the listed order and chooses from the list randomly. If the Pulse Client connection is configured to use a list of Pulse Secure servers, any preferred roles and realms you specify must be applicable to all of those servers.
•Start with most recently connected URL first, then try from top of list. The most recently connected URL is saved across reboots.
•Connections that use machine authentication ignore this option and always use the ordered list of connection URLs.
•In the case of an interrupted connection, such as temporarily losing the WiFi link, Pulse Client always tries to reconnect to the most recently connected URL.
•During a credential provider connection attempt, Pulse Client chooses the URL automatically. It does not display a window to let the user choose a URL.
•Randomize URL list order: If you have specified a list of connection URLs, select this check box to have Pulse Client ignore the order in which the servers are listed. You can select this option to spread the connection load across multiple Pulse Secure servers. If you enabled Attempt most recently connected URL first, Pulse Client attempts that connection first. If that connection attempt fails, Pulse Client chooses randomly from the list for the next connection attempt. During a credential provider connection attempt, Pulse Client chooses the URL automatically. It does not display a window to let the user choose a URL.
- IF-MAP federation must be configured to ensure that a suspended session can be resumed to a different URL.
- When this feature is used with Pulse Policy Secure, all of the Pulse Secure servers in the list must be configured for failover so that any one of them can provision the firewall enforcer.
•Client Certificate Location: Enables you to specify the certificate store that Pulse Client accesses for certificate authentication on Windows endpoints. Typically, you would use the default setting, which retrieves the certificate from the user's personal certificate store, and then certificate authentication is controlled by the Connection is established option. If you disable this option, the Pulse Client connection uses a machine certificate from the Local Computer Personal certificate store, which enables you to perform machine authentication and user authentication for the Pulse Client connection. If you disable this option, you must also create a sign-in policy and configure authentications servers to perform the user authentication.
15.If you select "SRX", enter the IP address of the SRX device in the Address box and specify whether you want the user to be able to override connection policy.
16.Specify how the connection is established, manually or automatically. These options enable you to configure machine authentication and credential provider authentication.
17.(Optional) You can enable location awareness on automatic connections by creating location awareness rules. Location awareness can force a connection to a particular interface.
18.(Optional) You can set preferred role and realm options for a machine authentication connection.
If the Pulse Client connection is configured to use a list of Pulse Secure servers, the preferred roles and realms you specify must be applicable to all of those servers.
19.After you have created the client connection set, create a client component set and select this connection set.