Using an LDAP Server
This topic describes integration with the LDAP server.
LDAP Server Overview
This section describes support for using PPS with the LDAP server.
Understanding LDAP Server
Lightweight Directory Access Protocol (LDAP) facilitates the access of online directory services. The Internet Engineering Task Force (IETF) designed and specified LDAP as a better way to make use of X.500 directories, having found the original Directory Access Protocol (DAP) too complex for average Internet clients to use. LDAP is a relatively simple protocol for updating and searching directories running over TCP/IP.
LDAP directory consists of a collection of attributes with a name, known as a distinguished name (DN). Each of the entry’s attributes, known as a relative distinguished name (RDN), has a type and one or more values. The types are typically mnemonic strings, such as CN for common name. The valid values for each field depend on the types.
The full DN is constructed by stringing together RDNs from most specific to least specific, separated by commas, as shown in the following example:
cn=Bob_Employee, ou= account_mgr, o=sales, dc=Acme,dc=com.
LDAP Feature Support
Pulse Secure access management framework supports the following LDAP features:
•LDAP directory services to retrieve user attributes and group membership in role mapping rules
•Encrypted connections to the LDAP server using LDAP over SSL (LDAPS) or Start Transport Layer Security (TLS)
•Password management feature enabling users who access an LDAP server to manage their passwords using the policies defined on the LDAP server
•Fine-grained password policy (FGP) for Active Directory 2008
Interoperability Requirements and Limitations
The following limitations apply to interoperability with LDAP:
•By default, challenge response protocols are disabled for LDAP servers. Use these protocols only with noninteractive devices (for example, phones), as password management is not possible if these protocols are used for authentication.
•To use the CHAP, EAP-MD5-Challenge, MS-CHAP-V1, and MS-CHAP-V2 protocols, the LDAP server must store the user’s password in clear text.
•Backup LDAP servers must be the same version as the primary LDAP server. Also, we recommend that you specify the IP address of a backup LDAP server instead of its hostname, which might accelerate failover processing by eliminating the need to resolve the hostname to an IP address.
Configuring Authentication with an LDAP Server
To configure authentication with an LDAP server:
1.Select Authentication > Auth. Servers.
2.Select LDAP Server and click New Server to display the configuration page.
3.Complete the configuration as described in table.
4.Save the configuration.
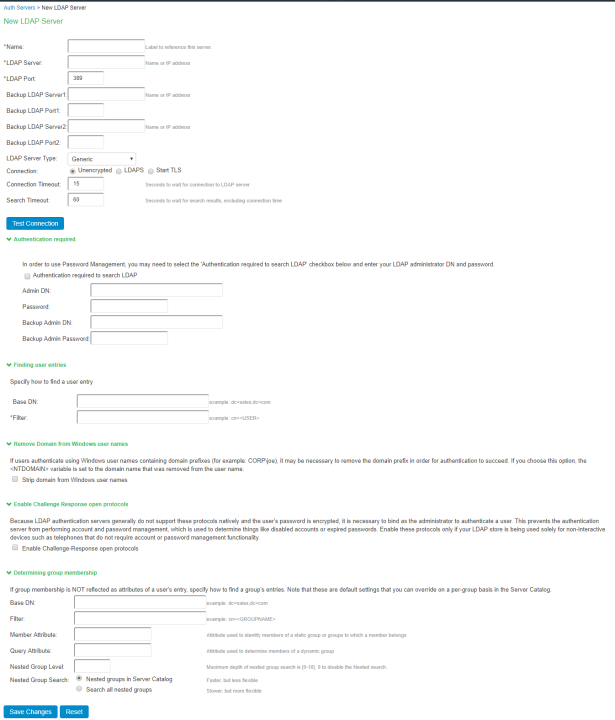
|
Settings |
Guidelines |
|
Name |
Specify a name to identify the server within the system. |
|
Enable Domain Name(enabled) |
Select this option to fetch a list of servers from the DNS server. |
|
|
Domain Name When you Enable Domain Name, specify the LDAP Domain name that can be mapped to domain controllers by DNS service. |
|
Enable Domain Name (disabled) |
Clear this option if you want to manually enter all the domain controllers host names. |
|
LDAP Server: Specify the LDAP server name or the IP address. Backup LDAP Server1: (Optional) Specify the parameters for backup LDAP server1. The specified backup LDAP server is used for failover processing. The authentication request is first routed to the primary LDAP server, and then to the specified backup servers if the primary server is unreachable. |
|
| Backup LDAP Port1: Specify the parameters for backup LDAP port1. | |
| Backup LDAP Server2: (Optional) Specify the parameters for backup LDAP server2. | |
|
LDAP Port |
Specify the LDAP port for the LDAP server. Default port number: 389 (unencrypted connection) Default port number: 636 (SSL connection) |
|
LDAP Server Type |
Select the backend LDAP server type from the following choices: Generic Active Directory iPlanet Novell eDirectory Profiler (Policy Secure only) |
|
Connection |
Select one of the following options for the connection to the LDAP server: Unencrypted– The device sends the username and password to the LDAP Directory Service in clear text. LDAPS– The device encrypts the data in the LDAP authentication session using the Secure Socket Layer (SSL) protocol before sending it to the LDAP Directory Service. Start TLS– The device allows both secure and plain requests against an LDAP server on a single connection. - If you select LDAPS or Start TLS, the Validate Certificate option is displayed for the configured LDAP server(s) and its referral servers. Select this option if the SSL connection uses digital certificate security. |
|
Connection Timeout (seconds) |
Specify the time to wait for connection to the primary LDAP server, and then to each backup LDAP server. Default: 15 seconds |
|
Sarch Timeout (seconds) |
Specify the time to wait for search results from a connected LDAP server. |
|
Test Connection |
(Optional) To verify the connection between Pulse Secure client and LDAP servers, click the Test Connection button. We recommend using the Test Connection function only after saving changes on the LDAP Server Configuration page. |
|
Authentication required? |
|
|
Authentication required to search LDAP |
Select this option to require authentication when performing search or password management operations. - If you use Active Directory, you must select the Authentication required to search LDAP check box and provide the full DN and password of an account that can reach Active Directory. |
|
Admin DN |
Specify the administrator DN for queries to the LDAP directory. |
|
Password |
Specify the password for the LDAP server. |
|
Backup Admin DN |
Specify the backup administrator DN for queries to the LDAP directory, as a fallback when primary Admin DN fails (due to account expiration). The interaction with LDAP directory stops when both primary and backup administrator accounts fail. |
|
Backup Admin Password |
Specify the backup administrator password for the LDAP server. |
|
Finding user entries |
|
|
Base DN |
Specify the base DN under which the users are located. For example, dc=sales,dc=acme, dc=com. |
|
Filter |
Specify a unique variable that can be used to do a fine search in the tree. For example, samAccountname=<username> or cn=<username>. Include <username> in the filter to use the username entered on the sign-in page for the search. Specify a filter that returns 0 or 1 user DNs per user; the device uses the first DN returned if more than 1 DN is returned. |
|
Remove Domain from Windows users names? |
|
|
Strip domain from Windows username |
Select this option to pass the username without the domain name to the LDAP server. |
|
Enable Challenge-Response open protocols? |
|
|
Enable Challenge-Response open protocols |
Select this option if you want to use a challenge-response protocol for authentication. By default, these protocols are disabled for LDAP servers because account management is not possible. |
|
Determining group membership |
|
|
Base DN |
Specify the base DN to search for user groups. |
|
Filter |
Specify a unique variable which can be used to do a fine search in the tree. For example, samAccountname=<username> or cn=<GROUPNAME>. |
|
Member Attribute |
Specify all the members of a static group. For example, member or uniquemember (iPlanet specific). |
|
Reverse group search |
Select this option to start the search from the member instead of the group. This option is available only for Active Directory server types. |
|
Query Attribute |
Specify an LDAP query that returns the members of a dynamic group. For example, memberURL. |
|
Nested Group Level |
Specify how many levels within a group to search for the user. The higher the number, the longer the query time, so we recommend that you specify to perform the search no more than two levels deep. |
|
Nested Group Search |
Select one of the following options: Nested groups in Server Catalog–This option is faster because it can search within the implicit boundaries of the nested group. Search all nested groups–With this option, the device searches the Server Catalog first. If the device finds no match in the catalog, then it queries LDAP to determine if a group member is a subgroup. |
Displaying the User Accounts Table
To display user accounts:
1.Select Authentication > Auth. Servers.
2.Click the link for the authentication server you want to manage.
3.Click the Users tab to display the user accounts table.
The user accounts table includes entries for the accounts that have been created. The Last Sign-in Statistic column shows the last successful sign-in date and time for each user, the user’s IP address, and the agent or browser type and version.
4.Use the controls to search for users and manage user accounts:
•To search for a specific user, enter a username in the Show users named box and click Update.
You can use an asterisk (*) as a wildcard, where * represents any number of zero or more characters. For example, to search for all usernames that contain the letters jo, enter *jo*. The search is case-sensitive. To display the entire list of accounts again, type * or delete the field’s contents and click Update.
•To limit the number of users displayed on the page, enter a number in the Show N users box and click Update.
•To terminate the user session and delete the account, select the check box next to the user account record and click Delete.