Endpoint protection with McAfee ePolicy Orchestrator (ePO) Server
Overview
This section describes how to integrate McAfee ePO server with PPS to support endpoint protection in your network. It describes Pulse Policy Secure (PPS) integration with McAfee ePO server to assess device security posture by querying device attributes details and use them in role mapping rules to make access control decisions.
Prerequisites
This guide assumes you are familiar with the use of the following products and their related terminology.
•Pulse Policy Secure at version 9.1R8.
•McAfee ePolicy Orchestrator (ePO) server version 5.10.0 and above
Pulse Policy Secure (PPS) integration with the McAfee ePolicy Orchestrator (ePO) server provides complete visibility of network endpoints and provide end to end network security. McAfee ePO server maintains the endpoint information that it manages in its database.
The PPS integration with McAfee ePO server allows Admin to use the host property values of the endpoints managed by ePO to access device security posture. This document talks about the REST APIs exposed by McAfee ePO server, which can be used by PPS to fetch the endpoint details, attributes that are needed for accessing device security posture and also about the remote command to take remediation action on the endpoint using McAfee ePO server.
Use Cases
The following use cases are supported with PPS and McAfee ePO server integration:
1.Role Based Access Control (RBAC) for the endpoints based on the device attributes received from HTTP attribute server (McAfee ePO).
2.Periodic compliance check for the endpoint using HTTP attribute server.
3.Report the unmanaged endpoint IP address to McAfee ePO server for McAfee agent installation on the endpoint.
The authentication process is described below:
1.When endpoint tries to connect to the network, PPS authenticates the user and queries the third-party server for the endpoint device attribute values using endpoint identifier.
2.Roles are assigned based on the attribute values received from external server and user is given the corresponding access.
3.PPS periodically queries the external server for change in attribute values and assigns the role accordingly. Endpoint identifier can be IP address, MAC address, or user certificate.
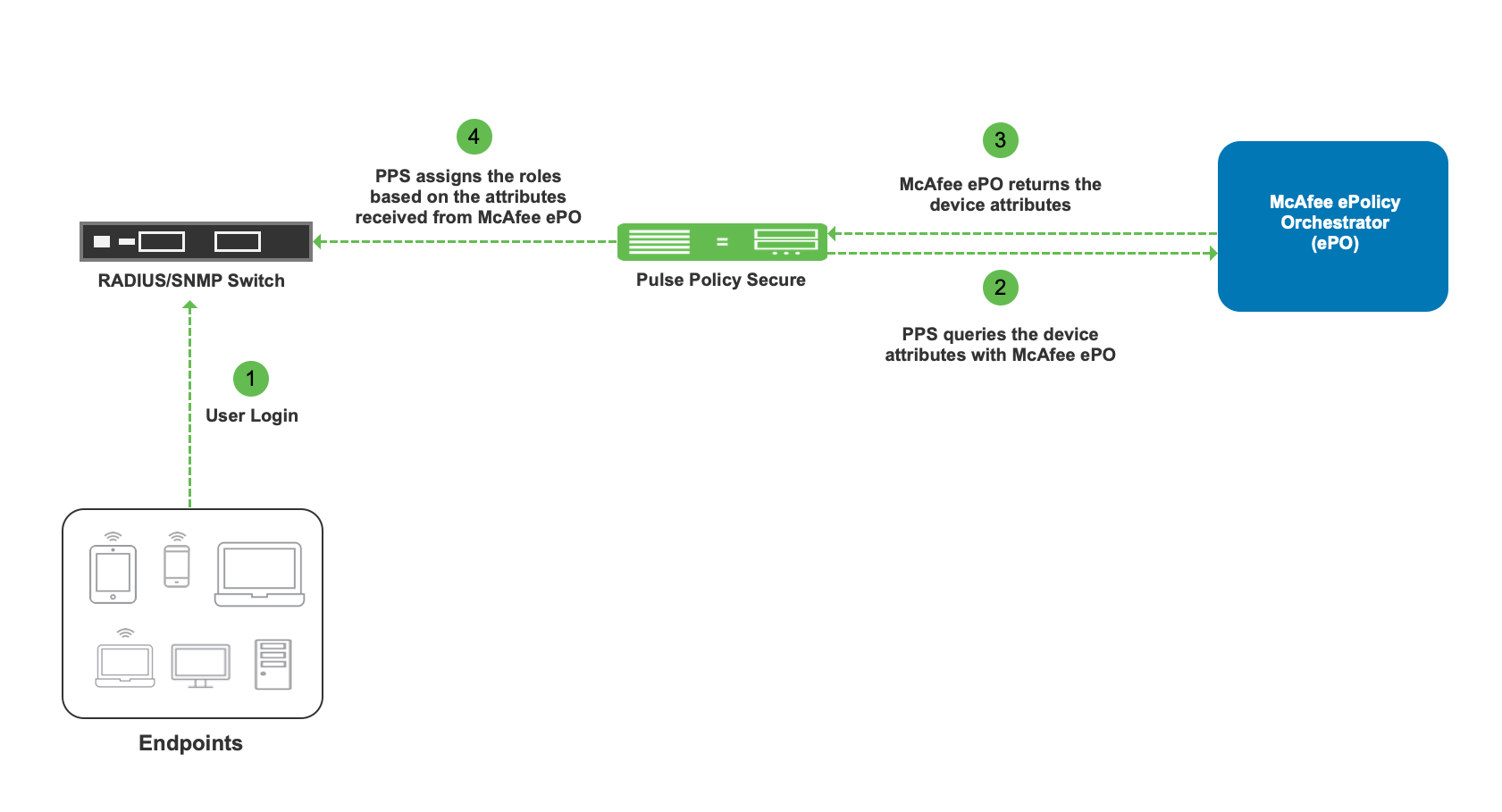
In this example, the endpoint is connected to a third-party switch. The switch has 802.1X/MAB authentication enabled. As an alternate, SNMP enforcement mechanism can also be used.