Alert-Based Admission Control with McAfee ePolicy Orchestrator (ePO)
Overview
This section describes how to integrate McAfee ePO server with PPS to support alert-based admission control in your network. It describes how to configure Pulse Policy Secure (PPS) to provide Alert-based admission control protection for your network using McAfee ePolicy Orchestrator (ePO).
Prerequisites
This guide assumes you are familiar with the use of the following products and their related terminology.
•Pulse Policy Secure at version 9.1R5.
•McAfee ePolicy Orchestrator (ePO) server version 5.9.0 and above
Pulse Policy Secure (PPS) integration with the McAfee ePolicy Orchestrator (ePO) provides complete visibility of network endpoints and provide end to end network security. The PPS integration with McAfee ePO server allows Admin to perform user access control based on alerts received from the McAfee ePO server.
If ePO detects that an endpoint on the network has become non-compliant, ePO can send PPS the non-compliant IP address and an event label. PPS resolves the event as a property on the endpoint, and can take automated actions until the endpoint is remediated and becomes compliant.
The authentication process is described below:
1.User downloads a malicious file from the Internet. The perimeter firewall scans the file and, based on user-defined policies, sends the file for analysis.
2.McAfee agent running on the Endpoint detects the malicious activity and sends the information to McAfee ePO server.
3.Based on the alert rules configured on McAfee ePO server, it generates alerts and sends automatically to PPS with the help of Pulse Policy Secure Extension.
4.McAfee ePO server sends alert to PPS to isolate the endpoint from the network. The Alert includes severity for the affected endpoint to PPS.
5.The PPS server quarantines/blocks the endpoint based on the configured Admission control policies.
McAfee ePO server receives Threat events from different Endpoint Security (ENS) modules like Firewall, Threat Intelligence Exchange (TIE)/Adaptive Threat Protection (ATP), Threat Prevention and others.
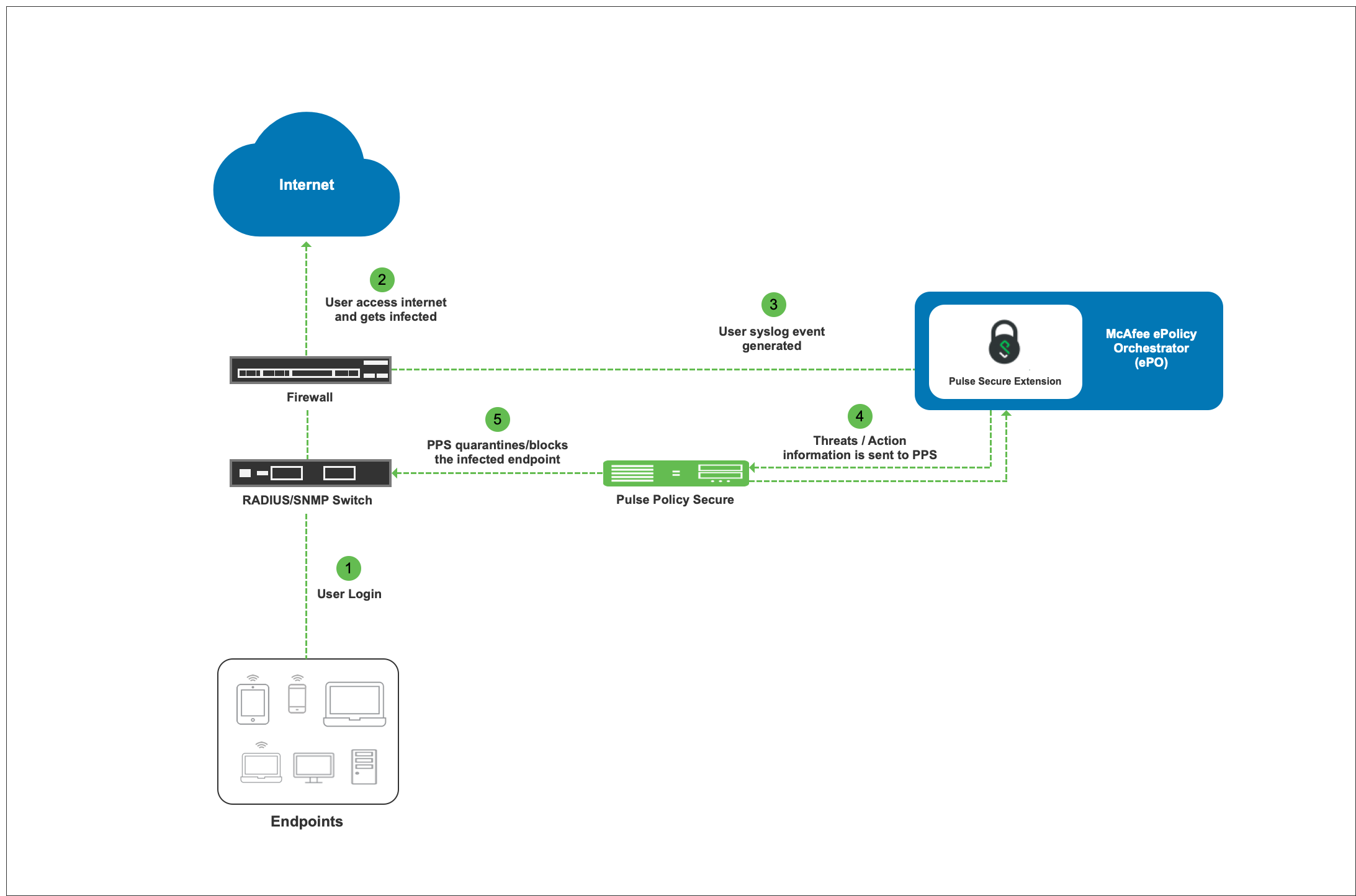
In this example, the endpoint is connected to a third-party switch. The switch has 802.1X/MAB authentication enabled. As an alternate, SNMP enforcement mechanism can also be used.