Configuring FortiGate Firewall
The FortiGate firewall detects traffic from an endpoint that matches a configured security policy using the FortiAuthenticator FSSO record. It determines the role(s) associated with that user, and allows or denies the traffic based on the actions configured in the security policy.
To configure FortiGate firewall:
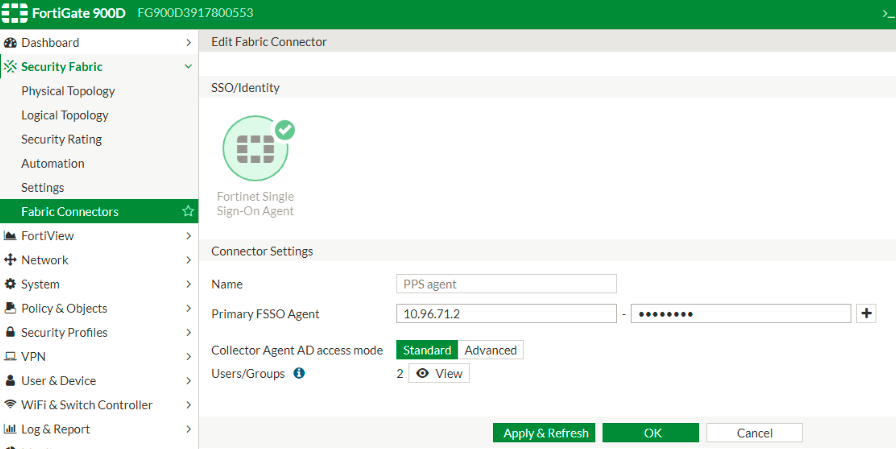
1.(Applies to Release 6.0.*) Create the FortiAuthenticator as an FSSO agent in the FortiGate Firewall. Select Fabric Connector > Create New, under SSO/Identity select Fortinet Single Sign-On Agent.
•Name: Enter a name for the entry
•Primary FSSO Agent: Enter the IP address of the FortiAuthenticator appliance, and the password* used to communicate with it.
•Click Apply & Refresh to test your configuration. If correct, the users /groups area will automatically populate
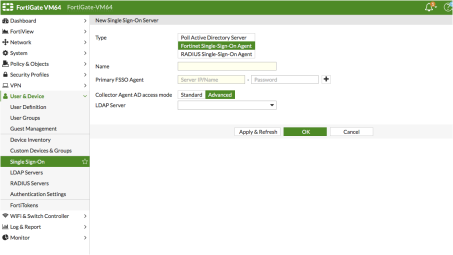
(Applies to Release 5.6.*) Create the FortiAuthenticator as an FSSO agent in the FortiGate Firewall. Select User & Device >Single Sign-On and click Create New and enter the following data.
•Type: Fortinet Single-Sign-On Agent
•Name: Enter a name for the entry
•Primary Agent IP/Name: Enter the IP address of the FortiAuthenticator appliance, and the password* used to communicate with it.
*This is the same as the secret key configured on FortiAuthenticator in the Fortinet SSO Methods > General section.
•Click Apply & Refresh to test your configuration. If correct, the users /groups area will automatically populate
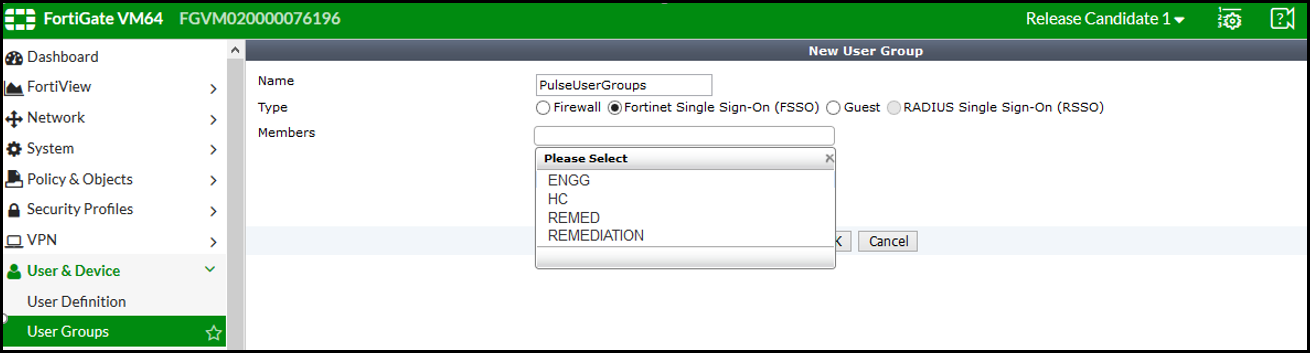
2.Create matching User groups. Select User & Device > User Groups. Click create New and enter the following data:
•Name- Enter the name of the group. This name will appear in the firewall policy.
•Type- Select Fortinet Single Sign-On as type.
•Select the matching User group created on FortiAuthenticator and Click OK.
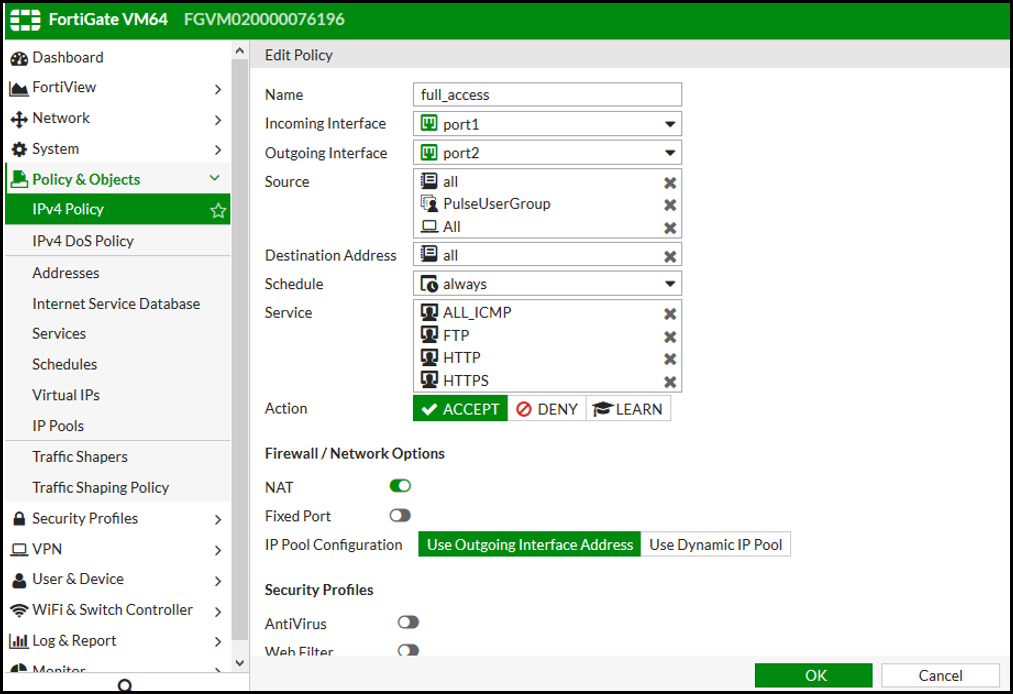
3.Create a firewall policy to use the PPS enforcement groups just created. Select Policy & Objects > IPv4 Policy. Click Create New and create the policy based on the resource access restrictions to be enforced.