Deployments using 802.1X Authentication with Native Supplicant
802.1X Authentication with Native Supplicant
Using PPS, you can provision 802.1X authentication for endpoints using native supplicant. The Layer 2 authentication and enforcement is used to control network access policies at the edge of the network using an 802.1X enabled switch or access point.
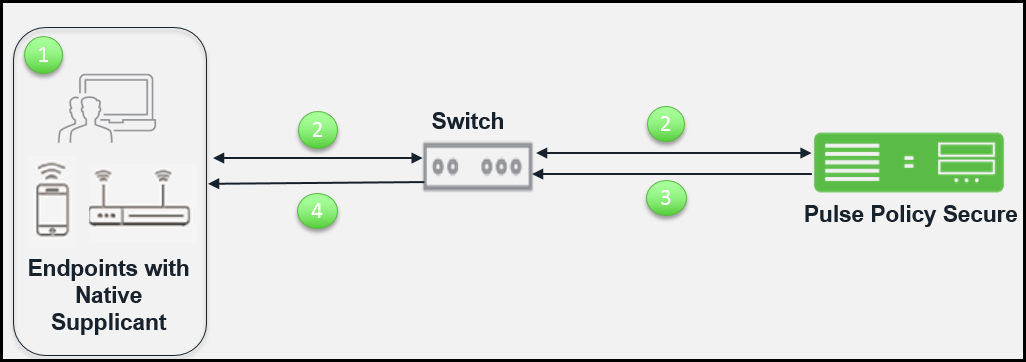
The workflow for 802.1X authentication with native supplicant is described below:
1.Configure the endpoints protocols from the Adapter settings as per the PPS configured protocols. Once the client adapter is online the authentication starts automatically.
2.Switch receives the request and starts RADIUS authentication with PPS. The user is prompted for user credentials.
3.PPS assigns the roles based on the credentials provided by the user. PPS communicates the enforcement rules to switch in form of RADIUS return attributes (For example, Change of VLAN) for the authenticated user.
4.Switch provides access and IP address to the endpoints based on the RADIUS return attributes.
Agentless Host Checking with Native Supplicant
As many users bring their own devices, additional intelligence must be applied to eliminate intrusions and protect sensitive information. The IT administrators need the ability to control where devices are allowed on the network, based on the device type, operating system, owner of the device and user log in credentials of the device. The network resource request must be handled appropriately and appropriate action must be taken for any violation, which includes limiting access to internet only.
The PPS solution provides endpoint compliance for BYOD devices for providing seamless access to protected resources with native supplicant. For example, enterprise users need to provide onsite access to employees and contractors. To provide network access, the BYOD devices from contractor must be compliant to host checker security policies. For such users, you can use 802.1X authentication using native supplicant and then endpoint compliance check is achieved using a web browser. A single session is created for both the connections and a single license is consumed.
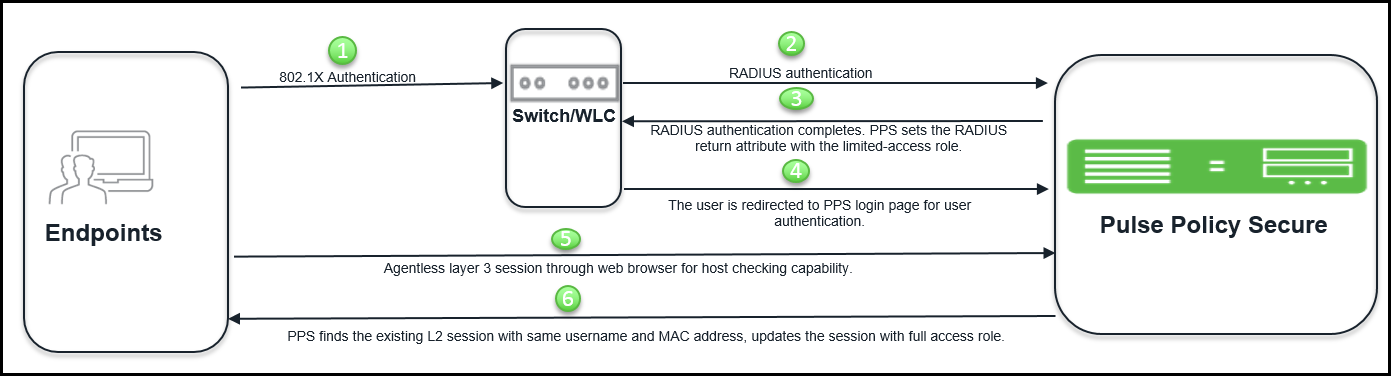
The workflow is described below:
1.The contractor user connects to network, performs layer 2 authentication using AD credentials. For 802.1X, AD username and password is used for authentication. For MAC authentication, endpoints MAC address or device attributes for profiler is used for authentication.
2.The endpoint host check is not performed and hence the user gets limited connectivity. The user must be compliant to host check security policy for full access.
3.PPS sets the RADIUS return attribute with limited access role. Limited access role is applied on the endpoint.
4.The user is redirected to a PPS log in page for user authentication.
5.The user opens the web browser and enters the AD username and password. The agentless Host Checker provides the compliance details to PPS.
6.PPS finds the existing session with the same username and MAC address and then updates the session with full access role.
The user gets the required full access to protected resources if the system is compliant to HC security policies.
- The user can choose to remember the username and password to avoid entering it multiple times for layer 2 and layer 3 connections.
- This feature is supported for Windows and MAC OSX.
- For configuration, see Configuring Agentless Host Checking with Native Supplicant .
Host Checking with Native Supplicant
On Mac OSX, Windows, and Linux endpoint using native supplicant, PPS Host checking can be enforced only for Layer 3 connection. Once the endpoint gets authenticated using native supplicant and gains network access, you can launch and install Pulse Secure client using web browser deployment or SCCM advertisement to establish a Layer 3 session. This evaluates the health status of the endpoints and thereby ensuring legitimate resource access behind PPS Enforcer.
There will be only one session for Layer 2 and Layer 3 connections on PPS which will consume single license.
For agentless host checking, native supplicant is used to perform 802.1x authentication. The compliance check is performed using browser based agentless L3 session. The L2 and agentless L3 session are bridged on PPS to provide compliance based layer 2 access control. For access control, RADIUS return attribute Filter-ID with Radius COA is used.
The Host Checker functionality is not supported on the native Mozilla browser on MAC OSX. As a workaround disable the Captive Network Assistant feature, which is enabled by default or open the Pulse Secure client using a different web browser.
Using Native Supplicant the Host Checker functionality is not supported. This is possible through Configuring Agentless Host Checking with Native Supplicant .
Agentless Session Bridging requires Host Checker functionality to be executed on Linux via JAVA NPAPI plugin, which is only supported on Firefox ESR browser with v52.0 and lower.