Enabling Granular Cipher Selection for Setting the Security Options
Granular cipher selection provides an administrator the ability to select specific ciphers and the preferred ordering of the selected ciphers. This feature also provides presets like Suite-B and PFS. There are two tabs, Inbound OpenSSL options and Outbound OpenSSL options. With this feature the administrator can select the ciphers that TLS/SSL connections will use. The Inbound OpenSSL options apply to all incoming connections. Outbound OpenSSL options apply to the following services:
•SCEP
•Syslog
•LDAPS
•Start TLS
FIPS Mode Settings is common for both Inbound and Outbound SSL Options.
A common cipher library has been added which can be used by both, the inbound and outbound connections. The outbound options are listed in a separate tab next to the inbound settings. The outbound settings have presets for High and Medium ciphers along with custom options. There is no PFS or SuiteB presets on the outbound side. From 5.3R3 release onwards, support for preset Low has been removed and the same can be configured using Custom SSL Cipher Selection option. For the SuiteB preset to work, PPS should have ECC Device Certificate mapped to Internal or External Port. SuiteB preset does not work if the ECC Device Certificate is mapped only to virtual port.
Enabling Inbound SSL Options
Only when FIPS mode is turned on, the FIPS compliant ciphers are available to be chosen from the Supported Ciphers panel. FIPS mode is editable only on the inbound option page.
To set the security options with Inbound SSL options:
1.In the admin console, select System > Configuration > Security > Inbound SSL Options.
2.Under Allowed Encryption Strength choose Custom SSL Cipher Selection.
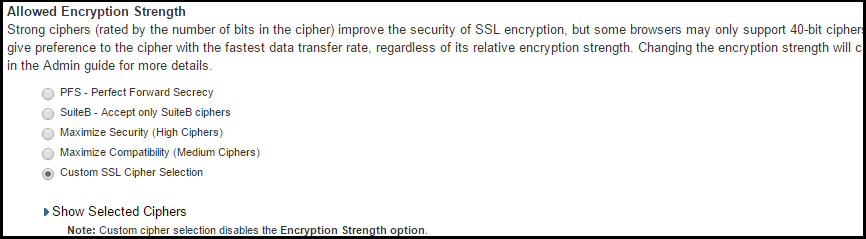
•The two panels of Supported Ciphers and Selected Ciphers are displayed. Supported ciphers has the entire list of ciphers supported for the selected SSL or TLS version. Selected ciphers list the currently selected ciphers list. The below figure shows the two panels (Supported Ciphers and Selected Ciphers). Note that the Selected Ciphers and Supported Ciphers List will also be displayed for all Preset like PFS or SuiteB or Medium or High.

1.For adding a cipher, click the cipher string on the left panel and then click Add or double click the cipher name in the left panel.
2.To remove the cipher, click the cipher name on the right panel and then click Remove or double click on the cipher name on the right side.
3.The selected ciphers on the right are listed in order of their priority from top to bottom. To change the priority of the ciphers, click on the cipher name and then click on Move Up to increase priority or the Move Down button to decrease the priority.
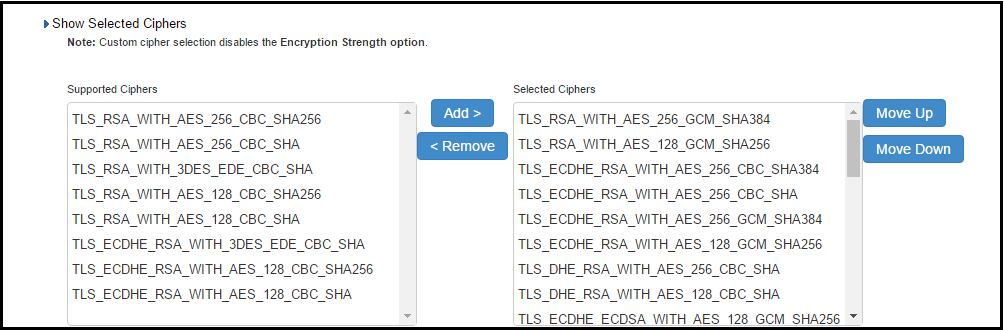
A list of the custom ciphers to be used on the device’s port is displayed in the order the web server will select them. Note that Suite B ciphers are listed on top. End users who now log in to external virtual port p_ecdsa256 must have at least one of the listed ciphers installed on their browser or else they cannot log in to the server.
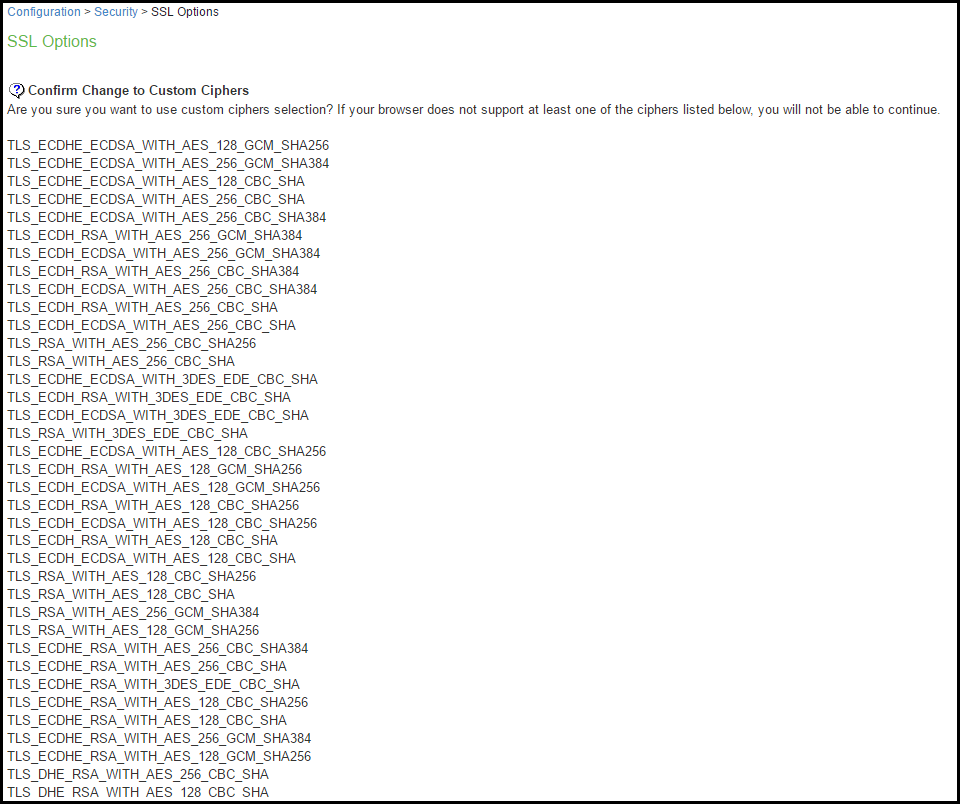
4.Click Change Allowed Encryption Strength.
When custom ciphers are selected, there is a possibility that some ciphers are not supported by the web browser. Also, if any of ECDH/ECDSA ciphers are selected, they require ECC certificate to be mapped to the internal/external interface. If ECC certificate is not installed, administrator may not be able to log in to the box. The only way to recover from this situation is to connect to the system console and select option 8 to reset the SSL settings from the console menu. Option 8 resets the SSL settings to its default. So, the previously set SSL settings are lost. This is applicable only to Inbound SSL settings.
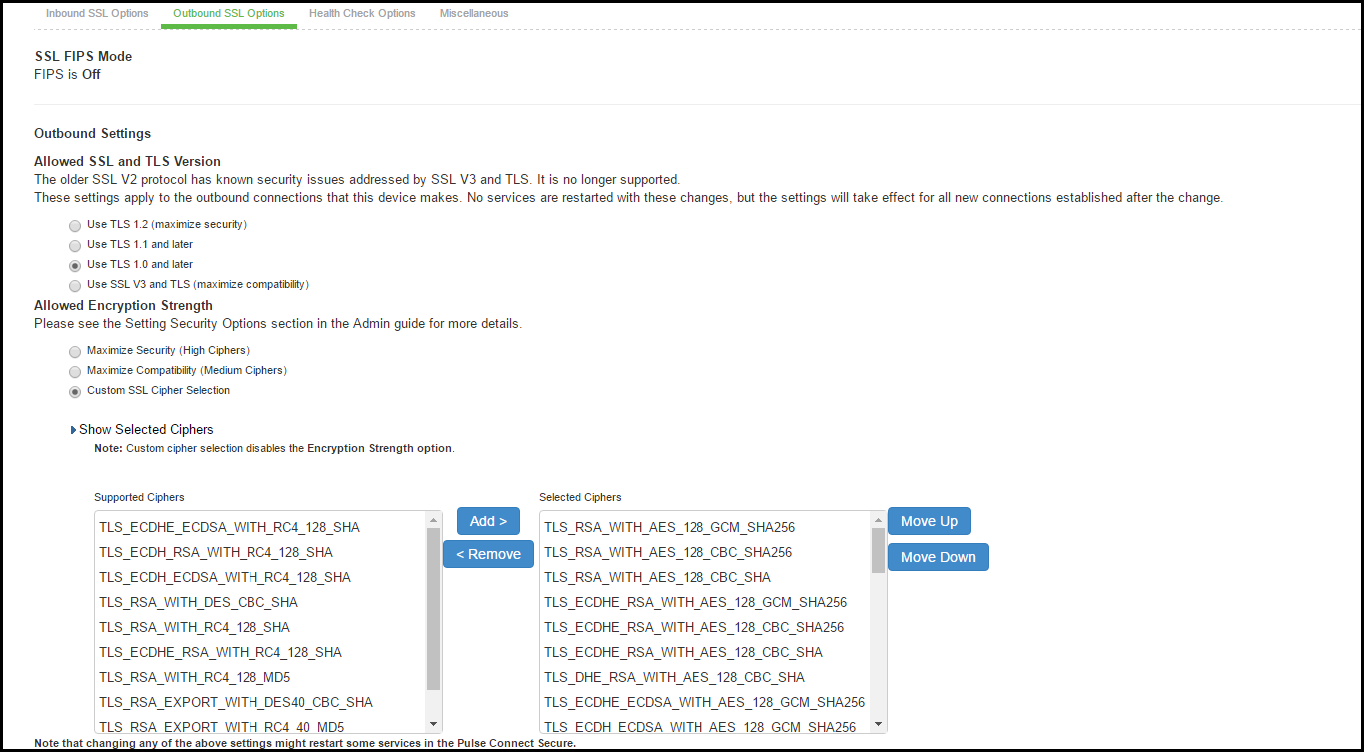
Enabling Outbound SSL Options
We can configure non FIPS ciphers only for Outbound SSL Settings using Custom Cipher Selection option. There are options to change different SSL/TLS versions and different encryptions in the Outbound SSL Settings. The below figure shows the Outbound SSL Settings
|
Settings |
Guidelines |
|
SSL FIPS Mode option |
Turn on FIPS mode— Select this option to enable FIPS mode. |
|
Allowed SSL and TLS Version |
Specify encryption requirements for clients. By default, the system requires SSL version 3 and TLS. The system honors this setting for all Web server traffic and all types of clients. You can require users who have older browsers that use SSL version 2 to update their browsers, or you can change this setting to allow SSL version 3, and TLS. |
|
Allowed Encryption Strength |
•Accept only 168-bit and greater — If you select this option the system gives preference to 256-bit AES over 3DES. •Accept only 128-bit and greater — (Default) If you select this option the system gives preference to RC4 ciphers. You can require users to have this level of encryption strength or change this default to an option compatible with the user base. • Accept 40-bit and greater — If you select this option the system gives preference to RC4 ciphers. Older browsers that predate the change in the U.S. export law in year 2000 that required 40-bit cipher encryption for international export, can still use 40-bit encryption. •Custom SSL Cipher Selection — Specify a combination of cipher suites for the incoming connection from the user’s browser. If you select the AES/3DES option, the system gives preference to 256-bit AES over 3DES. When using 168-bit encryption, some Web browsers may still show 128-bit encryption (the gold lock on the browser status bar) even though the connection is 168-bit. This is typically a limitation of the browser’s capability. |
|
Encryption Strength option |
The allowed encryption strength is enforced after an SSL session is established, so that a user connecting with a disallowed encryption strength receives a Web page describing the problem. Enable this option to prevent a browser with a weak cipher from establishing a connection. |
|
SSL Handshake Timeout option |
Determines the time elapse before the SSL handshake timeout. The default is 60 seconds. |
|
SSL Legacy Renegotiation Support option |
SSL and Transport Layer Security (TLS) renegotiations can be subjected to man-in-the-middle (MITM) attacks that can lead to abuse. A new TLS extension (defined in RFC 5746) ties renegotiations to the TLS connections they are being performed over to prevent these kinds of attacks. The SSL Legacy Renegotiation Support option is enabled by default and allows renegotiation between clients and servers even if they do not support the new TLS extension. Disable this option to not allow renegotiations between clients and servers that do not support the new TLS extension. A web server restart is required when you change the value of this option. |