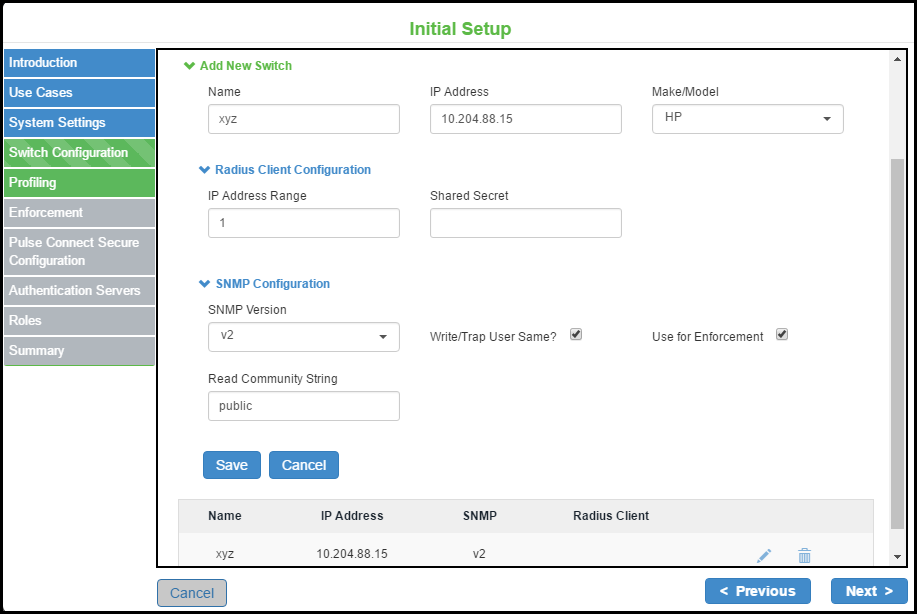
Step 3: Configuring Layer 2 Enforcement
Layer 2 enforcement means controlling network access at the point where the user attaches to the network. In a wired network, this control is at the switch port; in a wireless network the control is at the wireless access point. The network access control is accomplished through 802.1X authentication protocol (implemented on the switch or wireless AP) in conjunction with RADIUS return attributes to control switch or AP operation such as VLAN assignment and filtering.
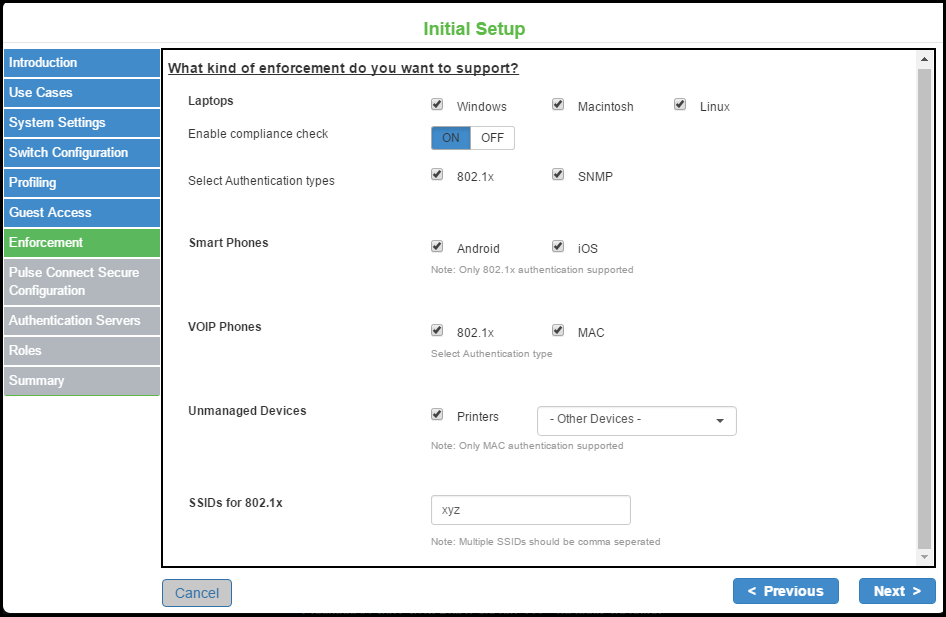
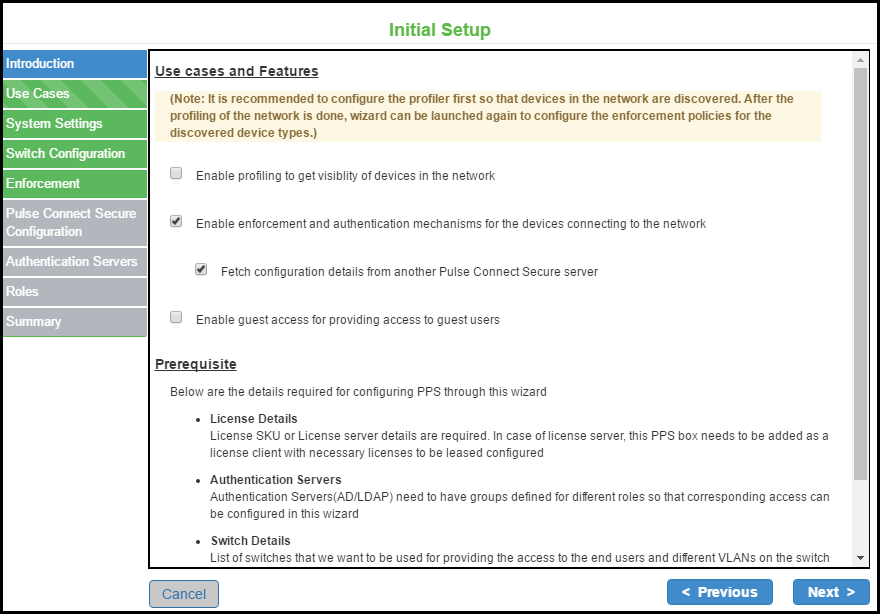
The following enforcements are supported for the devices connecting to the network.
•802.1X
•MAC Authentication
•SNMP
Profiling is enabled by default when you enable enforcement and authentication.
Configure the enforcement for devices, which includes laptops, smart phones, VOIP phones, and unmanaged devices.
If profiling is enabled the device platform types are automatically enabled.
|
Device Type |
Platforms |
Authentication Type |
Additional Support |
|---|---|---|---|
|
Laptops |
•Windows •MAC •Linux |
•802.1X •SNMP |
Host Checker |
|
Smart phones |
•Android •iOS |
802.1X |
NA |
|
VOIP phones |
NA |
•802.1X •MAC |
NA |
|
Unmanaged devices |
NA |
MAC |
NA |