Alert-Based Admission Control with Check Point
This section describes how to integrate Check Point Next Generation Firewall with PPS to support Alert-based admission control in your network.
Configuring Pulse Policy Secure
This section describes the integration of PPS with Check Point Next Generation firewall. PPS integrates with Check Point’s syslog notification mechanism to receive the threat alert information from Check Point and takes an action based on the admin configured policies.
To view and add the admission control templates:
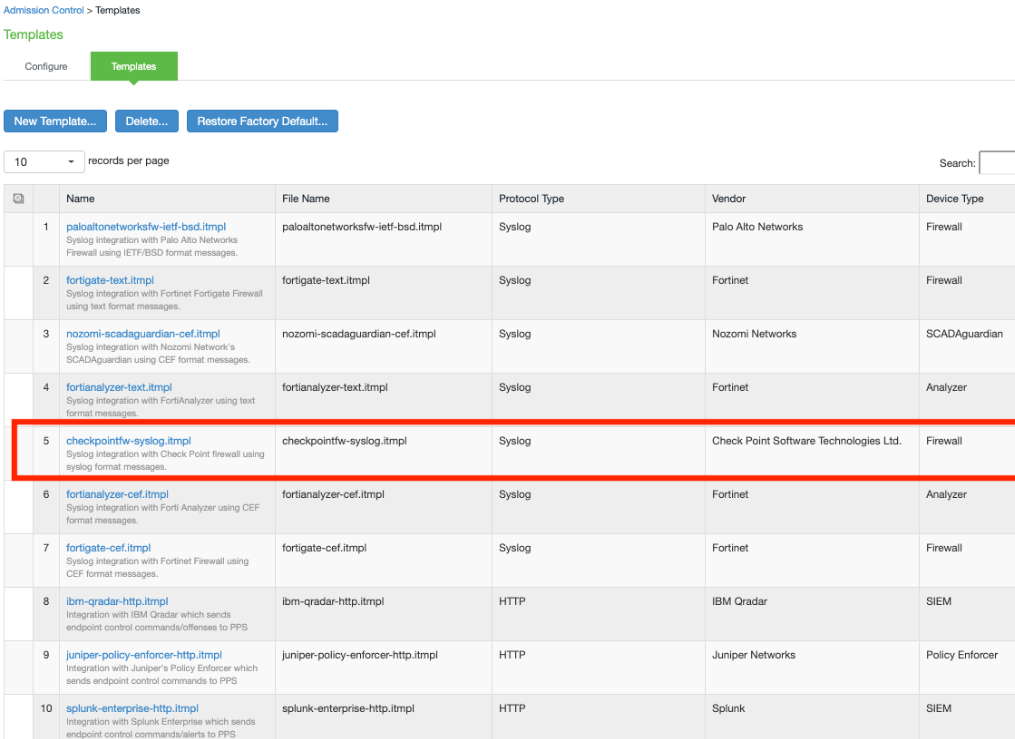
1.Select Endpoint Policy > Admission Control > Templates.
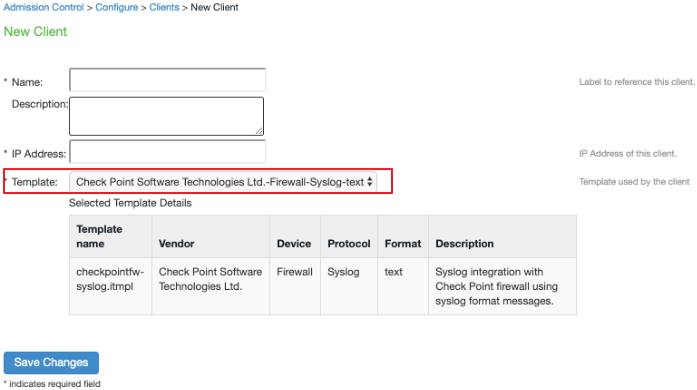
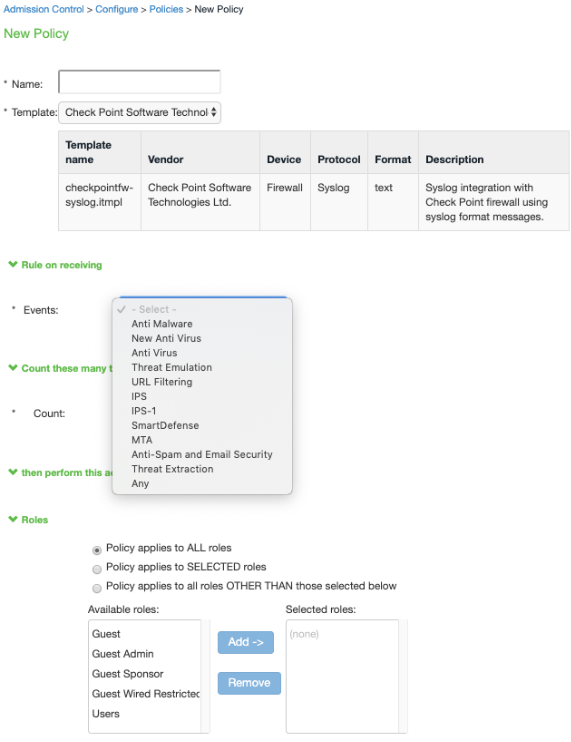
2.Select Endpoint Policy > Admission Control > Clients, choose Check Point Software Technologies Ltd-Firewall-Syslog-text as template during the template creation.
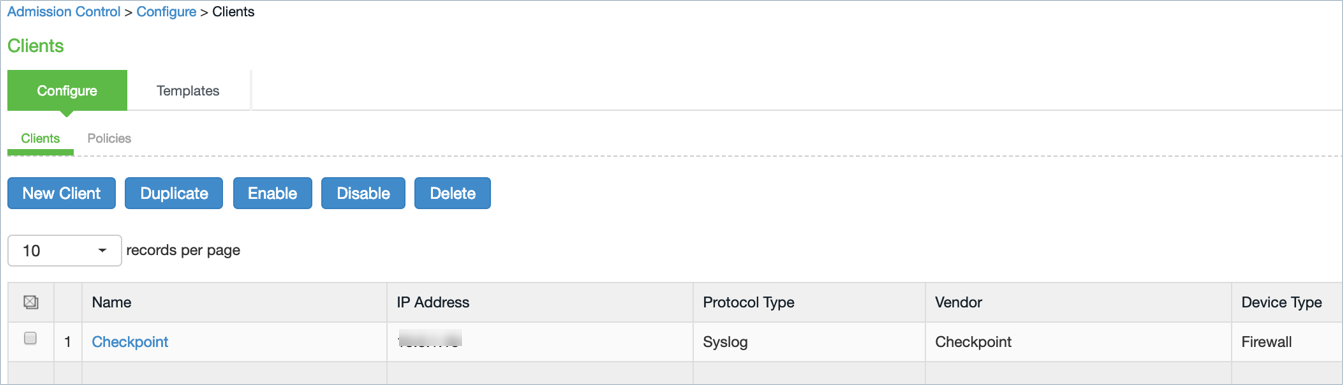
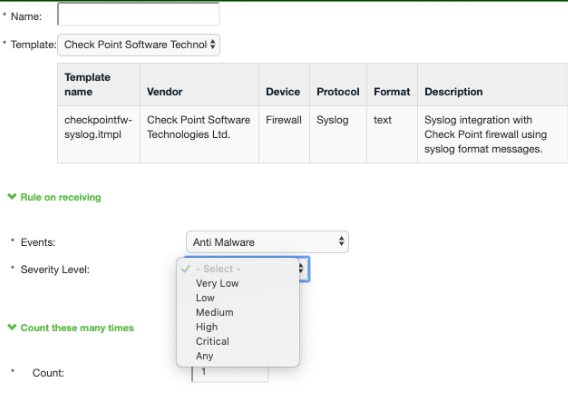
3.Select the new template during policy creation (Endpoint Policy > Admission Control > Policies). Events and severities are populated based on the template.
Configuring Check Point Firewall
The PPS device must be added as a syslog server while configuring the Check Point firewall for sending the logging information. You must add Check Point firewall as syslog client on PPS.
cp_log_export add name <name> [domain-server <domain-server>] target-server <target-server IP address> target-port <target-port> protocol <(udp|tcp)> format <(syslog)|(cef)|(splunk)(generic)> [optional arguments]
cp_log_export add name pulse target-server 10.0.1.9 target-port 514 protocol udp format syslog
cp_log_export set name <name> filter-blade-in "value2”
One predefined family for "product" field (filter-blade-in):
TP for exporting only Threat Prevention logs (Anti-Bot,Anti-Exploit,Anti-Malware,Anti-Ransomware,Capsule Docs,Endpoint Compliance,Forensics,Full disc encryption,Media Encryption & Port Protection,Secure Client,Threat emulation,Threat extraction,Zero Phishing).
cp_log_export set name pulse filter-blade-in ”TP”
For exporting Check Point logs over syslog, see Log Exporter.
Troubleshooting
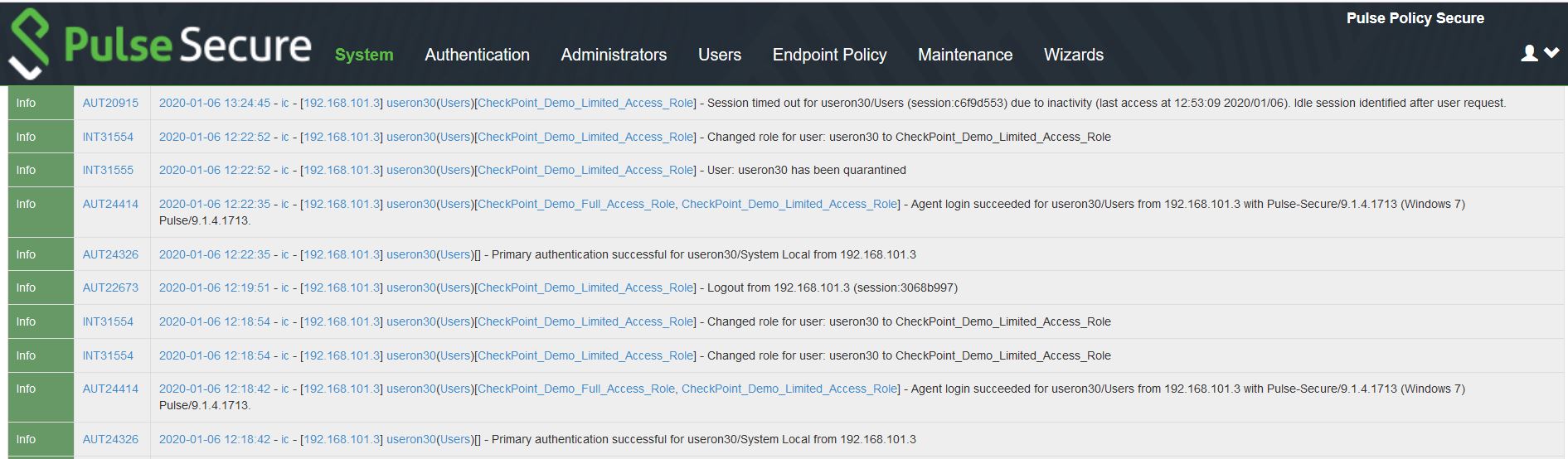
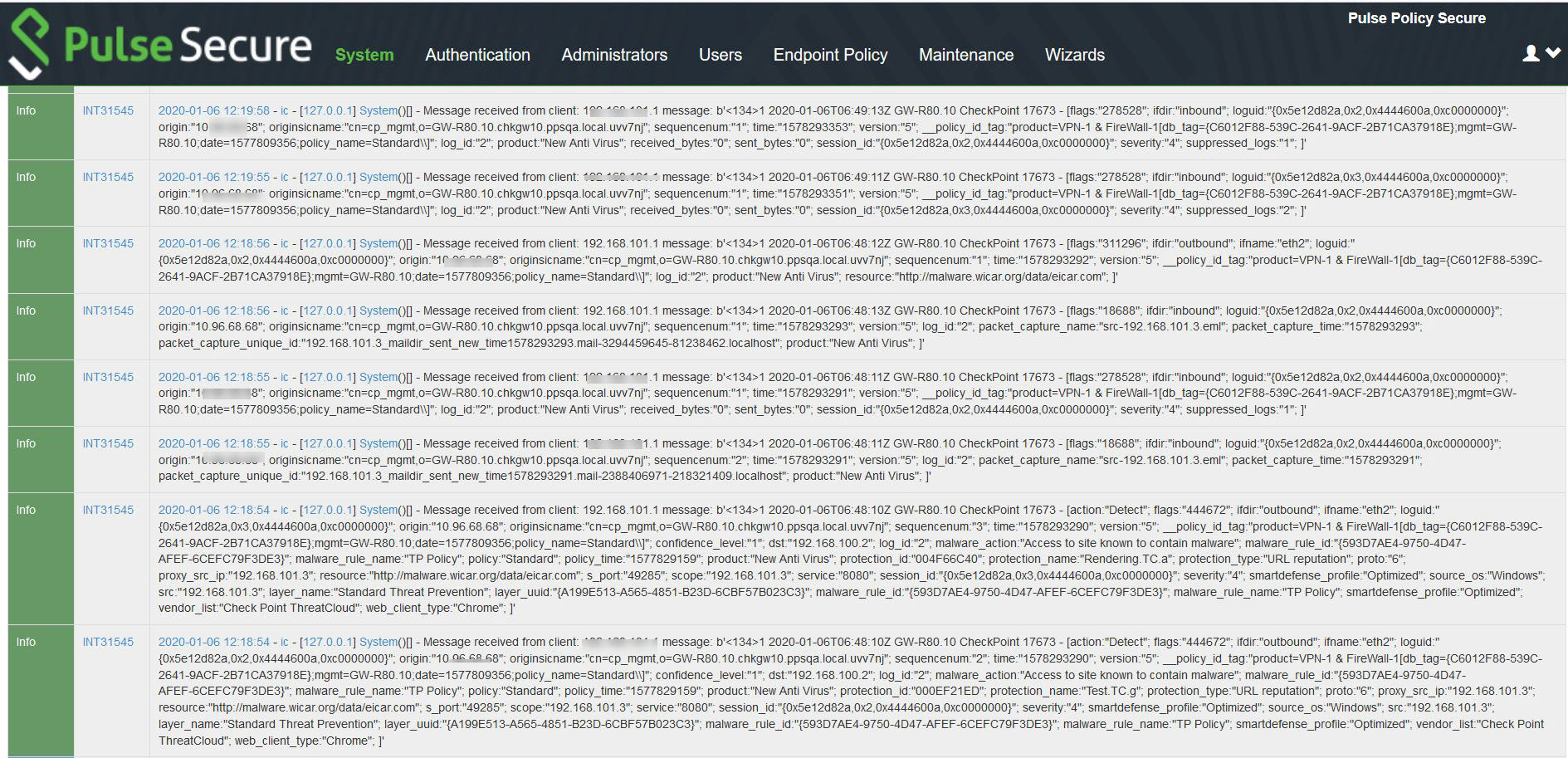
To verify the event logs on PPS, select System > Log/Monitoring > Event. Ensure Admission control events option is enabled in Event logs settings.
You can verify that the event logs are generated every time when an event is received from Check Point.
To verify the user access logs, select System >Logs & Monitoring > User Access to verify the user login related logs.