Pulse Policy Secure Syslog Add-On for Splunk
Pulse Policy Secure is a network and application access control (NAC) solution used extensively in small, midrange and large enterprises. PPS provides the capability to send various kinds of user access, device/user authentication, Host Checker compliance events, admission control events, profiler discovery, device profile, attribute update and device contextual information as Syslog messages to any Syslog receiver.
Splunk is a log management/SIEM solution that can receive Syslog messages from multiple sources. These messages are stored within Splunk and then can be correlated, searched, analyzed and displayed using its graphical user interface.
Splunk is also a platform that runs applications (Apps) as add-ons to Splunk, which are customized for specific external applications or products which send Syslogs. The App provides visualization of the received data without requiring the user to run complex searches within Splunk.
These apps typically consist of a number of dashboard elements like charts, tables and graphs that are accessible via a menu structure contained within the app, which are based on pre-defined searches. The PPS Splunk App is such an App developed by Pulse Secure for visualizing a Syslog feed from Pulse Policy Secure.
To integrate PPS with Splunk, perform the following:
Configuring PPS to send syslogs to Splunk
Add an instance of Splunk to PPS as syslog server. Add the Splunk IP address or hostname and port number at the appropriate place in the PPS administrative interface.
T o configure Splunk as a Syslog server:
1.Under Log/Monitoring > <User Access/Events/Admin Access>.
2.Click Log Settings.
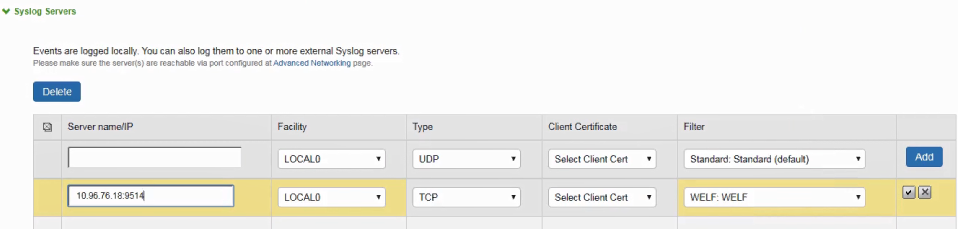
3.Under Syslog Servers, Enter the Splunk Server name/IP and add port value as 9514.
The port number can be customized from the inputs.conf file if desired.
4.Select the type as TCP.
5.Select the file format as WELF. Only WELF is supported.
6.Click Add.