Alert-Based Admission Control with Splunk Enterprise
Overview
Pulse Policy Secure (PPS) integration with the Splunk Enterprise provides complete visibility of network endpoints, including unmanaged endpoints and provide end to end network security. The PPS integration with Splunk integration allows Admin to perform user access control based on alerts received from the Splunk.
Splunk Enterprise receives log or threat information from various log sources such as Palo Alto Network firewall. Based on these logs/alerts a search query is created on Splunk to trigger alerts to PPS. PPS takes action on user session by blocking or quarantining the user.
The authentication process is described below:
1.User downloads a file from the Internet. The perimeter firewall scans the file and, based on user-defined policies, sends the file for analysis.
2.Firewall detects that the file contains malware and a threat alert sylog gets generated and sent to Splunk Enterprise.
3.Based on the alert rules configured on Splunk. It generates alerts and this has to be manually sent to PPS with the help of Pulse Policy Secure App.
4.The Alert includes severity for the affected endpoint to PPS.
5.The PPS server quarantines/blocks the endpoint based on the configured Admission control policies.
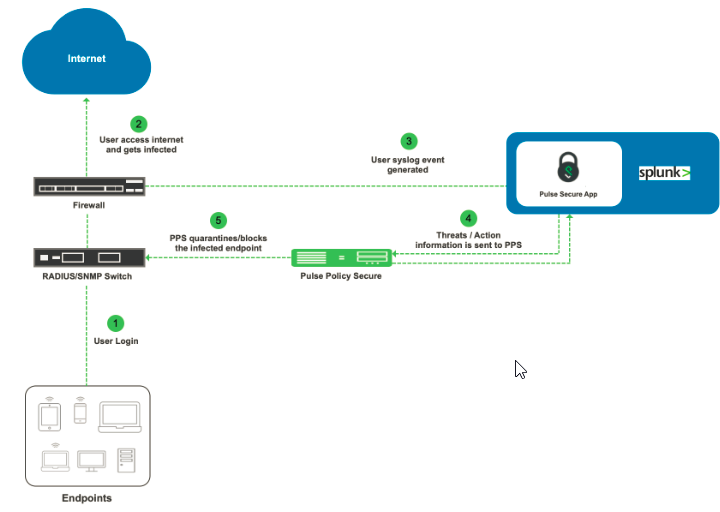
In this example, the endpoint is connected to a third-party switch. The switch has 802.1X/MAB authentication enabled. As an alternate, SNMP enforcement mechanism can also be used.